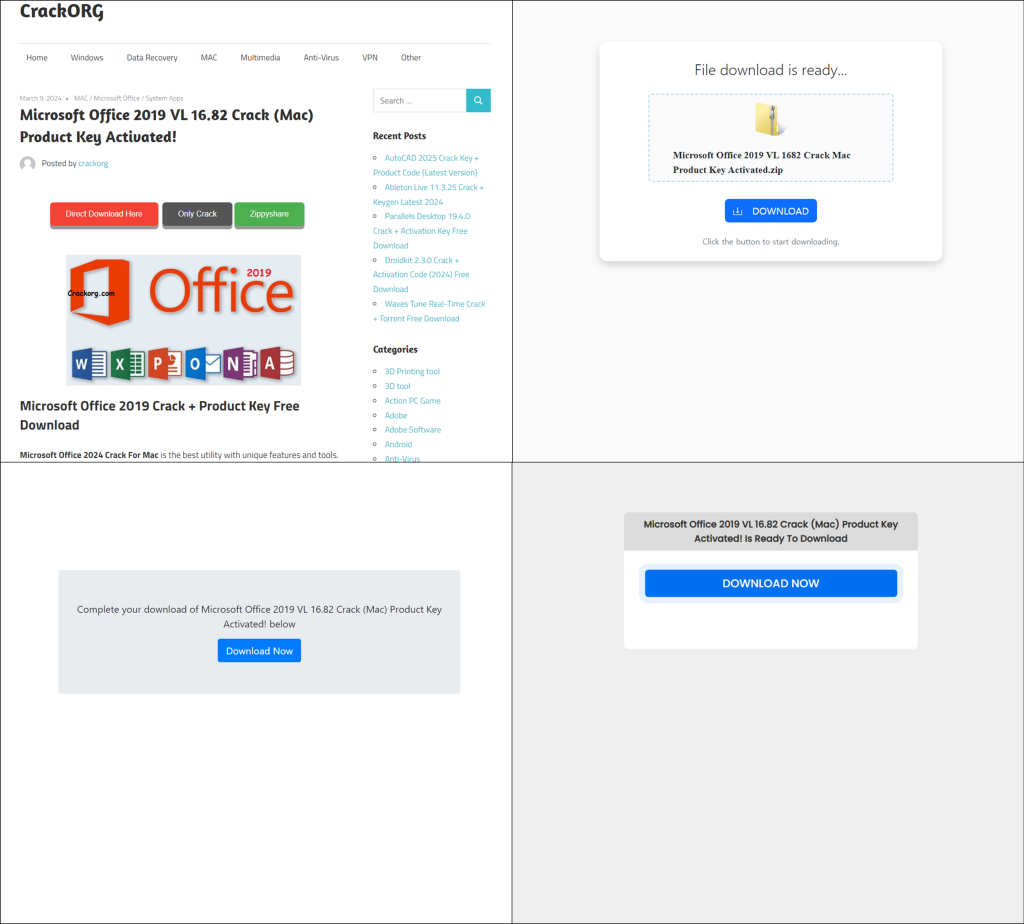
Webpages distributing the malware
The AhnLab Security Intelligence Center (ASEC) has issued a warning about a new breed of malware that disguises itself as cracked software and legitimate tools. This malware, dubbed “InnoLoader,” is far from ordinary. Unlike traditional malware that activates upon execution, InnoLoader lurks within the installation process, waiting for unsuspecting users to click through the installer’s interface before unleashing its malicious payload.

Unlike traditional malware, which often includes precompiled malicious code, this new strain, referred to as “InnoLoader,” creates a unique malware instance each time a download request is made. This dynamic generation process results in each malware sample having a different hash value but maintaining the same malicious functionality, making detection and tracking significantly more challenging for cybersecurity defenses.
