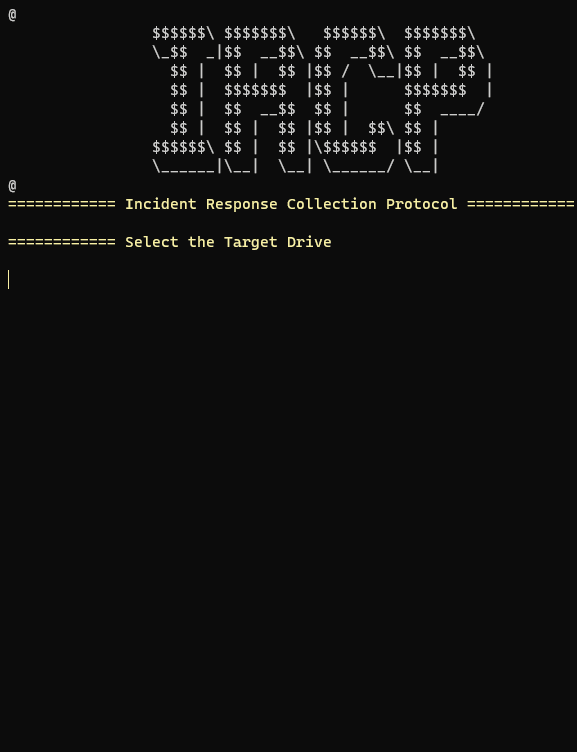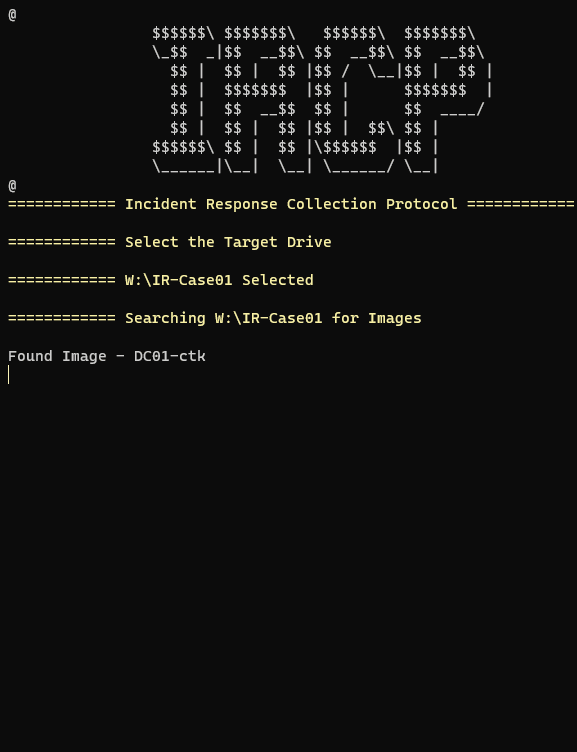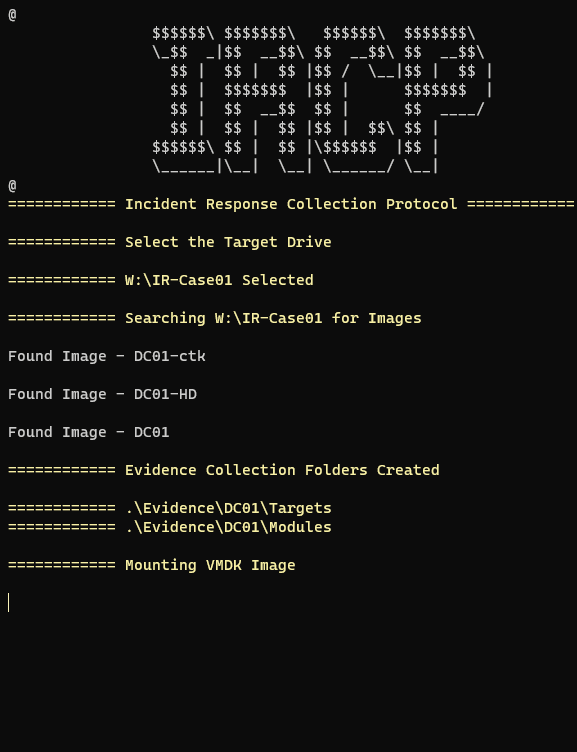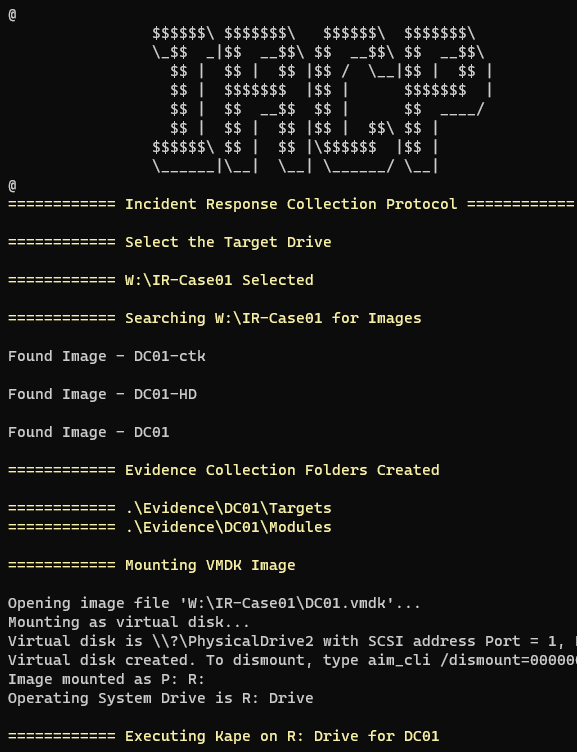
Incident Response Collection Protocol (IRCP)
A series of PowerShell scripts to automate artifact collection & assist Responders triaging endpoints in lab-based & onsite environments.

IRCP Features
IRCP supports E01, VMDK, VHD, VHDX images & Live hosts.
IRCP includes lab single image, lab multi-image, Live host & Bootable versions.
Each script contains built-in automation to mount/dismount of images, detect OS partition, detect OS type, create Evidence folders & execute Kape with parsers id’d by OS detection. A full breakdown of each script features can be found below.
IRCP has customizable Kape parser variables which Responders can change to suit varied investigational needs.
All logging is copied to the root of each host evidence folder. The logs include IRCP console log, Kape Modules/Targets log & Target System Information containing IP, domain, OS, users, timezone, etc. taken with RECmd.
IRCP-Lab-Multi
For artefact collection of multiple images across a network share or onsite harvest drive. This will locate, mount, detect OS partition, collect & dismount each image one-by-one. With minimal user interaction, it is intended to ‘Fire & Forget’ while acquisition takes place. The cycle below will run until all images have been processed –
- Select drive containing images
- Script detects a location of all images & image pointers if VMDK
- Creates Evidence folders with each image filename
- Mounts each image with Arsenal
- Locates OS partition
- Kape executes with preset parsers
- Image dismounts when complete
- All logging copied to host folder root
IRCP-Lab-Single
For artefact collection of a single image.
- Select image location
- Image mounts with Arsenal
- Locates OS partition
- Select type of endpoint (Workstation/Server)
- Creates Evidence folders with the image filename
- Kape executes with preset parsers
- Image dismounts when complete
- All logging copied to host folder root
IRCP-Live
For artefact collection of a Live host.
- Select image location
- Image mounts with Arsenal
- Creates Evidence folders from hostname
- Detects OS type – Workstation or Server
- Kape executes with endpoint id’d specific parsers
- All logging copied to host folder root
IRCP-Bootable
For artefact collection of hosts booted into WinPE/WinFE.
- Select OS drive
- Select harvest drive
- Collects hostname from the registry
- Creates Evidence folders from hostname
- Detects OS type – Workstation or Server
- Kape executes with endpoint id’d specific parsers
- All logging copied to host folder root
Download
git clone https://github.com/hackjalstead/IRCP.git
Use
Copyright (c) 2022 hackjalstead