IMDShift: Prevent SSRF attacks on AWS EC2
IMDShift
AWS workloads that rely on the metadata endpoint are vulnerable to Server-Side Request Forgery (SSRF) attacks. IMDShift automates the migration process of all workloads to IMDSv2 with extensive capabilities, which implements enhanced security measures to protect against these attacks.

Features
- Detection of AWS workloads that rely on the metadata endpoint amongst various services which includes – EC2, ECS, EKS, Lightsail, AutoScaling Groups, Sagemaker Notebooks, Beanstalk (in progress)
- Simple and intuitive command-line interface for easy usage
- Automated migration of all workloads to IMDSv2
- Standalone hop limit update for compatible resources
- Standalone metadata endpoint enable operation for compatible resources
- Detailed logging of migration process
- Identify resources that are using IMDSv1, using the
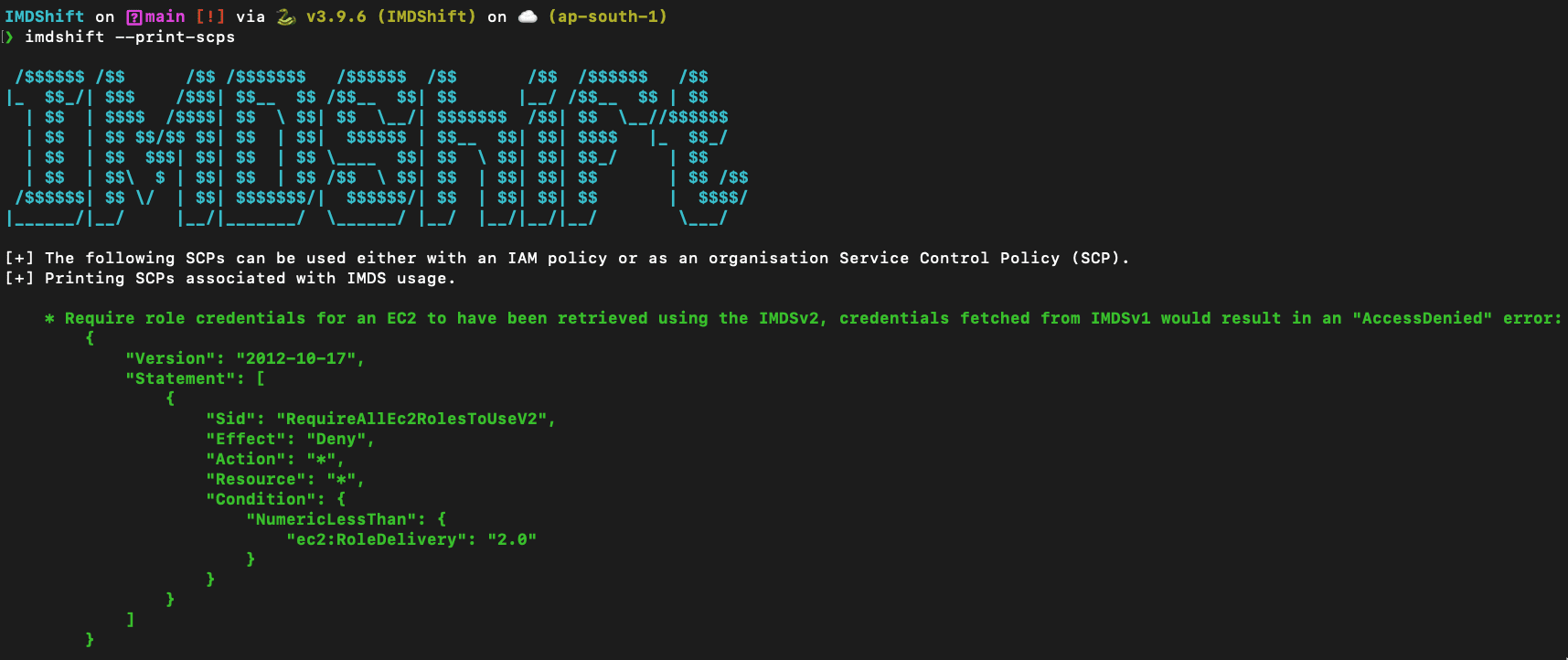
MetadataNoTokenCloudWatch metric across specified regions - Built-in Service Control Policy (SCP) recommendations
IMDShift vs. Metabadger
Metabadger is an older tool that was used to facilitate the migration of AWS EC2 workloads to IMDSv2.
IMDShift makes several improvements to Metabadger’s capabilities:
- IMDShift allows the migration of standalone services and not all EC2 instances, blindly. For example, the user can choose to only migrate EKS workloads, also some services such as Lightsail, do not fall under the EC2 umbrella, and IMDShift has the capability to migrate such resources as well.
- IMDShift allows standalone enabling of metadata endpoint for resources it is currently disabled, without having to perform migration on the remaining resources
- IMDShift allows standalone update response hop limit for resources where metadata endpoint is enabled, without having to perform migration on the remaining resources
- IMDShift allows, not only the option to include specific regions but also skip specified regions
- IMDShift not only allows usage of AWS profiles but also can assume roles, to work
- IMDShift helps with post-migration activities, by suggesting various Service Control Policies (SCPs) to implement.
Install & Use
Copyright (C) 2023 ayushpriya10





