HookDump: EDR function hook dumping
HookDump
EDR function hook dumping.
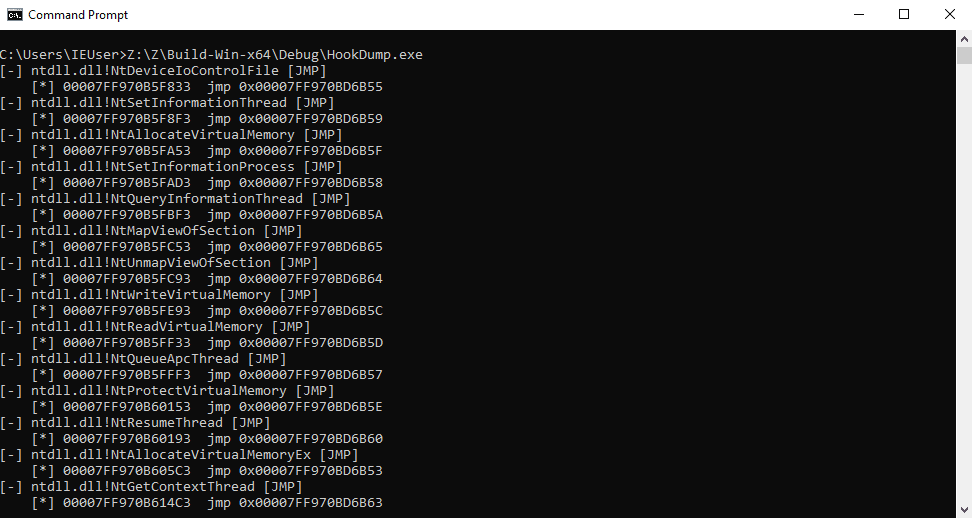
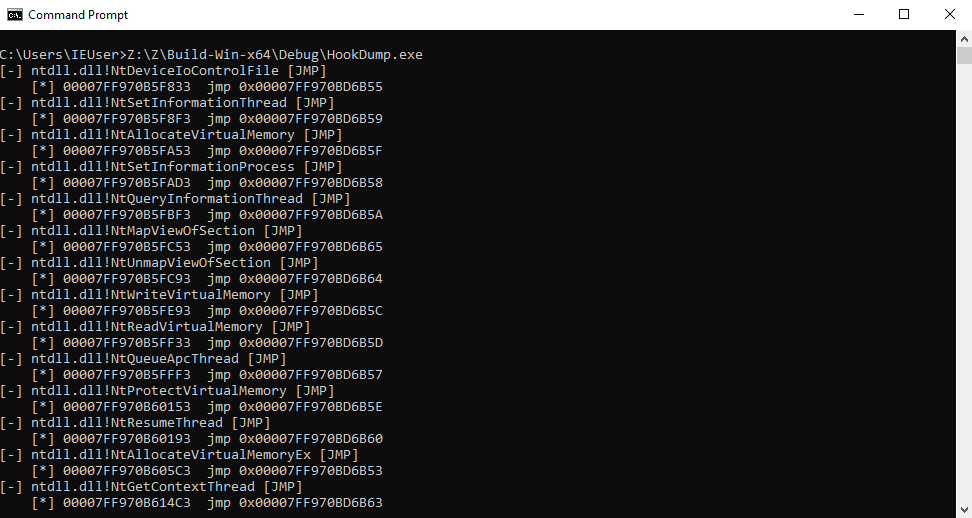
Hook Types Detected
JMP
A jump instruction has been patched into the function to redirect execution flow
WOW
Detection of the WOW64 syscall stub being hooked, which allows filtering of all system calls
EAT
The address in the export address table does not match the address in the export address table in the copy on disc
GPA
GetProcAddress hook, an experimental feature, this is only output in verbose mode, when the result of GetProcAddress does not match the manually resolved function address. YYMV with this and some care should be taken to verify the results.
Verification
The only way to truly verify the correct working of the program is to check in a debugger if hooks are present. If you are getting a zero hooks result and are expecting to see something different, then first verify this in a debugger, and please get in touch.
Notes
- Some EDRs replace the WOW stub in the TEB structure (specifically Wow32Reserved) in order to hook system calls for 32-bit binaries. In this case, you may see zero hooks since no jump instructions are present in NTDLL. Most likely you will see hooks in the x64 version as the syscall instruction is used for system calls instead of a WOW stub
- We have noted that Windows Defender does not use any user-mode hooks
- This tool is designed to be run as a standard user, elevation is not required
Download & Use
Copyright (C) 2021 Coder666