Hexrays Toolbox: Find code patterns within the Hexrays AST
Hexrays Toolbox
Hexrays Toolbox is a script for the Hexrays Decompiler which can be used to find code patterns within decompiled code:
- scan binary files for known and unknown vulnerabilities
- locate code patterns from previously reverse engineered executables within newly decompiled code
- malware variant analysis
- find code similarities across several binaries
- find code patterns from one architecture within executable code of another architecture
- many more, limited (almost) only by the queries you’ll come up with 😉
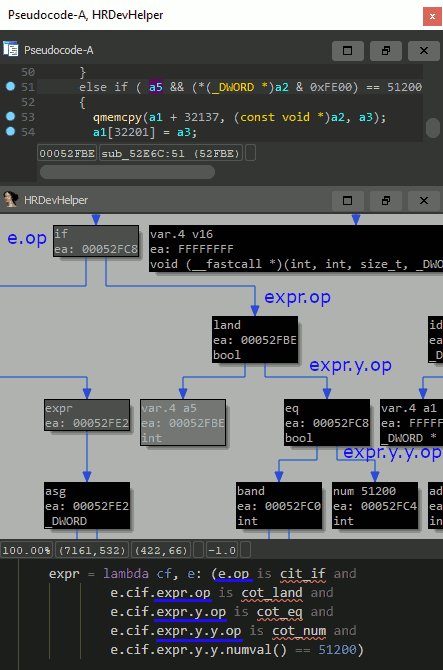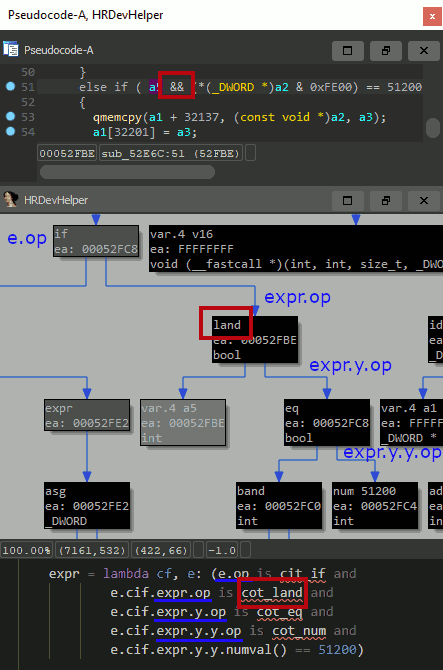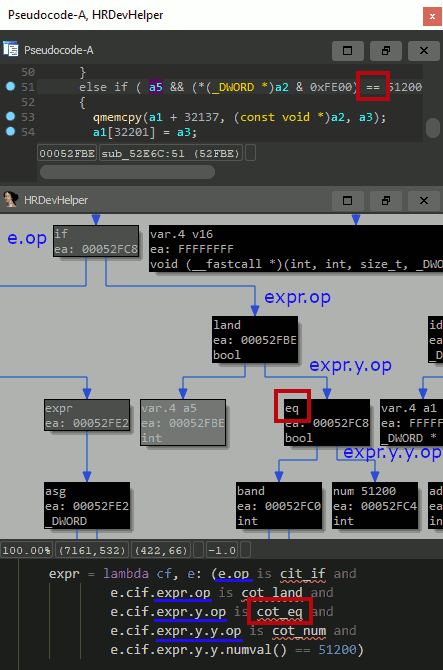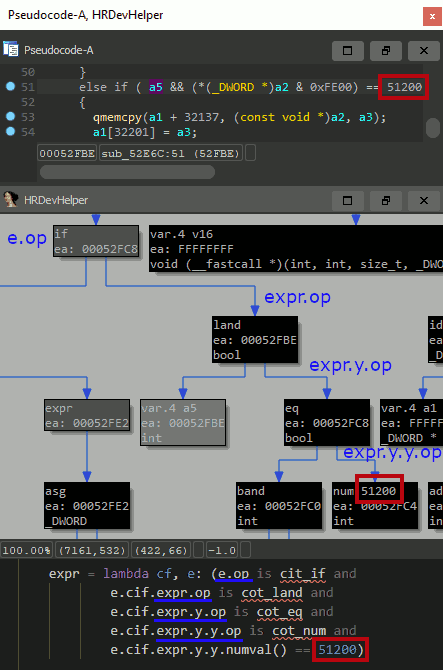
The query shown below can be used to detect CVE-2019-3568 in libwhatsapp.so.
Download
git clone https://github.com/patois/HexraysToolbox.git
Use
Loading hxtb.py with IDA (alt-f7) will make available the “find_expr()” and “find_item()” functions to the IDAPython CLI and the script interpreter (shift-f2).
find_item(ea, q)
find_expr(ea, q)Positional arguments:
ea: address of a valid function within
the current database
q: lambda function
custom lambda function with the following arguments:
1. cfunc: cfunc_t
2. i/e: cinsn_t/cexpr_t
Returns:
list of query_result_t objectsExample:
find_expr(here(), lambda cf, e: e.op is cot_call)-> finds and returns all function calls within a current function.
The returned data is a list of query_result_t objects (see hxtb.py).The returned list can be passed to an instance of the ic_t class,
which causes the data to be displayed by a chooser as follows:from idaapi import *
import hxtb
hxtb.ic_t(find_expr(here(), lambda cf,e:e.op is cot_call))Please find the cfunc_t, citem_t, cinsn_t and cexpr_t structures
within hexrays.hpp for further help and details.