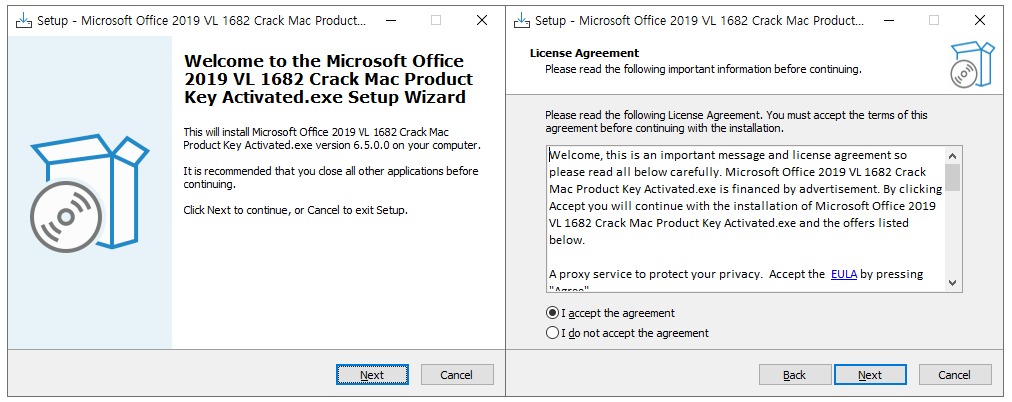
The malware cleverly disguises itself by presenting an installer user interface (UI). Malicious behaviors are triggered only when the user interacts with the installer, such as clicking “Next” during the installation process. This deceptive approach not only lures users into a false sense of security but also complicates the detection of malicious activities.
How the Malware Operates
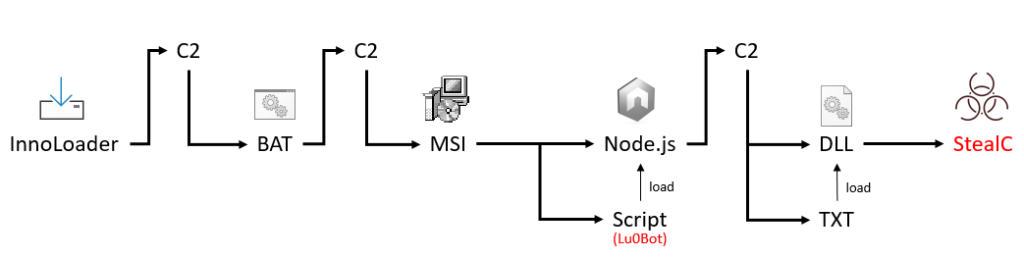
- Download and Execution: When a user requests a download, a unique malware instance is generated and delivered. Upon execution, an installer UI is displayed, masking the underlying malicious intent.
- Command and Control (C2) Communication: The malware communicates with a command and control server (C2), downloading and executing additional files based on the server’s responses. The response from the C2 dictates whether the installation will proceed with malicious activities or terminate without incident to evade detection.
- Multiple Malicious Components: The investigation revealed that the malware could download various malicious components, including:
- Infostealer StealC: Designed to exfiltrate sensitive information such as passwords and cryptocurrency wallet details.
- Socks5Systemz: Utilizes infected systems as commercial proxy resources.
- Clicker: A disguised browser plugin that artificially increases views.
- Adware and Other Malicious Tools: Various adware and potentially harmful programs disguised as legitimate software like the Opera browser and 360 Security products.
To hinder analysis and detection, the malware employs several sophisticated techniques:
- Timestamp and Country Information: Each download request includes a timestamp and country information, ensuring the creation of a new, unique malware sample each time.
- Legitimate Software Camouflage: In environments with a history of previous malware downloads, the system may temporarily deliver legitimate software (e.g., WinRAR) to avoid raising suspicion.
- Complex Execution Flow: The malware executes through a multi-step process, often involving obfuscated scripts and temporary files to complicate forensic analysis.
Users are strongly advised to exercise caution, avoid pirated software, and keep their security solutions up to date.