hayabusa v2.13 releases: Windows event log fast forensics timeline generator and threat hunting tool
Hayabusa
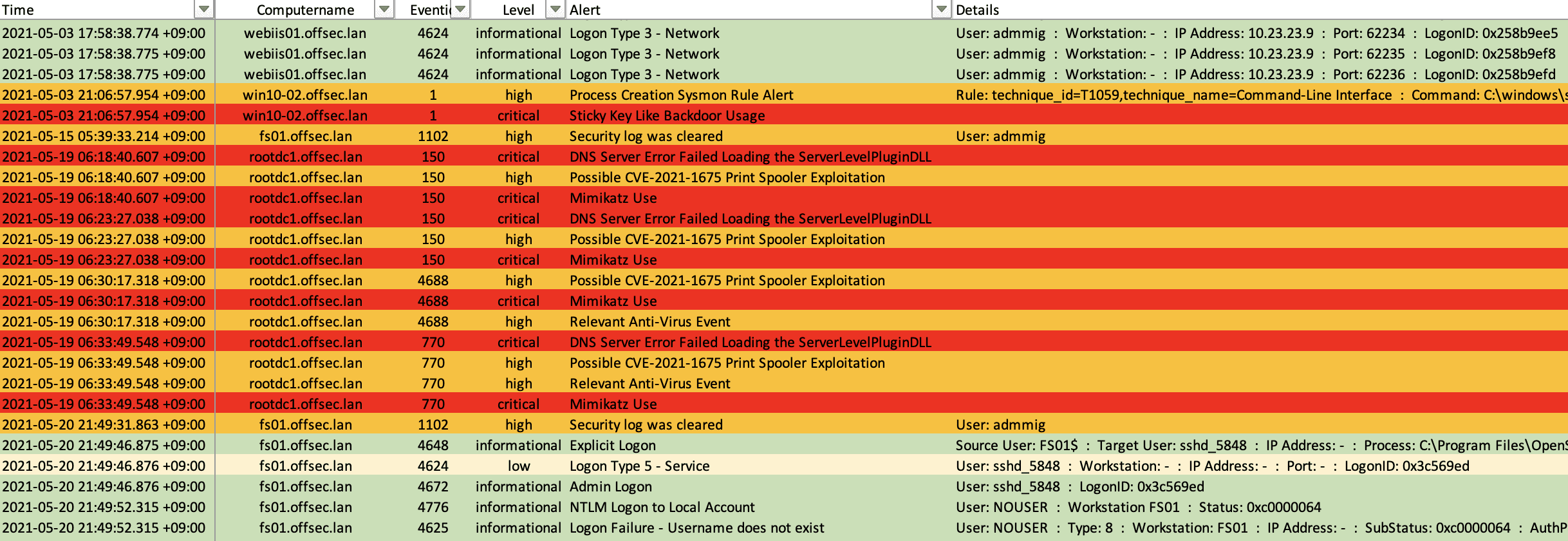
Hayabusa is a Windows event log fast forensics timeline generator and threat hunting tool created by the Yamato Security group in Japan. Hayabusa means “peregrine falcon” in Japanese and was chosen as peregrine falcons are the fastest animal in the world, great at hunting, and highly trainable. It is written in Rust and supports multi-threading in order to be as fast as possible. We have provided a tool to convert sigma rules into hayabusa rule format. The hayabusa detection rules, like sigma, are also written in YML in order to be as easily customizable and extensible as possible. It can be run either on running systems for live analysis or by gathering logs from multiple systems for offline analysis. (At the moment, it does not support real-time alerting or periodic scans.) The output will be consolidated into a single CSV timeline for easy analysis in Excel or Timeline Explorer.

Analysis in Excel
Main goals
Threat hunting
Hayabusa currently has over 1000 sigma rules and around 50 hayabusa rules with more rules being added regularly. The ultimate goal is to be able to push out hayabusa agents to all Windows endpoints after an incident or for periodic threat hunting and have them alert back to a central server.
Fast forensics timeline generation
Windows event log analysis has traditionally been a very long and tedious process because Windows event logs are 1) in a data format that is hard to analyze and 2) the majority of data is noise and not useful for investigations. Hayabusa’s main goal is to extract out only useful data and present it in an easy-to-read format that is usable not only by professionally trained analysts but any Windows system administrator. Hayabusa is not intended to be a replacement for tools like Evtx Explorer or Event Log Explorer for more deep-dive analysis but is intended for letting analysts get 80% of their work done in 20% of the time.
