HKCERT Warns Phishing Campaigns Targeting Users in Various Platforms on the Rise
According to the Hong Kong Computer Emergency Response Coordination Centre (HKCERT), Hong Kong is facing an increasingly complex phishing threat landscape. Hackers are employing sophisticated techniques to impersonate banks, government agencies like the Inland Revenue Department, and widely-used platforms like WhatsApp. These attacks aim to steal sensitive personal and financial data, potentially leading to significant losses for individuals and businesses.
The Evolving Attack Strategies
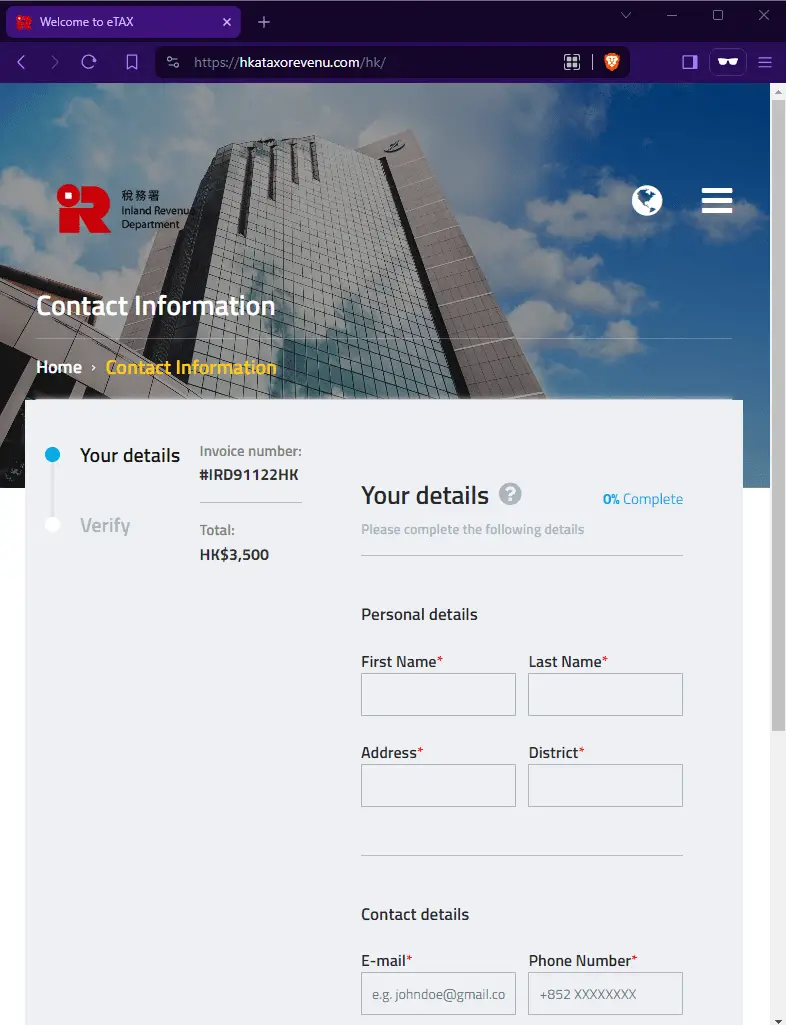
- Deceptive Clones: Attackers meticulously replicate official websites, luring victims into entering confidential details like ID card numbers, credit card information, and login credentials.

Phishing page | Image: HKCERT
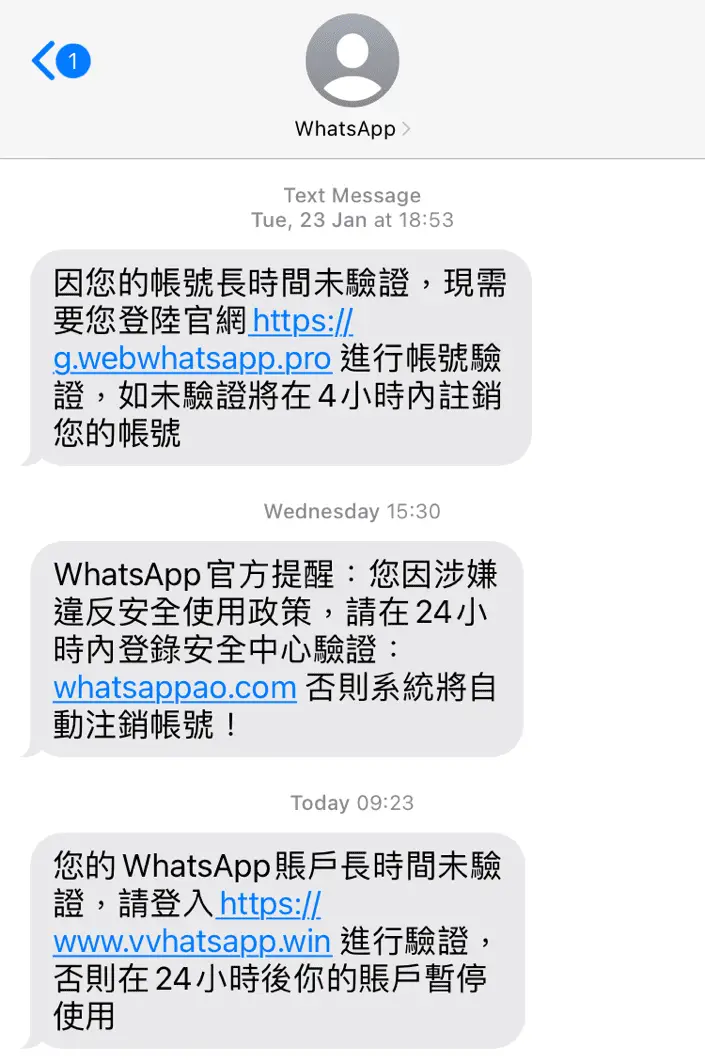
- Messaging App Hijacking: Fake login pages, often promoted through search engine ads, trick users into handing over control of their messaging accounts. This allows hackers to impersonate individuals and exploit their networks.

Image: HKCERT
Potential Consequences
- Financial Theft: Hackers can access bank accounts or open fraudulent lines of credit using stolen personal information.
- Identity Fraud: Comprehensive data theft paves the way for tax fraud, false government claims, and other damaging actions taken in a victim’s name.
- Wider Exposure: Compromised accounts or information may be used to launch attacks against businesses and other connected individuals.
Critical Defense Measures
The Hong Kong Computer Emergency Response Coordination Centre (HKCERT) emphasizes the need for heightened awareness and the following actionable steps:
- URL Scrutiny: Carefully inspect website addresses (URLs) before entering any data. Watch for typos, unusual domains, or subtle differences from official sites.
- Safeguard Your Links: Avoid clicking links in emails, SMS, or social media posts, even seemingly legitimate ones. Manually type known URLs or use trusted bookmarks.
- Messaging App Hygiene: Regularly check your connected devices and review “archived” folders in messaging apps for suspicious activity. Log out unknown devices immediately.
- Independent Verification: Always confirm financial requests, even from familiar contacts, through other channels like a phone call or in-person meeting.