Security researcher Robin has published technical details and a proof-of-concept (PoC) exploit for CVE-2024-53676, a critical vulnerability in Hewlett Packard Enterprise Insight Remote Support (Insight RS). Assigned a CVSS score of 9.8, this directory traversal vulnerability could allow unauthenticated remote attackers to execute arbitrary code on affected systems.
HPE Insight Remote Support (Insight RS) is a monitoring and support platform used by enterprises to ensure system uptime and proactive issue resolution for servers, storage, and networking hardware. The software automatically submits hardware event notifications to HPE for diagnostics and service resolution.
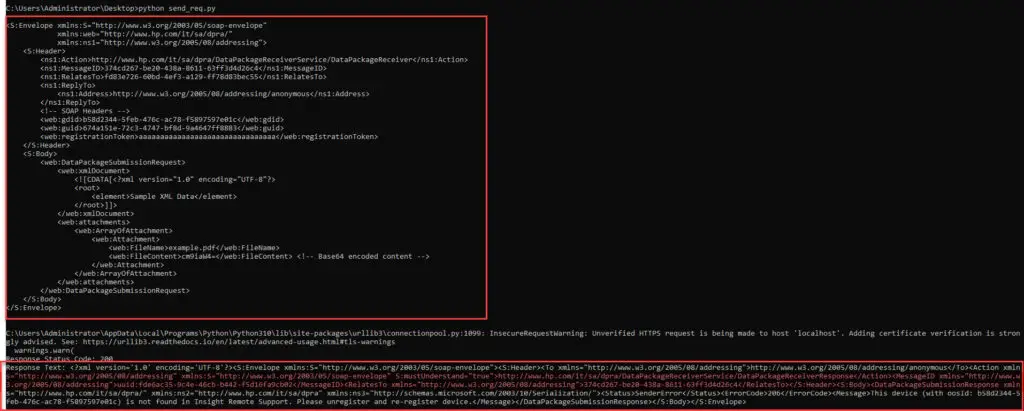
The vulnerability stems from improper path validation in the processAtatchmentDataStream method. This flaw allows attackers to bypass directory restrictions and upload malicious files outside the intended directory. According to the Zero Day Initiative (ZDI) Advisory, this flaw enables remote code execution (RCE) by uploading web shells to the web server directory, which can then be executed remotely.
Robin’s analysis of the vulnerability highlights the potential for remote code execution by uploading a crafted JSP file to the web server directory. However, due to limitations in the testing environment, full exploitation was not demonstrated.
Robin demonstrated a theoretical attack exploiting this flaw, showing how an attacker could craft a malicious SOAP request that sends a web shell to the vulnerable system. The attack follows these steps:
- Craft a SOAP request: The attacker modifies the attachment’s filename parameter to include directory traversal sequences (../../../../../webapps/ROOT/shell.jsp).
- Upload a malicious JSP shell: The file is stored in the web server directory instead of the intended folder.
- Execute the uploaded shell: By accessing the uploaded file via HTTP (http://target-ip/shell.jsp), the attacker gains remote execution capabilities.
However, full exploitation requires a valid device ID (oosId) assigned during system registration. Robin explains: “Based on our analysis, exploitation requires the gdid (oosId) and a registration token, which limits the potential for a fully unauthenticated attack.”
Despite this requirement, if an attacker can obtain valid registration credentials, they can fully exploit the vulnerability to achieve remote code execution.
To address these security concerns, HPE has promptly released Insight Remote Support v7.14.0.629. This update includes fixes for all identified vulnerabilities, and HPE strongly advises users to update their Insight Remote Support installations immediately to mitigate the risk of exploitation.
Related Posts:
- CVE-2024-12356 (CVSS 9.8): Critical Vulnerability in BeyondTrust PRA and RS Enables Remote Code Execution
- HPE Insight Remote Support Hit with Critical Vulnerabilities, Urgent Patch Released
- HPE Aruba Networking Addresses Severe Vulnerabilities in Access Points
- CVSS 9.8 Vulnerabilities Expose Aruba Access Points to RCE: HPE Urges Immediate Action