Image: Sekoia
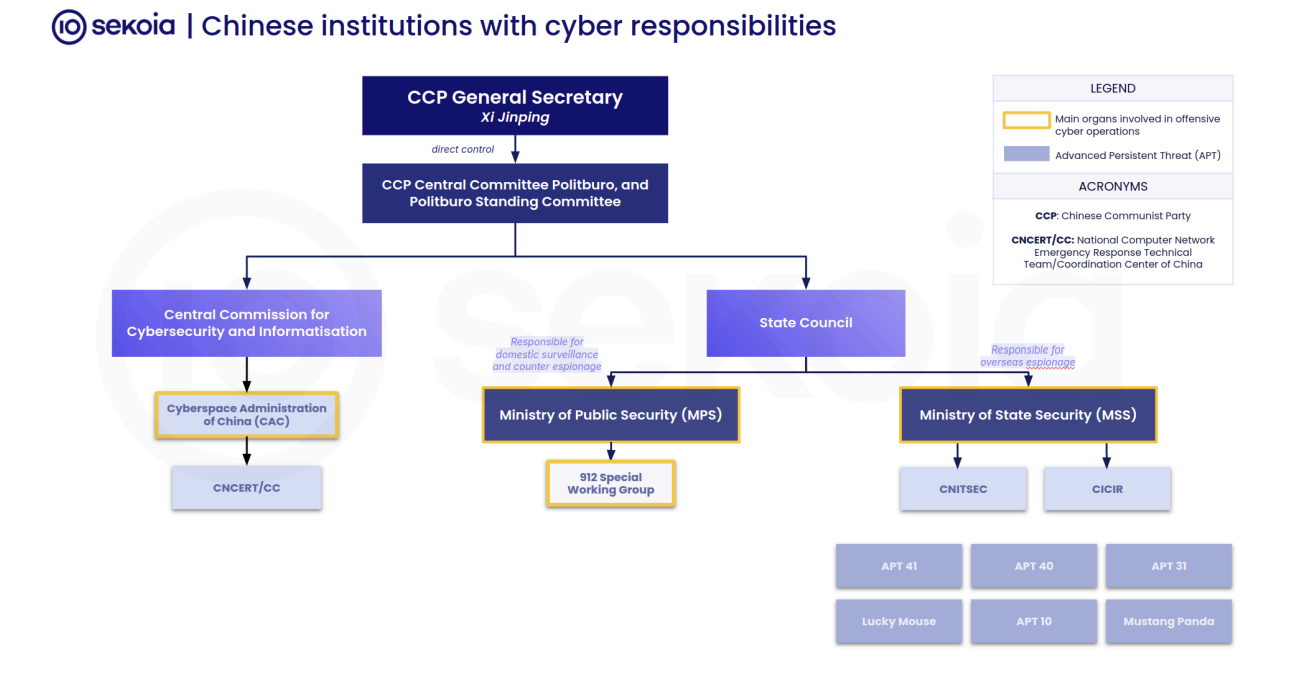
In a recent report, the Sekoia TDR team, in collaboration with cybersecurity expert Coline Chavane, dives deep into the intricacies of China’s state-sponsored cyber operations in their latest report, “A Three-Beat Waltz: The Ecosystem Behind Chinese State-Sponsored Cyber Threats.” The analysis reveals the synchronized efforts of state, military, and civilian actors orchestrated by the Chinese Communist Party (CCP) to form a robust cyber-espionage ecosystem.
The report identifies three main pillars driving China’s cyber-espionage activities: the People’s Liberation Army (PLA), the Ministry of State Security (MSS), and the Ministry of Public Security (MPS). These entities operate with distinct yet complementary roles. While the PLA has historically conducted cyber operations as part of China’s military initiatives, a strategic shift has seen the MSS taking a leading role. “From 2021 onward, operations attributed to China were mostly linked to the Ministry of State Security (MSS) rather than the People’s Liberation Army (PLA),” notes the report.
The PLA, equipped with sophisticated cyber capabilities, focuses on information superiority, a critical doctrine in modern warfare. The MSS, meanwhile, leverages its vast network of provincial branches and partnerships with private companies to carry out espionage and counterintelligence missions. This shift in responsibility underscores a trend where “state actors increasingly outsource cyber offensive capabilities to private entities,” a tactic used to obfuscate direct government involvement.
China’s offensive cyber strategy extends beyond formal government and military channels. Since the 1990s, patriotic hacker communities have supported state operations by attacking foreign targets. Initially, these groups acted independently, launching cyberattacks driven by nationalism.
Over time, however, the CCP harnessed these talents, integrating them into state-sponsored operations. This integration, known as Military-Civil Fusion (MCF), allowed China to tap into the skills of private sector experts, providing an efficient means of advancing their cyber capabilities. “This proximity was encouraged by the policies of Xi Jinping, who made Military-Civil Fusion (MCF) a national strategy in 2015,” the report adds.
One of the report’s more alarming findings is the hack-for-hire ecosystem in China, where government agencies contract private companies to conduct cyber operations. The I-SOON leaks, which disclosed internal documents from the Chinese IT company I-SOON, illustrate how private contractors are vital in China’s cyber strategy. “State actors subcontract cyber offensive services at the provincial and the city levels,” the report reveals, underscoring the autonomous capabilities of regional actors within the MSS and MPS.
Through hacking contests like the Tianfu Cup, vulnerabilities discovered by civilian hackers are weaponized and distributed among these contractors. This centralization of vulnerability reporting and exploitation aligns with CCP’s regulations that prevent Chinese cybersecurity researchers from sharing their findings internationally, ensuring that valuable zero-days remain within China’s arsenal.
Sekoia’s analysis provides a sobering perspective on the evolving cyber threat landscape posed by China. The complexity of China’s cyber-espionage ecosystem—melding state, military, and private entities into a coordinated threat—demands a reassessment of cybersecurity measures. “A China-nexus APT is likely to be a mix of private and state actors cooperating to conduct operations,” the report suggests, highlighting the blurred lines that complicate attribution.
Related Posts:
- North Korean Hackers Exploit Old Office Flaw to Deploy Keylogger
- Canadian Organizations Targeted by Chinese State-Sponsored Scanning
- North Korea Targets DeFi and Crypto Companies with Advanced Social Engineering Attacks
- North Korean Hacker Indicted: Ransomware on Hospitals Funds Military Espionage