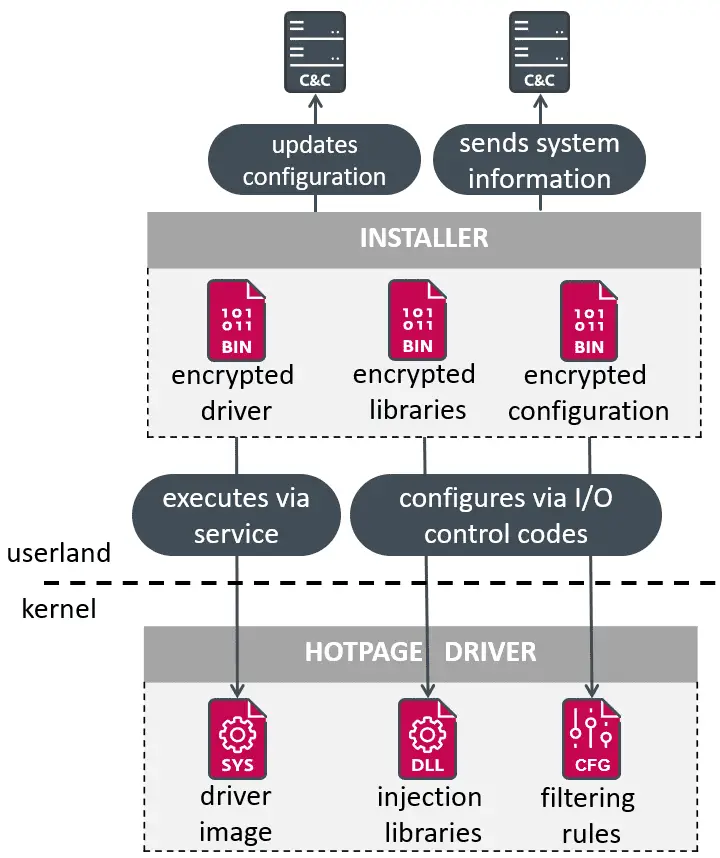
Overview of the installer’s workflow | Image: ESET
At the end of 2023, researchers stumbled upon an intriguing discovery—a setup file named HotPage.exe. At first glance, this application appeared to be yet another piece of adware. However, deeper analysis revealed that behind its innocuous facade lay a sophisticated piece of malware with impressive capabilities.
HotPage.exe installs a driver capable of injecting code into remote processes, along with two libraries that intercept and modify browser network traffic. This allows the malware to alter the content of requested web pages, redirect users to different sites, or open new tabs under certain conditions.
What particularly caught the researchers’ attention was that the driver was signed with a Microsoft certificate. According to the signature, it was developed by the Chinese company Hubei Dunwang Network Technology Co., Ltd. The lack of any information about this firm only fueled the experts’ interest.
The program was advertised as a “solution for internet café security,” targeting a Chinese-speaking audience. It purportedly aimed to simplify internet usage by blocking ads and malicious sites. In reality, its main objective was to inject game advertisements into users’ browsers.
This kernel component inadvertently leaves a backdoor for other threats. Due to improper access restrictions, any process can interact with the driver and exploit its capabilities.
Researchers reported the issue to Microsoft on March 18, 2024. After verification, the Microsoft Security Response Center (MSRC) determined that the vulnerability was no longer relevant, as the problematic driver was removed from the Windows Server catalog on May 1, 2024.
Examining the driver’s digital signature, experts discovered that the Chinese company had undergone Microsoft’s verification process for driver code signing and received an Extended Verification (EV) certificate. Evidently, the perpetrators went to great lengths to lend legitimacy to their product.
Further investigation revealed that the company was registered on January 6, 2022. According to official records, its business scope includes technology development, consulting, and advertising services. The main shareholder is a small firm, Wuhan Yishun Baishun Culture Media Co., Ltd, specializing in advertising and marketing.
In April and May 2022, the company filed applications to register the trademark “Shield Internet Café Security Defense.” A website, dwadsafe[.]com, was created on February 22, 2022, which was inaccessible at the time of the investigation.
Upon examining the program’s website, researchers found an interesting discrepancy. The product was marketed as a “proactive protection platform for internet cafés,” but the license agreement contained conflicting information. One clause stated that DwAdsafe had no interception functions and did not affect other programs. However, another clause claimed that the program had extensive control capabilities, including interception, monitoring, and even data deletion.
A technical analysis of the HotPage.exe installer revealed the following features:
- The file was compressed with the UPX packer.
- The installer contained encrypted versions of the driver, libraries for process injection in browsers, and three JSON configuration files.
- Upon execution, the program checks whether it is running in a virtual environment using the CPUID instruction.
- The driver is saved in the C:\Windows\ShieldNetWork\Business\ folder under a random 7-character name with a .sys extension.
- A service is created to start the driver, but without autostart mechanisms.
- The installer interacts with the driver through its file device, using the following IOCTL codes:
- 0x9C4013FC – sends the 32-bit library for browser process injection.
- 0x9C400FFC – sends the 64-bit library for browser process injection.
- 0x9C40173C – sends the chromedll configuration.
- 0x9C400BFC – sends the updated newtalbe configuration.
The newtalbe configuration file contains crucial information for the malware’s operation, including:
- URL patterns for collecting statistics.
- A list of domains for redirecting users.
- API endpoints for updating the list of gaming domains and sending information about infected computers.
- Pattern lists for applying redirection rules.
The driver creates two threads: one for injecting libraries into browser processes, and another for opening new tabs. It also sets up handlers for process creation and image loading notifications to monitor new processes.
The injected library intercepts the SSL_read and SSL_write functions, allowing manipulation of decrypted TLS traffic. Special patterns found in the loaded browser modules are used for this purpose.
The library also intercepts the NtDeviceIoControlFile function to handle specific IOCTL codes. This enables the cancellation of DNS requests and the modification of outgoing and incoming HTTP requests based on rules from the configuration files.
Thus, under the guise of a program to enhance internet café security, the attackers created sophisticated malware capable of manipulating network traffic and injecting advertisements. This case demonstrates the sophistication of modern cyber threats and underscores the importance of thoroughly analyzing even seemingly benign applications.