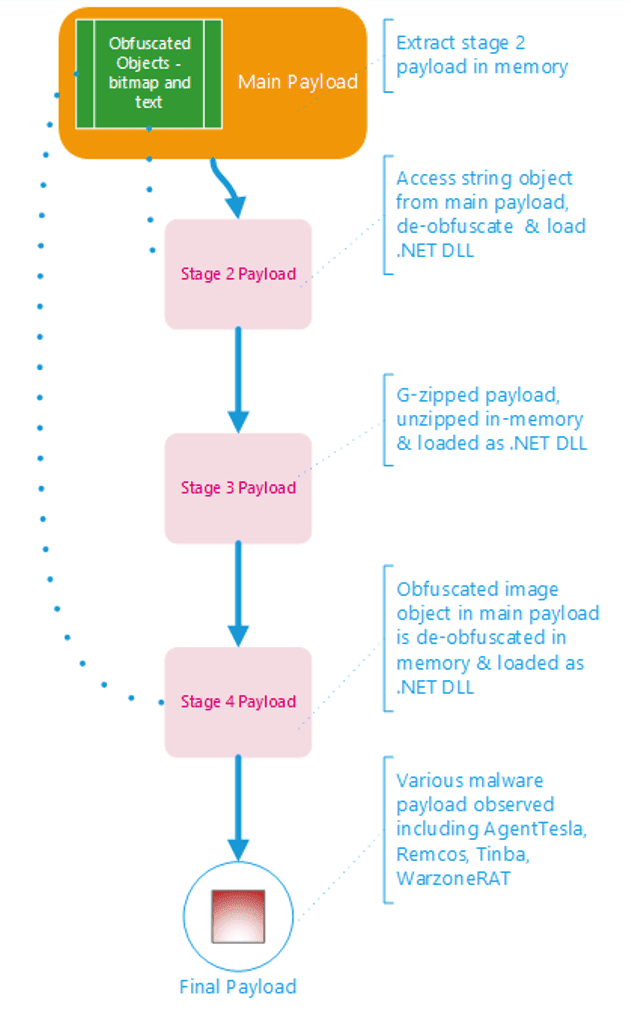
TicTacToe dropper extraction process
Recently, the FortiGuard team identified a new malware targeting the unwary with precision and ingenuity. Dubbed the “TicTacToe Dropper,” this malware has demonstrated the sophistication and adaptability of modern cyber threats.
Originating from a common Polish language string translating to “TicTacToe,” this malware has been identified by the FortiGuard team as a versatile dropper used to deliver a variety of final-stage payloads. Its name, reminiscent of a simple childhood game, belies the complexity and danger it poses, delivering malicious software such as Leonem, AgentTesla, and LokiBot, among others, into unsuspecting systems.

The TicTacToe Dropper operates by employing multi-stage obfuscated payloads, cleverly evading detection by disguising itself within .iso files to bypass antivirus software. This technique, coupled with the use of phishing to distribute these files, highlights the cunning methods employed to infiltrate systems.
Analysis of this malware reveals a labyrinth of DLL files, each layer unpacking and executing the next. This convoluted process, designed to confuse and conceal, speaks to the lengths cybercriminals will go to protect their nefarious tools from discovery and analysis.
“The executable inside the iso had multiple layers of DLL files, which were extracted at runtime and loaded directly into memory. One layer of DLL was decoded at runtime, and the next layer of DLL was loaded and decoded by the previous layer of the DLL file,” the researcher explains.
Interestingly, the TicTacToe Dropper does not serve a single master. Its use across various campaigns suggests it’s a tool sold as a service to various threat actors. The evolving nature of its obfuscation techniques, including the use of unique strings like “MatrixEqualityTestDetail” and “Pizza_Project,” indicates a continuous development effort to stay ahead of detection mechanisms.
In conclusion, the TicTacToe Dropper exemplifies the dynamic and multifaceted nature of modern malware. Its ability to deliver varied payloads, evade detection, and adapt to countermeasures makes it a formidable challenge.