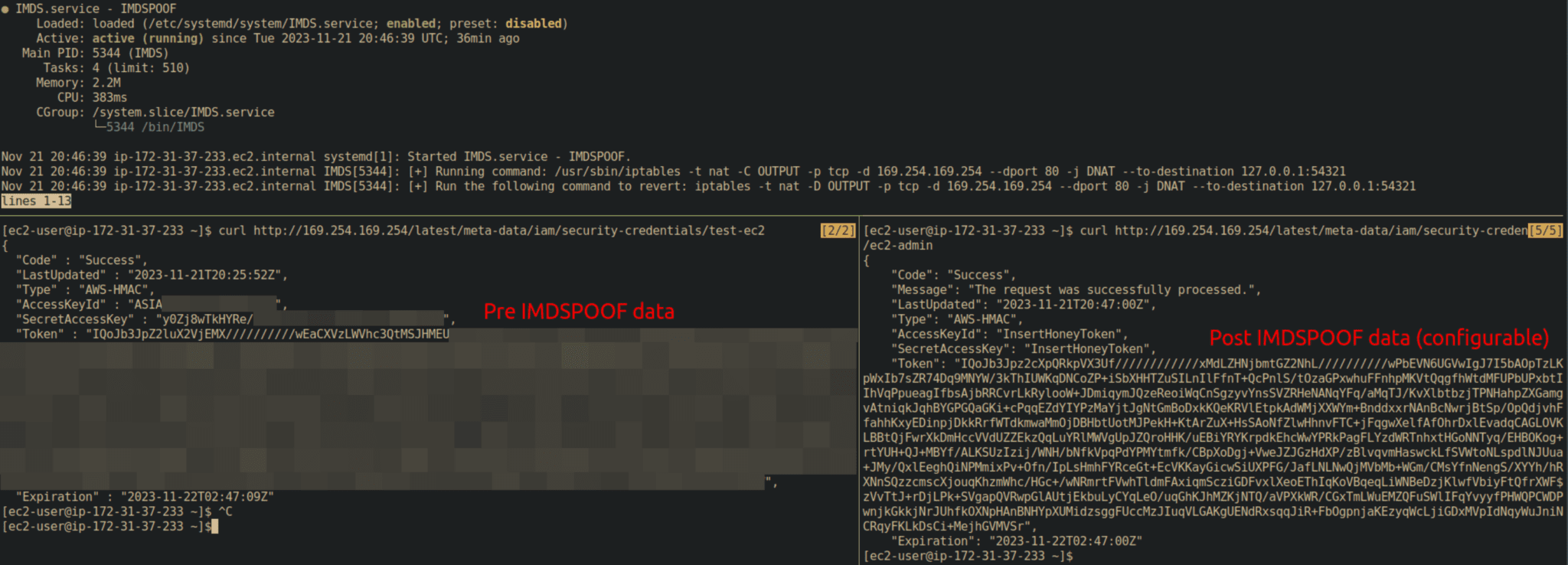
IMDSPOOF
IMDSPOOF is a cyber deception tool that spoofs an AWS IMDS service. One way that attackers can escalate privileges or move laterally in a cloud environment is by retrieving AWS Access keys from the IMDS service endpoint located at http://169.254.169.254/latest/meta-data/iam/security-credentials/<user>. This tool spoofs that endpoint and redirects traffic sent to 169.254.169.254 to a local webserver that serves fake data. This can be leveraged for highly tuned detections by inserting honey AWS tokens into the response of the spoofed IMDS response.

Who is this for?
This tool is intended to be used by blue teams on AWS instances that are NOT actively using the IMDS (version 1 or 2).
From an attacker’s perspective, they have no idea if the IMDS is being used on the EC2 instance they’re in. The goal of IMDSPOOF is to trick an attacker who lands in your cloud environment into thinking that they’re interacting with a legitimate IMDS service.
Does this work with SSRF?
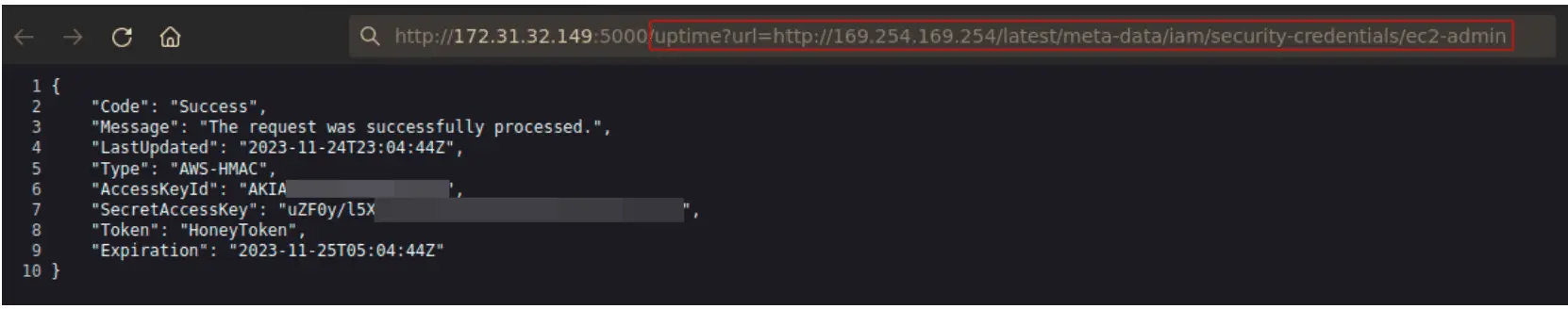
Yes! Because of the way IMDSpoof manipulates the iptables on the ec2 instance, it doesn’t matter where the traffic is coming from. This means that in addition to this working via the curl utilitiy on the EC2 instance, IMDSpoof also works if an SSRF vulnerability is found through a web application hosted on the EC2 instance. Using the following vulnerable application from AlexanderHose’s blog on IMDS pentesting, we can exploit the SSRF vulnerability which will also return the fake credentials from IMDSpoof
Reverting
- To stop the systemd service: sudo systemctl stop IMDS
- To stop the systemd service from running at startup: sudo systemctl disable IMDS
- To revert changes IMDSPOOF makes to iptables, run the following command: iptables -t nat -D OUTPUT -p tcp -d 169.254.169.254 –dport 80 -j DNAT –to-destination 127.0.0.1:54321
Install & Use
Source: https://github.com/grahamhelton/