
Infection Chain
In a recent discovery by the SonicWall Capture Labs threat research team, a new malware crypter known as “HORUS Protector” has emerged, presenting a significant threat to cybersecurity defenses. This Fully UnDetectable (FUD) crypter is being utilized to spread a range of notorious malware families, including AgentTesla, Remcos, Snake, and NjRat.
HORUS Protector employs a complex and multi-stage infection chain that begins with scripts hidden inside archive files. These scripts, often VBE (encoded VBS), are used to bypass security mechanisms. As the report states, “Most malicious files are distributed through scripts contained in archive files. Recent infections have been attributed to VBE scripts”. Once executed, the script connects to a Command-and-Control (C2) server, downloading several files needed for further exploitation.
The downloaded data is stored in the system’s registry, a tactic designed to evade detection. The registry path [HKEY_CURRENT_USER\SOFTWARE\uOITNhlpKJsMLJx] stores critical information and executable files for the next stage of the attack. The malware also uses task scheduling to ensure persistence, creating a task that triggers every minute to execute a malicious VBS file stored in the user’s AppData directory.
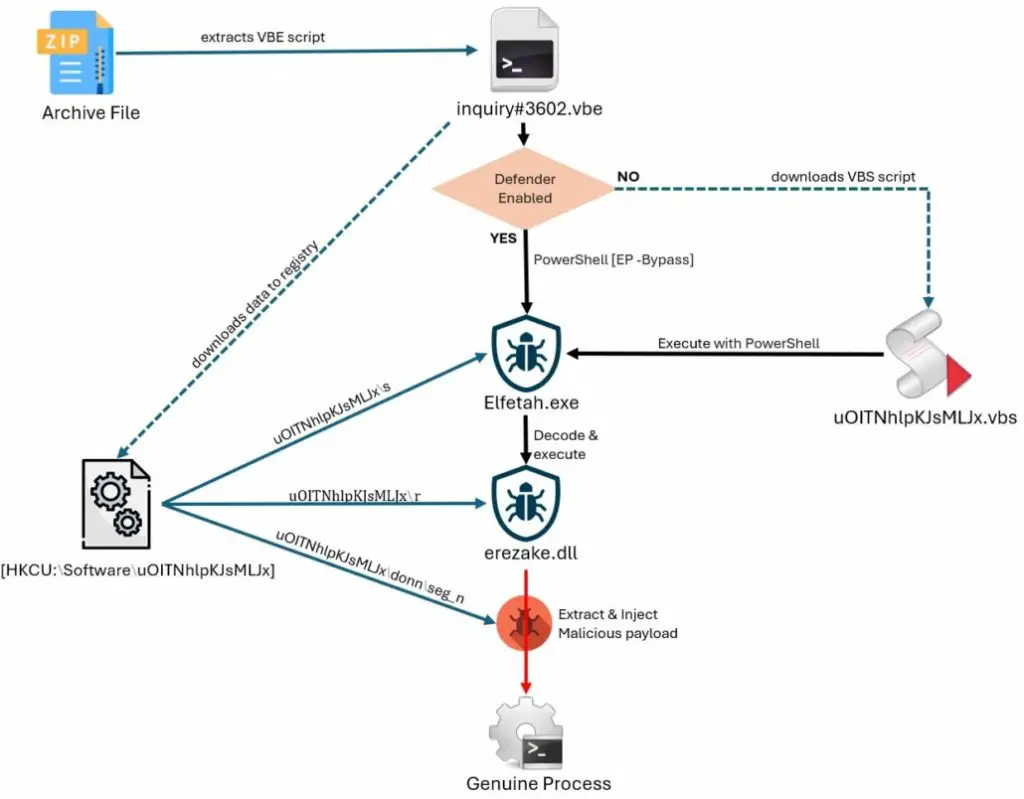
One of HORUS Protector’s unique aspects is its ability to check for antivirus software, particularly Windows Defender. If Defender is active, the malware uses PowerShell with the command: “PowerShell.exe -ExecutionPolicy Bypass -WindowStyle Hidden -NoExit,” effectively bypassing many of the default protections provided by the system. This allows the malware to continue its operations unhindered, further executing additional malicious files hidden in the system’s registry.
The second stage of the malware’s operation involves injecting its main payload into legitimate system processes. The payload is stored in hexadecimal format within the registry, divided across several subkeys. The malware then uses image hollowing, a process injection technique, to embed its payload into a running process, commonly MSBuild.exe, which is typically found on targeted systems.
Once inside MSBuild.exe, the payload executes its final stage, often a keylogger or other data-stealing malware. As the researchers noted, “The injected payload was the SNAKE Keylogger,” which is infamous for stealing sensitive information such as keystrokes, clipboard data, and browser information.
Interestingly, HORUS Protector also offers an optional “BotKill” feature, which can be activated by the malware author during the creation of the payload. This feature ensures that the malware deletes itself from the victim’s system, removing all traces of persistence, including scheduled tasks and registry keys.
The HORUS Protector service represents a new level of sophistication in the malware distribution ecosystem. By utilizing advanced techniques like registry-based storage, antivirus detection, and process injection, it provides cybercriminals with a robust and stealthy toolset. As the SonicWall team concludes, “We have observed similar mechanisms spreading different malware over this period. It would be interesting to see what new versions authors will bring in future.”
Related Posts:
- Cybercrime Actors Behind Agent Tesla Campaigns Unmasked
- CVE-2024-36072 (CVSS 10): Unauthenticated RCE Flaw in CoSoSys Endpoint Protector