Health application PumpUp server puts 6 million users information at risk
According to ZDNet report, PumpUp in Ontario, Canada, issued a statement last week that its social health tracking application under the same name inadvertently exposed the user’s privacy and sensitive data, including health information and private messages sent between users.
PumpUp describes itself as a health and fitness community. Its developed social health tracking application PumpUp supports Android and iOS platforms and claims to have more than 6 million users worldwide. With this app, users can share selfies and health tips, formulate and save custom workout plans, and get advice from fitness trainers and other users. On the other hand, it can also be used to track user activity such as calories burned, exercise time, exercise progress, etc.
All of this data is stored on a core back-end server and hosted on Amazon’s cloud. However, security researcher Oliver Hough found that the server did not set a password, which allows anyone to see who is logged in, who is sending messages in real time, and the content of the message.
According to the contents of PumpUp’s statement, the server is used to act as a messaging agent and is responsible for sending user requests and private messages to other PumpUp application users. The agent uses the little-known MQTT protocol and is often used by developers for communication between IoT devices and mobile applications.
At the same time, this protocol is also a low-bandwidth protocol, which can reduce server costs and data overhead. But because it is also a temporary agreement, it allows anyone to view real-time data streams instead of accessing large, centralized data stores. This means that whenever a user sends a message to another user, the PumpUp application will reveal the user’s profile and session message content.
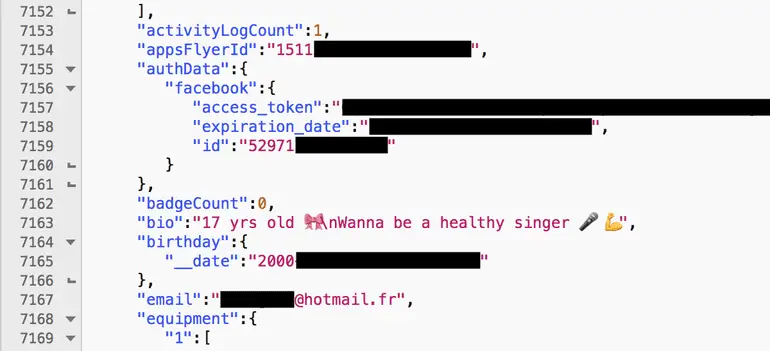
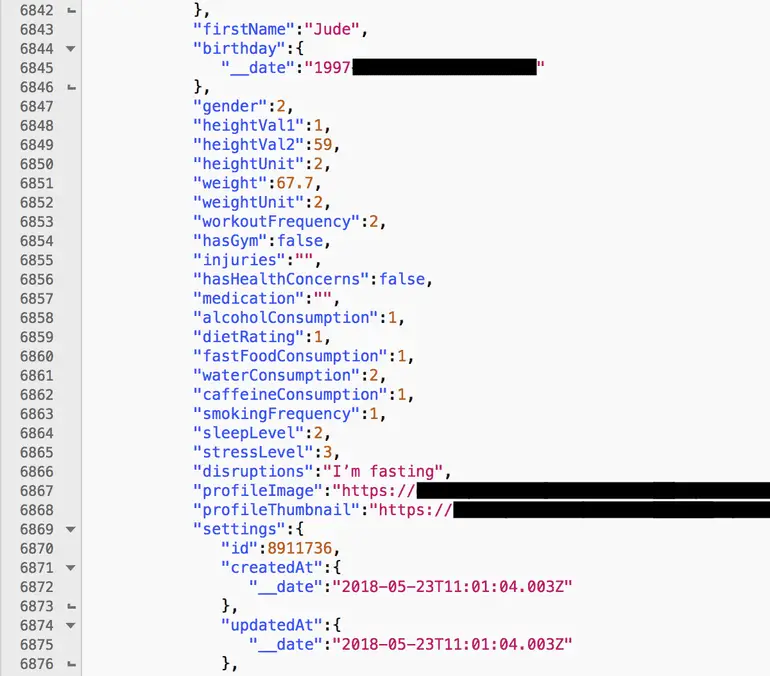
ZDNet pointed out that the exposed data mainly includes the user’s e-mail address, birth date, gender, and geographic information of the user’s location, as well as the user’s biometrics, exercise and activity goals, user avatars, and whether the user has been blocked or not. The application was rated. In addition, the app also exposed user-submitted health information such as height, weight, caffeine, and alcohol intake, smoking frequency, health problems, medications, and injuries.
 The exposed data also includes some device data, such as iOS and Android advertising identifiers, the user’s IP address, and the application’s session token, which can be used to access the user’s account without a password.
The exposed data also includes some device data, such as iOS and Android advertising identifiers, the user’s IP address, and the application’s session token, which can be used to access the user’s account without a password.
Users who log in using Facebook accounts also expose their access tokens and put their Facebook accounts at risk.

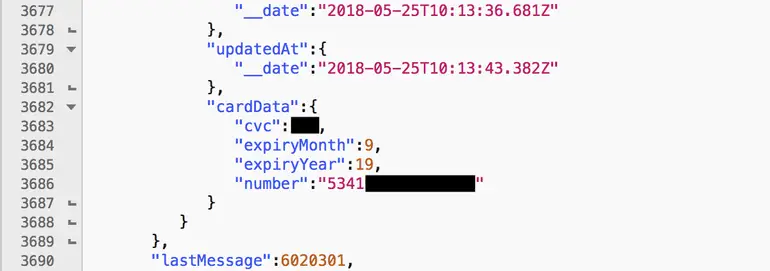
In some cases, exposure may also include unencrypted user credit card data such as card number, expiration date, and Card Verification Value (CVV).
ZDNet said that they spent more than a week to get in touch with PumpUp, but they did not receive any response from PumpUp. The good news is that the server was password protected earlier last week, but it is not clear how long this server has been exposed.
Source, Image: ZDNet





