Details and proof-of-concept (PoC) exploit code have emerged about a now-patched security flaw, CVE-2024-20656, in Microsoft Visual Studio that could be abused by a threat actor to gain elevated privileges on affected systems.
The vulnerability is rated 7.8 for severity and concerns an elevation of privilege bug in the VSStandardCollectorService150 service which is used for diagnostic purposes by Visual Studio and is running in NT AUTHORITY\SYSTEM context.
“An attacker who successfully exploited this vulnerability could gain SYSTEM privileges,” Microsoft disclosed in an advisory issued this month as part of Patch Tuesday updates.
Security researcher Filip Dragović was credited with discovering and reporting the flaw.

CVE-2024-20656 is not just another bug in the system; it is an elevation of privilege vulnerability that resides in the VSStandardCollectorService150 service. This service, essential for diagnostic purposes in Visual Studio, runs in the highly privileged NT AUTHORITY\SYSTEM context.
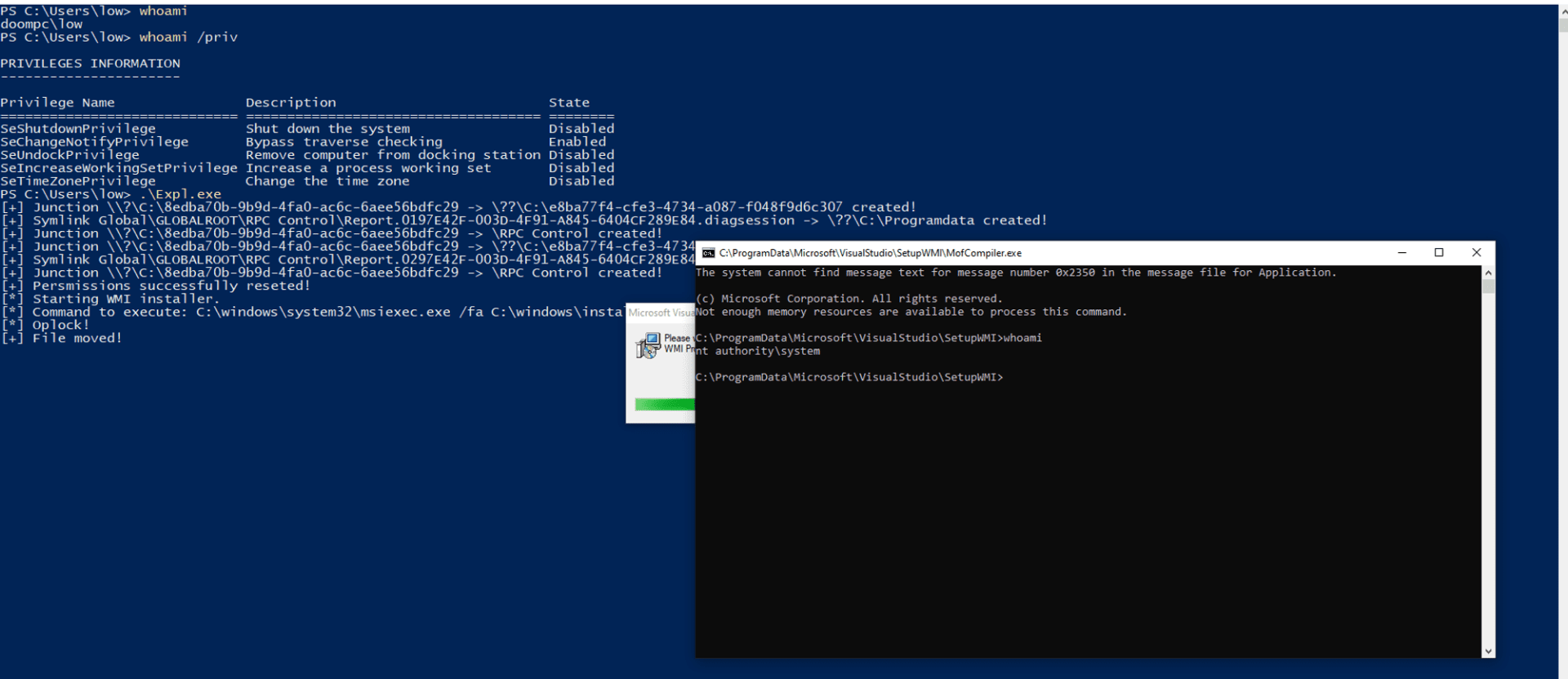
Filip Dragović who released the PoC, said CVE-2024-20656 is rooted in the fact that “the VSStandardCollectorService150 service which used for diagnostic purposes by Visual Studio and is running in NT AUTHORITY\SYSTEM context, and how it can be abused to perform arbitrary file DACL reset in order to escalate privileges.”
The exploitation of this vulnerability begins with the creation of a dummy directory where the VSStandardCollectorService150 writes files. This is followed by a series of calculated maneuvers involving the creation of junction directories, triggering of the service, and manipulation of symbolic links. The final stroke involves replacing a critical binary with a commandeered version, granting the attacker a SYSTEM shell. The proof-of-concept exploit code is available on Github.
Microsoft, understanding the gravity of this issue, issued a patch as part of their Patch Tuesday updates. However, the existence of such a flaw in a widely used IDE like Visual Studio raises important questions about software security, especially considering its usage in sensitive and high-security environments.