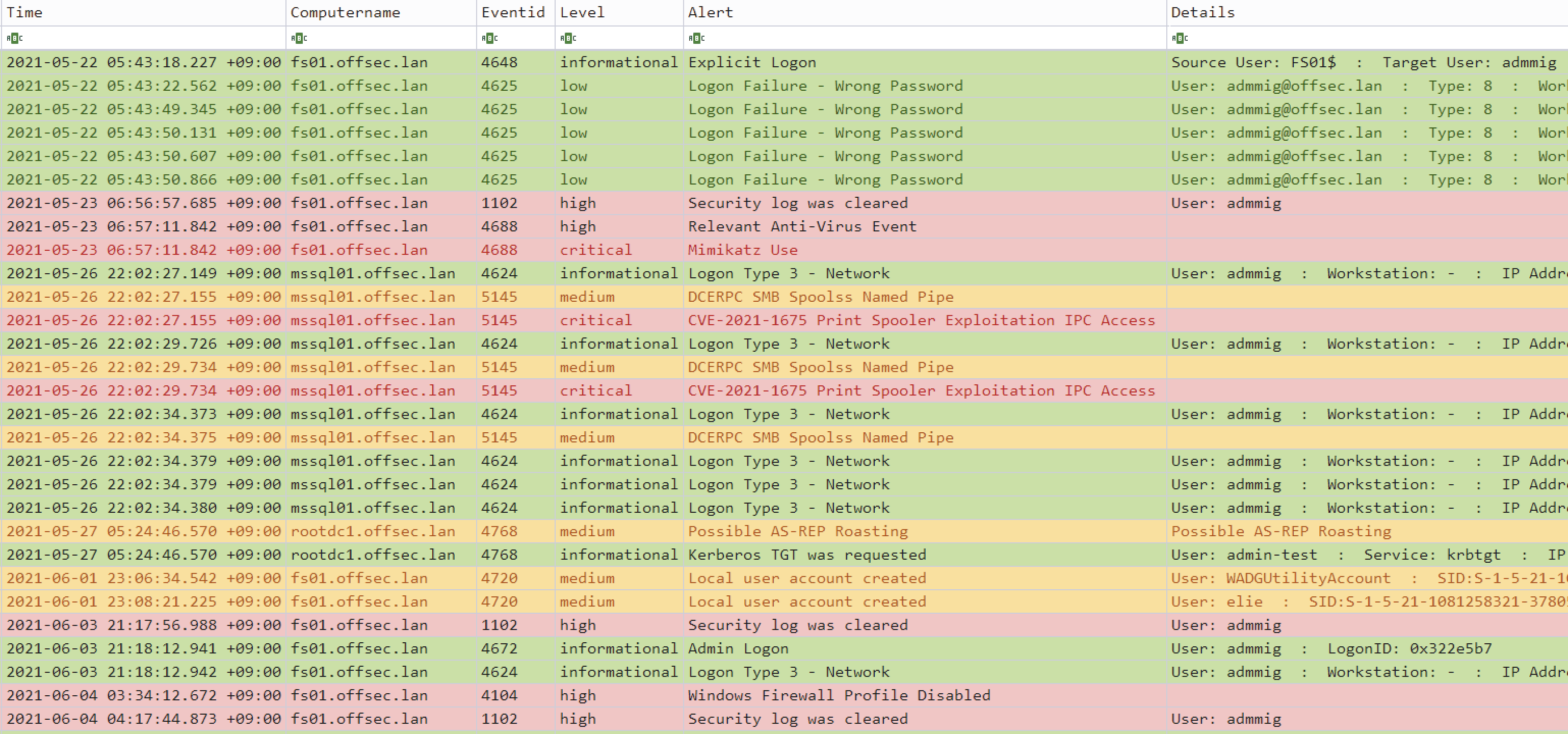
Analysis in Timeline Explorer
Features
- Cross-platform support: Windows, Linux, macOS
- Developed in Rust to be memory safe and faster than a hayabusa falcon!
- Multi-thread support delivering up to a 5x speed improvement!
