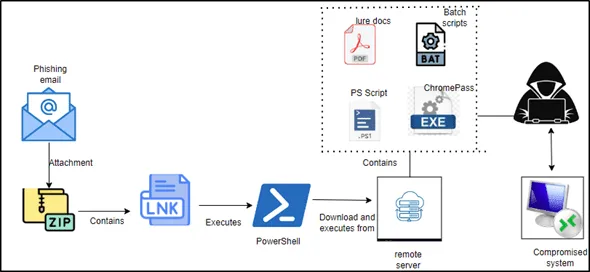
Infection chain | Image: CRIL
Cyble Research and Intelligence Labs (CRIL) has recently uncovered a covert and sophisticated cyberespionage campaign dubbed “HeptaX,” which exploits Remote Desktop Protocol (RDP) settings to gain unauthorized access to targeted systems. The HeptaX group employs multi-stage attack strategies that allow them to monitor, steal, and manipulate data across various industries, particularly healthcare.
According to CRIL, the HeptaX campaign often begins with a phishing email carrying a malicious .lnk shortcut file concealed within a ZIP archive. Once this file is executed, a PowerShell command initiates, downloading additional payloads from a remote server. “Upon execution, the LNK file triggers a PowerShell command that downloads and executes a series of additional payloads,” notes CRIL. These scripts work together to create a new administrative user account and modify RDP settings, effectively bypassing security measures. With these changes, attackers gain seamless access to the victim’s system.
In later stages of the attack, a PowerShell script creates a hidden user account named “BootUEFI,” granting it both administrative and remote desktop privileges. This account is hidden from the login screen, ensuring the victim remains unaware of the unauthorized user. CRIL describes this process: “The batch file… adjusts Terminal Services (Remote Desktop) settings to facilitate easier remote connections without stringent authentication requirements.”
This persistent setup allows the threat actors to continually access the infected machine, enabling them to monitor system activity, exfiltrate sensitive information, and install further malware without raising alarms.
Among the arsenal of tools, CRIL discovered an unwanted application called ChromePass in the attacker’s infrastructure. ChromePass specifically targets saved passwords from Chromium-based browsers, exposing a new layer of risk. By harvesting browser-stored credentials, HeptaX can easily infiltrate other systems and networks the victim may access, multiplying the potential impact of their espionage activities.
The HeptaX campaign’s reliance on basic yet effective scripts, particularly PowerShell and Batch files, exemplifies how even simple tools can accomplish complex cyberespionage tasks. CRIL emphasizes the risk, stating, “This combination of tactics highlights the need for enhanced detection and prevention measures to combat these stealthy cyber threats effectively.”
Related Posts:
- New Phishing Scam Targets Android Users in India, Researchers Warn
- Turla APT Suspected in “Tiny BackDoor” Campaign Leveraging MSBuild to Evade Detection
- Cybercriminals Escalate Attacks Exploiting Microsoft SmartScreen Flaw (CVE-2024-21412)
- Hackers Fake ChatGPT App to Spread Windows, and Android Malware
- Transparent Tribe & SideCopy: A Dangerous Cyber Alliance Targeting India