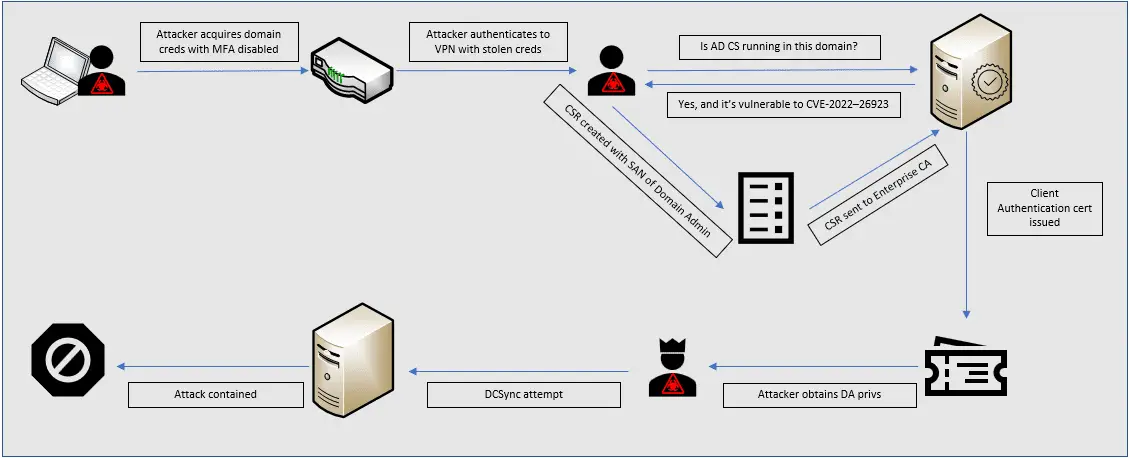
In June 2023, IBM Security X-Force responded to an incident where a client had received alerts from their security tooling regarding potential malicious activity originating from a system within their network targeting a domain controller. X-Force analysis revealed that an attacker gained access to the client network through a VPN connection using a third-party IT management account. The IT management account had multi-factor authentication (MFA) disabled to enable automated workstation provisioning.
The attacker commenced the breach by gaining access to the internal network through a VPN, employing an IT management account devoid of MFA — a vital security control for any network access. Following the ingress, the attacker identified a server operating AD CS. AD CS, a feature within Microsoft Windows, provides digital certificates for authenticating users, workstations, and servers, digitally signing messages, or encrypting data.

With a target in sight, the attacker exploited CVE-2022-26923, a vulnerability patched by Microsoft in update KB5014754, to elevate their privileges to domain administrators. Despite the patch, an unfortunate configuration in the Key Distribution Center (KDC) did not block the exploit and merely logged it as a warning. This oversight provided the attacker with enhanced domain control, leading to a consequential DCSync attack attempt.
A DCSync attack involves an attacker extracting credentials from a domain controller by mimicking it and retrieving password data through domain replication. In this case, the client’s security tools successfully detected and halted the DCSync attack. IBM’s X-Force team subsequently executed containment measures to eliminate the attacker’s access.
While CVE-2022-26923 is not new, and Microsoft has released a patch (KB5014754), there are still risks. The patch may not have been applied due to compatibility issues, and the resurgence of interest in AD CS abuse underscores the need for extra vigilance. As a result, IBM’s X-Force urges all organizations to confirm that the changes in KB5014754 are enforced.
The exploit centers on certificate templates within AD CS. An attacker can abuse loose permissions, particularly “Allow Enroll,” “CT_FLAG_ENROLLEE_SUPPLIES_SUBJECT=1,” and “Client Authentication EKU,” to escalate privileges and potentially take control of an Active Directory domain.
To protect against CVE-2022-26923, organizations should implement the following recommendations:
- Implement a vulnerability management program to ensure that all systems are up to date with the latest security patches.
- Granularly control access to certificate templates. Only users who need to create certificates should have access to the templates.
- Disable HTTP access for AD CS. This will prevent attackers from exploiting the vulnerability over the network.
- Implement strict security management of the AD CS. This includes configuring the Key Distribution Center (KDC) to block the exploit and monitoring for suspicious activity.