IceBox
It is a Virtual Machine Introspection solution that enables you to stealthily trace and debug any process (kernel or user). It’s based on project Winbagility.
Project Organisation
- fdp: Fast Debugging Protocol sources
- icebox: Icebox sources
- icebox: Icebox lib (core, os helpers, plugins…)
- icebox_cmd: Program that tests several features
- samples: Bunch of examples
- winbagility: stub to connect WinDBG to FDP
- virtualbox: VirtualBox sources patched for FDP.
Changelog v1.2
- Add python bindings
- Lots of bug fixes everywhere
Download
git clone https://github.com/thalium/icebox.git
Use
Some sample has been written in the samples folder.
You can build them with these instructions after you installed the requirements.
If you’re using a Windows guest you might want to set the environment variable _NT_SYMBOL_PATH to a folder that contains your guest’s pdb. Please note that icebox setup will fail if it does not find your guest’s kernel’s pdb.
vm_resume:
vm_resume just pause then resume your VM.
cd icebox/bin/$ARCH/ ./vm_resume <vm_name>
nt_writefile:
nt_writefile breaks when a process calls ntdll!NtWriteFile, and dumps what’s written in a file on your host in the current directory.
cd icebox/bin/$ARCH/ ./nt_writefile <vm_name> <process_name>
heapsan:
heapsan breaks ntdll memory allocations from a process and add padding before & after every pointer. It is still incomplete and doesn’t do any checks yet.
cd icebox/bin/$ARCH/ ./heapsan <vm_name> <process_name>
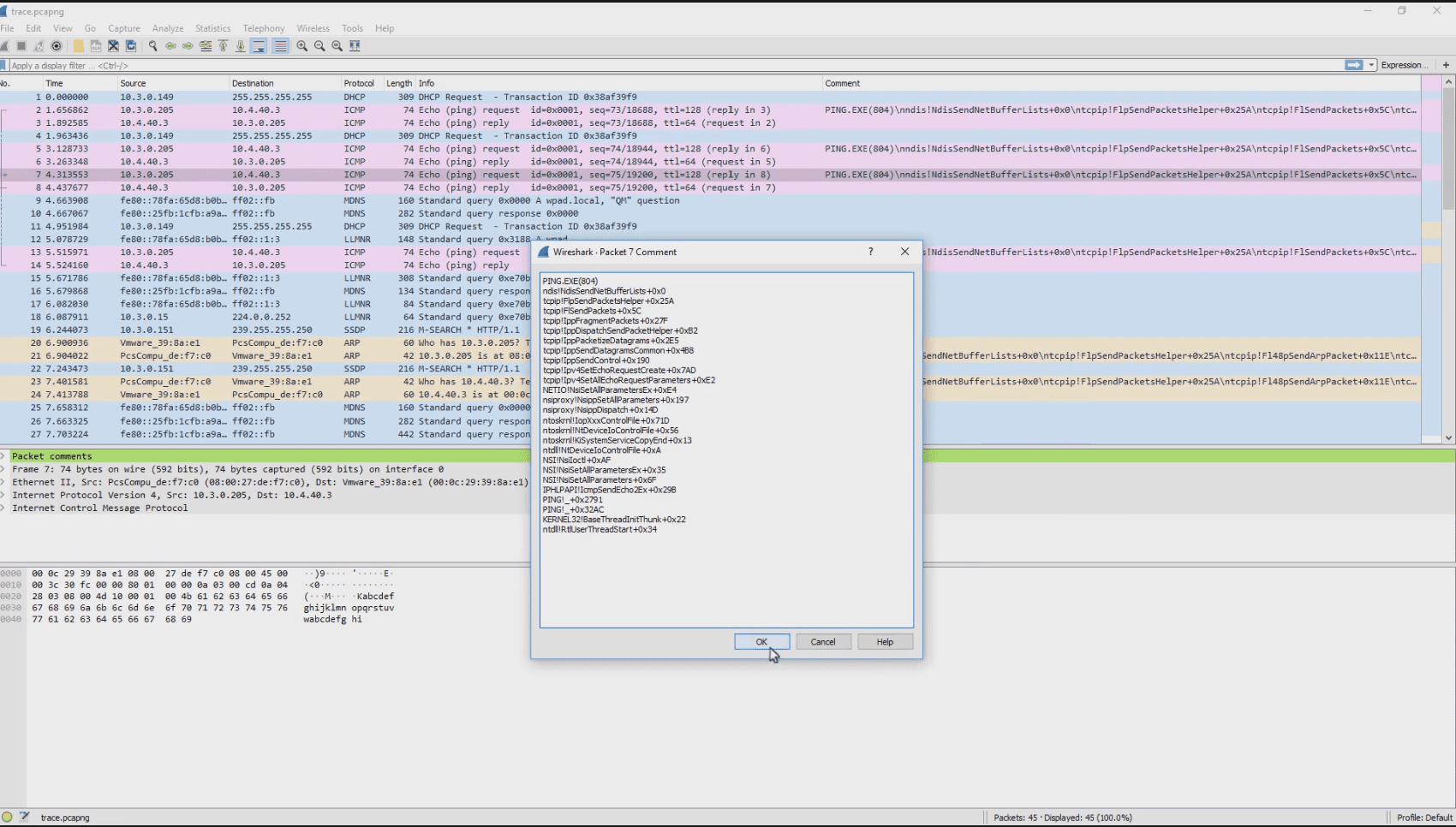
Wireshark:
Wireshark breaks when ndis driver reads or sends network packets and creates a Wireshark trace (.pcapng). Each packet sent is associated to a callstack from kernel land to userland if necessary.
cd icebox/bin/$ARCH/ ./wireshark <name> <path_to_capture_file>
Demo
Copyright (c) 2015 Nicolas Couffin ncouffin@gmail.com
Copyright (c) 2018 Benoît Amiaux benoit.amiaux@gmail.com
Copyright (c) 2018 Luca Farey luca.farey@gmail.com
Source: https://github.com/thalium/