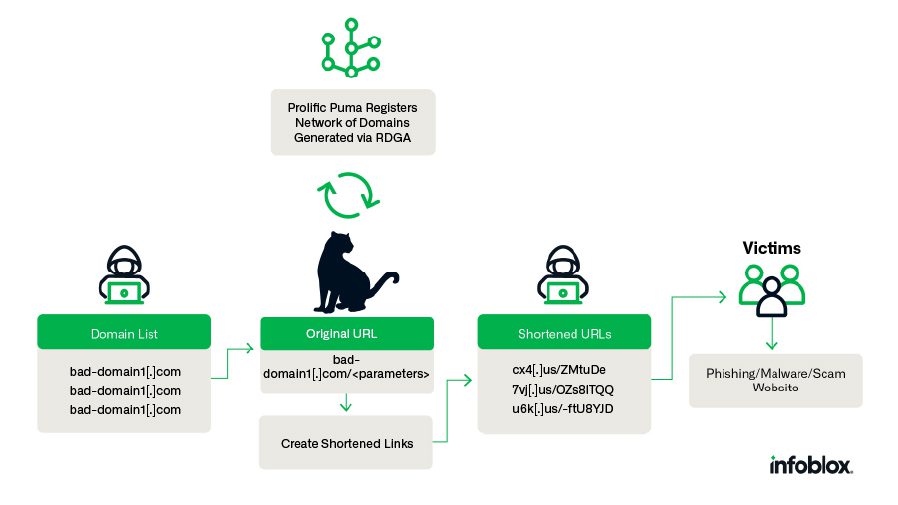
An overview of Prolific Puma’s role in the cybercrime supply chain.
A study by Infoblox revealed that the United States’ top-level domain (TLD) – .US – has become a hotspot for the registration of thousands of domains linked to a malicious link-shortening service. This service is employed for fraud and malware dissemination. This revelation follows a report that identified .US domains as among the most frequently used in phishing attacks over the past year.
Researchers at Infoblox have been monitoring this link-shortening service for three years. It was ascertained that these fraudulent domains typically range between 3 to 7 characters in length and are hosted on bulletproof hostings – platforms notorious for dismissing any content-related grievances or legal claims. While these shortened domains don’t host the content themselves, they obscure the actual addresses of phishing landing pages, crafted to deceive users or deploy malware.

How these malevolent pages propagate remains unclear, but suspicions suggest the primary method might be through SMS-based scams. Infoblox was able to delineate the service’s contours thanks to pseudorandom patterns in short domains, which at first glance appear as a nonsensical amalgamation of letters and numbers. Domain name generation algorithms were employed for this detection process.
The researchers christened the link-shortening service as “Prolific Puma”. It was determined that until May 2023, new malicious domain registrations predominantly occurred through .info domains via Prolific Puma. Since then, it has been discerned that those behind the service use .US for 55% of their domain registrations, with dozens of new malicious .US domains being registered daily.
The .US domain is overseen by the National Telecommunications and Information Administration (NTIA). However, over time, stewardship of the .US domains was delegated to various private entities, leading the primary US domain to become a quagmire of phishing activities.