Image: ESET
Malware researcher Dominik Breitenbacher from ESET revealed HiddenFace, a highly sophisticated backdoor malware developed by the MirrorFace APT group. This backdoor, also known as NOOPDOOR, is the most complex malware in MirrorFace’s arsenal, crafted with a heavy focus on modularity. It’s designed to adapt to current operational needs and employs various anti-detection and anti-analysis techniques.
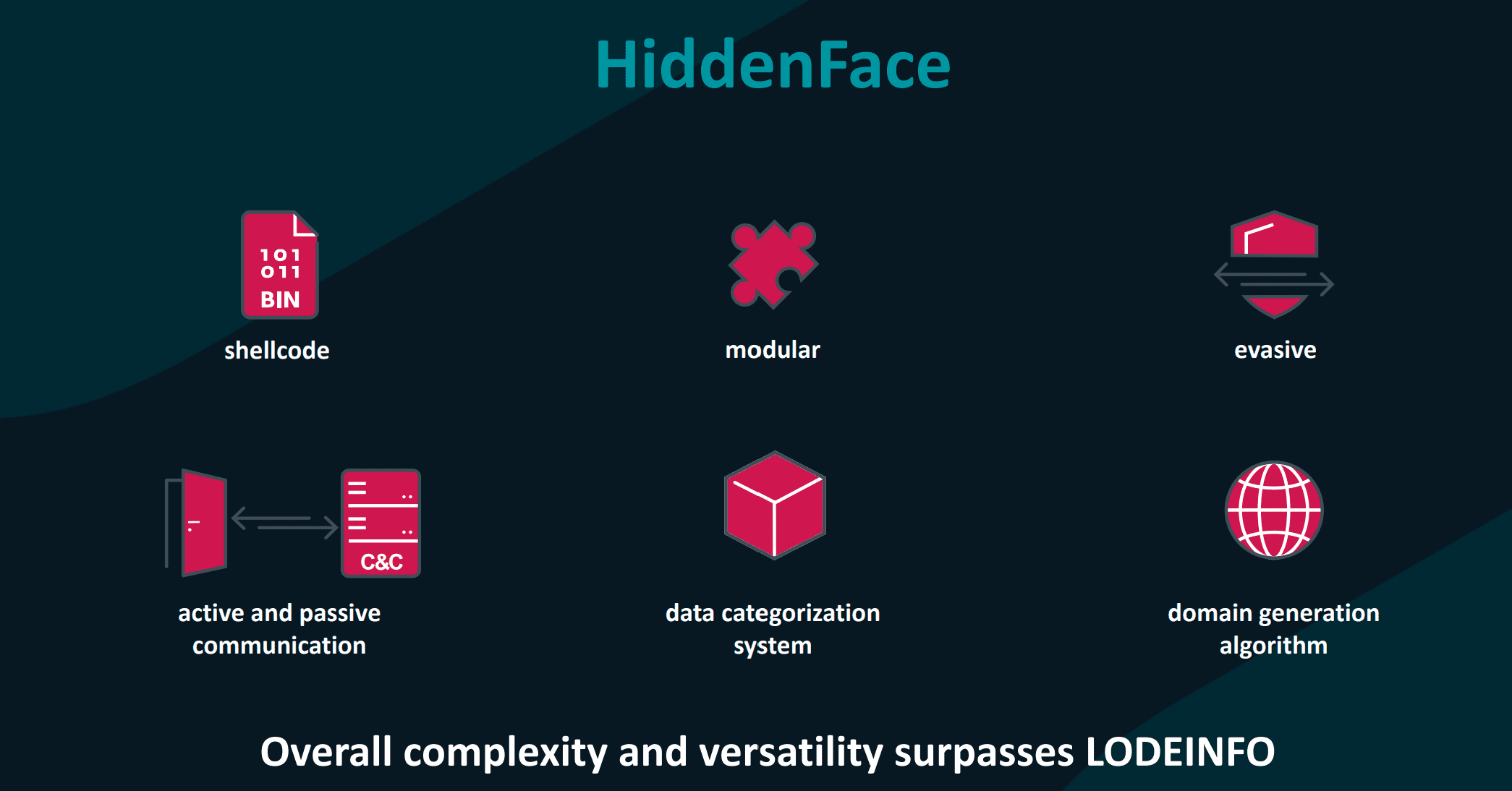
HiddenFace stands out due to its modular system, allowing the integration of both built-in functions and externally loaded shellcode modules. These modules are encrypted with AES-256-CBC and are tied to a user-specific filename, key, and initialization vector, making them highly secure and personalized.

The execution chain of HiddenFace reveals its meticulous design. It utilizes MSBuild for launching and employs FaceXInjector for injecting malicious XML files. This complex execution chain demonstrates the malware’s protective nature, indicating its high value to MirrorFace. The malware avoids detection by dynamically resolving Windows APIs, restricting DLL loading to Microsoft-signed ones, and performing random sleep intervals to elude sandbox or security solutions.
HiddenFace actively connects to command-and-control (C&C) servers, using a domain generation algorithm (DGA) and a custom protocol over TCP. It also possesses a passive communication capability, listening on hard-coded ports and reconfiguring the Windows firewall to allow communication. The communication is encrypted using AES-128-CBC, further showcasing its sophisticated design.
HiddenFace’s complexity, versatility, and protective execution chain make it an exceptionally valuable tool for MirrorFace’s cyber operations. Its development reflects a significant investment in time and resources, highlighting the evolving sophistication of APT groups in the realm of cyber warfare.