- Creates a single easy-to-analyze CSV timeline for forensic investigations and incident response
- Threat hunting based on IoC signatures written in easy to read/create/edit YML based hayabusa rules
- Sigma rule support to convert sigma rules to hayabusa rules
- Currently, it supports the most sigma rules compared to other similar tools and even supports count rules
- Event log statistics (Useful for getting a picture of what types of events there are and for tuning your log settings)
- Rule tuning configuration by excluding bad rules or noisy rules
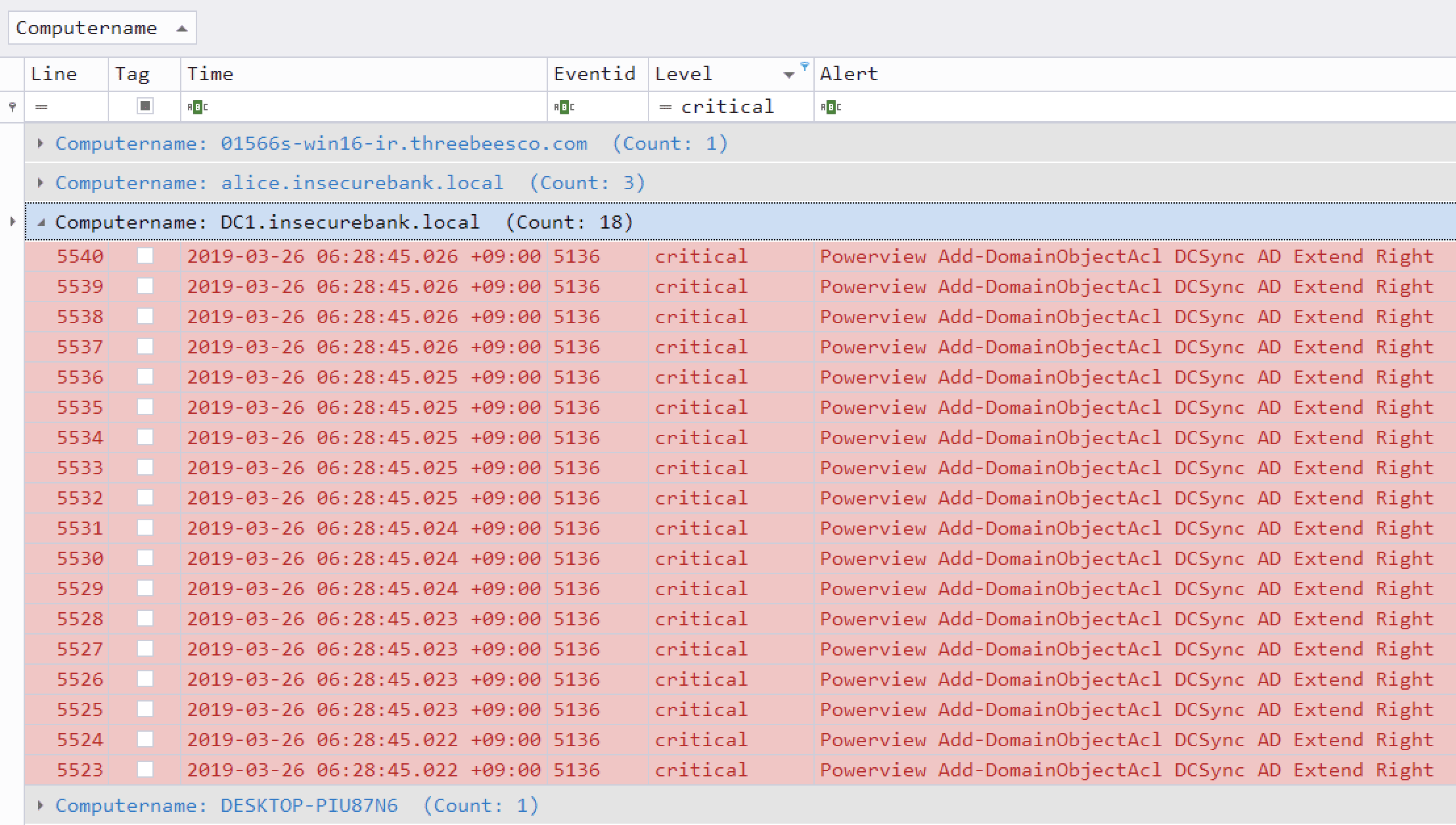
Critical alert filtering and computer grouping in Timeline Explorer
Changelog v2.13
Enhancements:
- Adjusted the
searchcommand’s Filter option to be an exact match and support wildcard characters. (#1240) (@hitenkoku) - Any time there is a change in a detection rule, it will be displayed when running the
update-rulescommand. Previously, only rules that updated theirmodifiedfield would be displayed. (#1243) (@hitenkoku) - The
json-timelinecommand now outputs in JSON format when outputting to the terminal. (#1197) (@hitenkoku) - Added support for parsing JSON input when the data is inside an array. (#1248) (@hitenkoku)
- Changed the
‖separator into a·separator to make it easier to read and render properly on older terminals. (#1258) (@YamatoSecurity) - Added a
-h, --helpoption to General Options for all commands. (#1255) (@hitenkoku) - Changed the
Detailsoutput in thejson-timelinecommand from alphabetical order to the original order. - Loading detection rules is now skipped when running commands that do not need them. (#1263) (@hitenkoku)
- Improved the standard output colors in the
csv-timelinecommand. (#1271) (@hitenkoku) - Refactoring and performance enhancements. (#1268, #1260) (@hach1yon)
Bug Fixes:
- Removed newline characters in the
searchcommand output. (#1253) (@hitenkoku) - Fixed the progress bar and wizard colored output when the
--no-coloroption is used. (#1256) (@hitenkoku) - Fixed a panic when the local timezone was not able to be identified. This was fixed in the
chronocrate version 0.4.32. (#1273)
Download & Use
Copyright (C) 2021 Yamato-Security





