Hfinger – fingerprinting HTTP requests
Tool for fingerprinting HTTP requests of malware. Based on Tshark and written in Python3. Working prototype stage 🙂
Its main objective is to provide a representation of malware requests in a shorter form than printing the whole request, but still human interpretable. This representation should be unique between malware families, which means that any fingerprint should be seen only for one particular family.
An academic paper accompanies work on this tool, describing, for example, the motivation of design choices. It will be published here after the peer-review process.
The idea
The basic assumption of this project is that HTTP requests of different malware families are more or less unique, so they can be fingerprinted to provide some sort of identification. Hfinger retains information about the structure and values of some headers to provide means for further analysis. For example grouping of similar requests – at this moment it is still work in progress.
After analysis of malware’s HTTP requests and headers, some parts of requests were identified as being most distinctive. These include:
- Request method
- Protocol version
- Header order
- Popular headers’ values
- Payload length, entropy, and presence of non-ASCII characters
Additionally, some standard features of request URL were also considered. All these parts were translated into a set of features, described in detail here.
The above features are translated into varying length representation, which is the actual fingerprint. Depending on the report mode, different features are used to fingerprint requests. More information on these modes is presented below. The feature selection process will be described in the upcoming academic paper.
Install
git clone https://github.com/CERT-Polska/hfinger.git
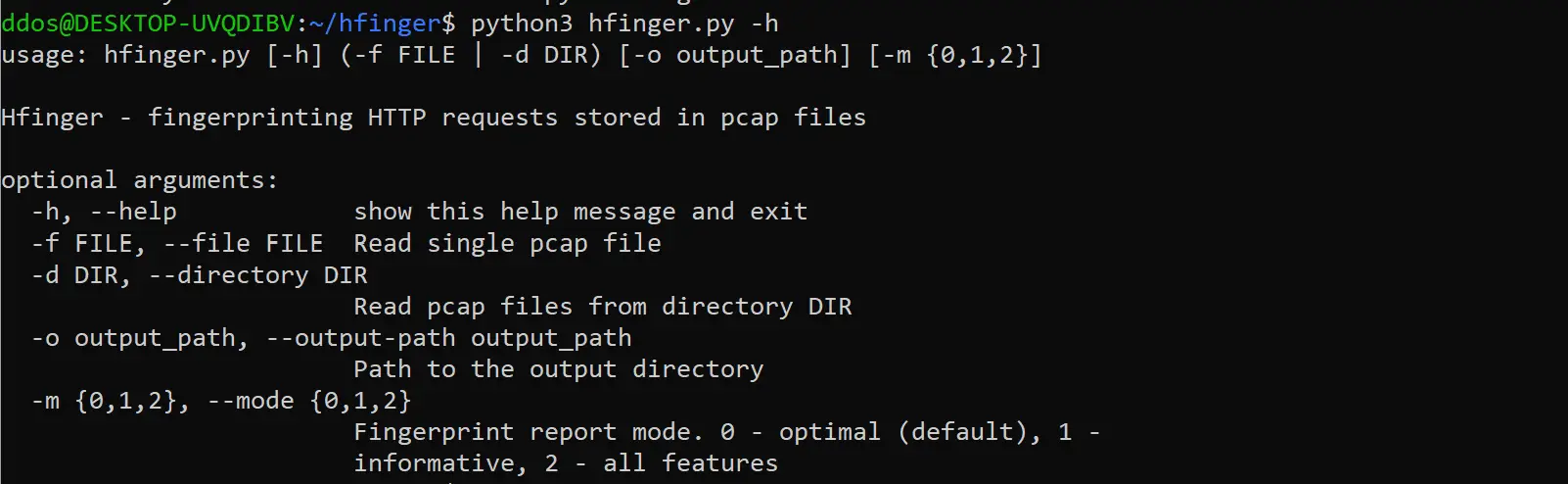
Usage
Copyright (C) 2020 cert