HTMLSmuggler
HTMLSmuggler – JS payload generator for IDS bypass and payload delivery via HTML smuggling.
The primary objective of HTML smuggling is to bypass network security controls, such as firewalls and intrusion detection systems, by disguising malicious payloads within seemingly harmless HTML and JavaScript code. By exploiting the dynamic nature of web applications, attackers can deliver malicious content to a user’s browser without triggering security alerts or being detected by traditional security mechanisms. Thanks to this technique, the download of a malicious file is not displayed in any way in modern IDS solutions.
The main goal of the HTMLSmuggler tool is to create an independent javascript library with embedded malicious user-defined payload. This library may be integrated into your phishing sites/email html attachments/etc. to bypass IDS and IPS systems and deliver embedded payload to the target user system. An example of a created javascript library may be found here.
Features
- Built-in highly configurable JavaScript obfuscator that fully hides your payload.
- May be used both as an independent JS library or embedded in JS frameworks such as React, Vue.js, etc.
- The simplicity of the template allows you to add extra data handlers/compressions/obfuscations.
Installation
-
Install yarn package manager.
-
Install dependencies:
yarn
-
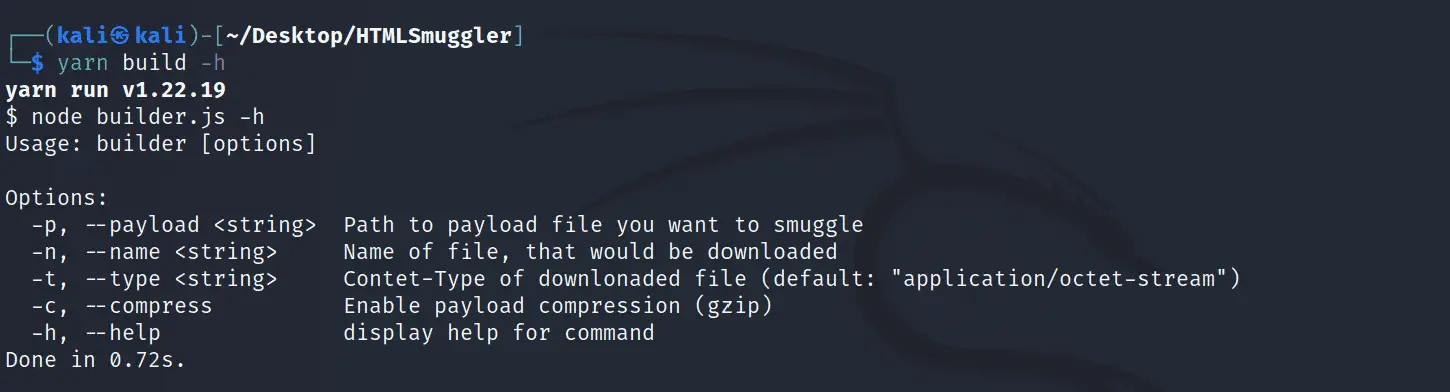
Read the help message.
yarn build -h

Tutorial
Copyright (c) 2023 Georgii Gennadev