Infection diagram | Image: X-Force
The IBM X-Force has recently shed light on a new variant of Gootloader — the “GootBot” implant, which is making waves by enabling attackers to quietly navigate and spread across enterprise networks, defying traditional detection mechanisms.
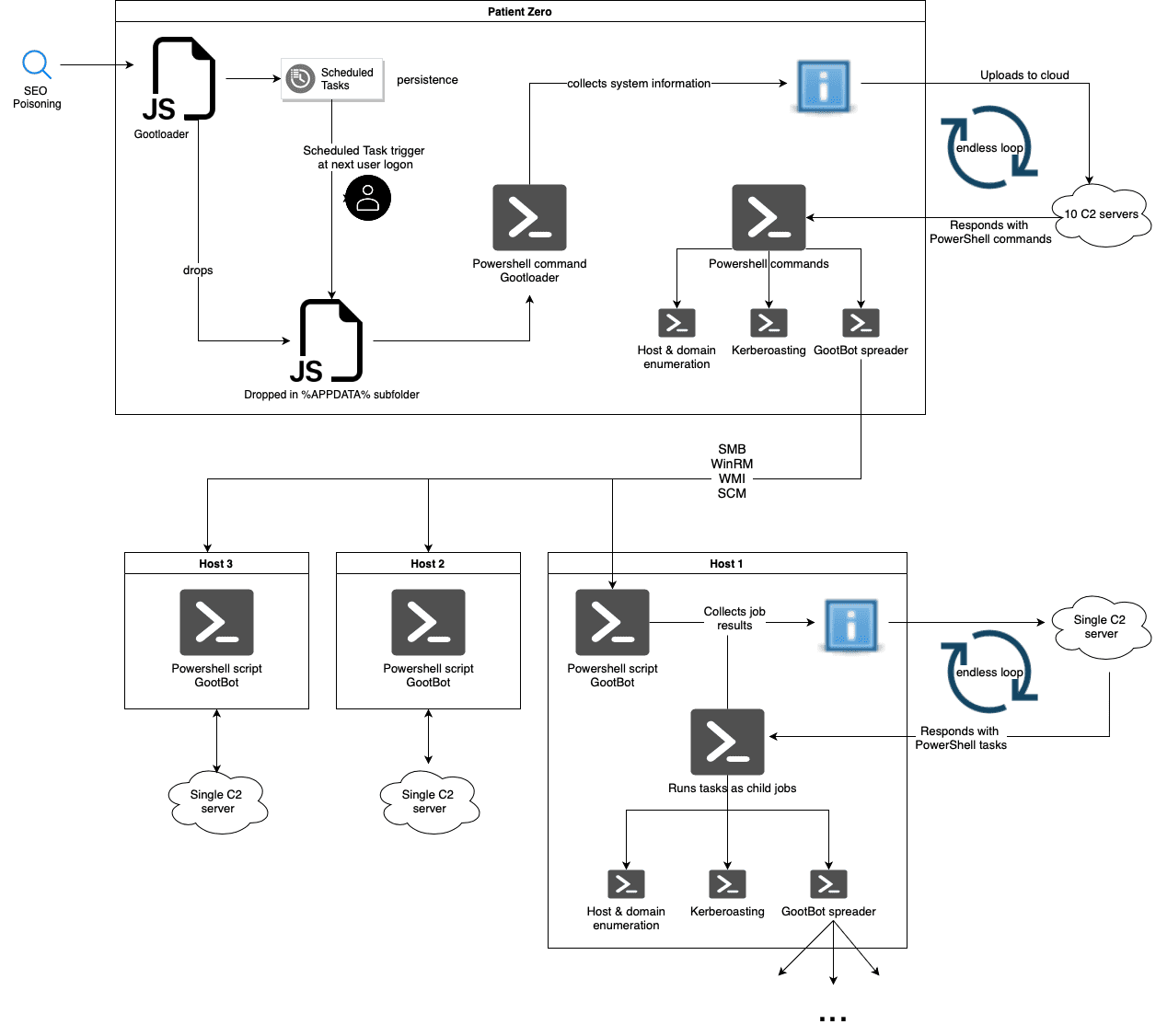
Gootloader, previously known only as a gateway for more egregious attacks, has morphed into an even greater threat. In the past, after securing initial access, it would pave the way for other malicious tools, such as CobaltStrike or RDP, to facilitate lateral movement within a victim’s network. But with the advent of GootBot, attackers are sidestepping these more detectable methods in favor of a custom tool that can operate under the radar for extended periods. This new lightweight malware is a game-changer for cybercriminals, allowing them to rapidly deploy payloads and establish a pervasive presence within an infected domain, often with the end goal of reaching domain controllers for full network compromise.

X-Force, tracking the Gootloader group under the moniker Hive0127 (also known as UNC2565), has observed this group in action since 2014. The group’s modus operandi involves a blend of search engine optimization (SEO) poisoning and exploiting vulnerabilities in WordPress sites to deliver their malware. They have a knack for luring in victims by manipulating search results and directing users to compromised websites that masquerade as legitimate forums offering business-related documents. Once a victim takes the bait and downloads what they believe are relevant files, the infection begins.
The Gootloader infection process is cleverly layered. Starting with an obfuscated JavaScript file in a downloaded archive, it advances through stages that involve a series of scheduled tasks and PowerShell scripts, culminating in the system information being sent to one of the ten C2 servers operated by the attackers. The pivotal shift here is the introduction of GootBot, a refined PowerShell script, as a subsequent payload.
GootBot is remarkable not only for its efficacy but also for its subtlety. Its communication with its command-and-control (C2) server is a testament to its stealth; it awaits encrypted PowerShell tasks and executes them without spawning new processes—thus skirting many Endpoint Detection and Response (EDR) systems. Its consistent beaconing, although adjustable, and its use of obfuscation techniques, suggest that the malware developers have a deep understanding of how to avoid modern security defenses.
The GootBot implant is purpose-built for lateral movement, using scripts that can quickly propagate the payload across the network, hunting for domain controllers and potentially leading to multiple reinfections. This activity showcases a significant enhancement in the threat actor’s capabilities, rendering the once straightforward process of blocking malicious traffic from known bad domains almost futile due to the sheer volume of compromised WordPress sites at their disposal.
This development is not just technically intriguing but deeply concerning for network defenders. The presence of GootBot indicates a potential prelude to more severe attacks, including ransomware deployment. Information theft is also a risk, with the malware capable of extracting sensitive data from compromised systems.
The revelation of GootBot highlights the persistent evolution of threat actors and the importance of staying abreast of their changing tactics, techniques, and procedures (TTPs). For organizations, this means that vigilance, along with advanced threat detection and response capabilities, is more crucial than ever in mitigating the risks posed by such sophisticated malware campaigns.