inhale: malware analysis and classification tool
Inhale – Malware Inhaler
Inhale is a malware analysis and classification tool that is capable of automating and scaling many static analysis operations.
Inhale started as a series of small scripts that I used when collecting and analyzing a large amount of malware from diverse sources. There are plenty of frameworks and tools for doing similar work, but none of them really matched my workflow of quickly finding, classifying, and storing information about a large number of files. Some also require expensive API keys and other services that cost money.
Data Model
The following is the current data model used for the elasticsearch database. Not every one of these will be used for every given file. Any r2_* tags are typically reserved for binaries of some sort.
| Name | Description |
|---|---|
| filename | The full path of the binary |
| file_ext | The file extension |
| filesize | The file size |
| filetype | Filetype based on magic value. Not as reliable as binwalk signatures. |
| md5 | The files MD5 hash |
| sha1 | The files SHA1 hash |
| sha256 | The files SHA256 hash |
| added | The date the file was added |
| r2_arch | Architecture of the binary file |
| r2_baddr | The binary’s base address |
| r2_binsz | The size of the program code |
| r2_bits | Architecture bits – 8/16/32/64 etc. |
| r2_canary | Whether or not stack canaries are enabled |
| r2_class | Binary Class |
| r2_compiled | The date that the binary was compiled |
| r2_dbg_file | The debug file of the binary |
| r2_intrp | The interpreter that the binary calls if dynamically linked |
| r2_lang | The language of the source code |
| r2_lsyms | Whether or not there are debug symbols |
| r2_machine | The machine type, usually means the CPU the binary is for |
| r2_os | The OS that the machine is supposed to run on |
| r2_pic | Whether or not there is Position Independent Code |
| r2_relocs | Whether or not there are relocations |
| r2_rpath | The run-time search path – if applicable |
| r2_stripped | Whether or not the binary is stripped |
| r2_subsys | The binary’s subsystem |
| r2_format | The binary format |
| r2_iorw | Whether ioctl calls are present |
| r2_type | The binary type, whether or not it’s an executable, shared object etc. |
| yara | Contains a list of yara matches |
| binwalk | Contains a list of binwalk signatures and their locations in the binary |
| tags | Any user defined tags passed with the -t flag. |
| url | The origin url if a file was remotely downloaded |
| urls | Any URLs that have been pulled from the binary |
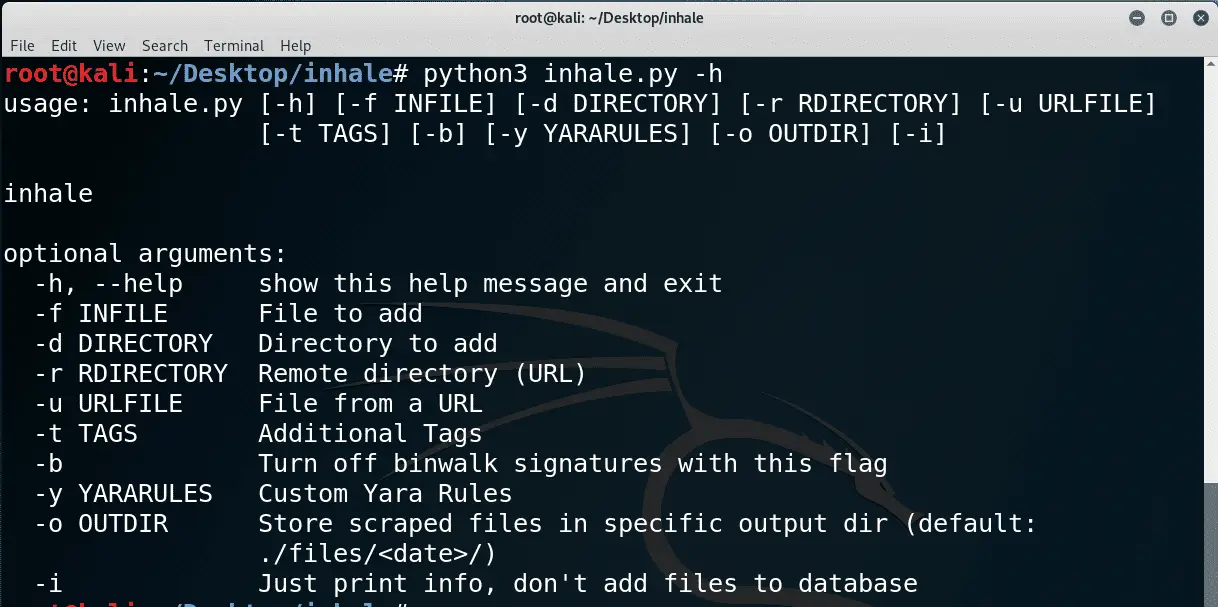
Install & Use
Author: @netspooky




