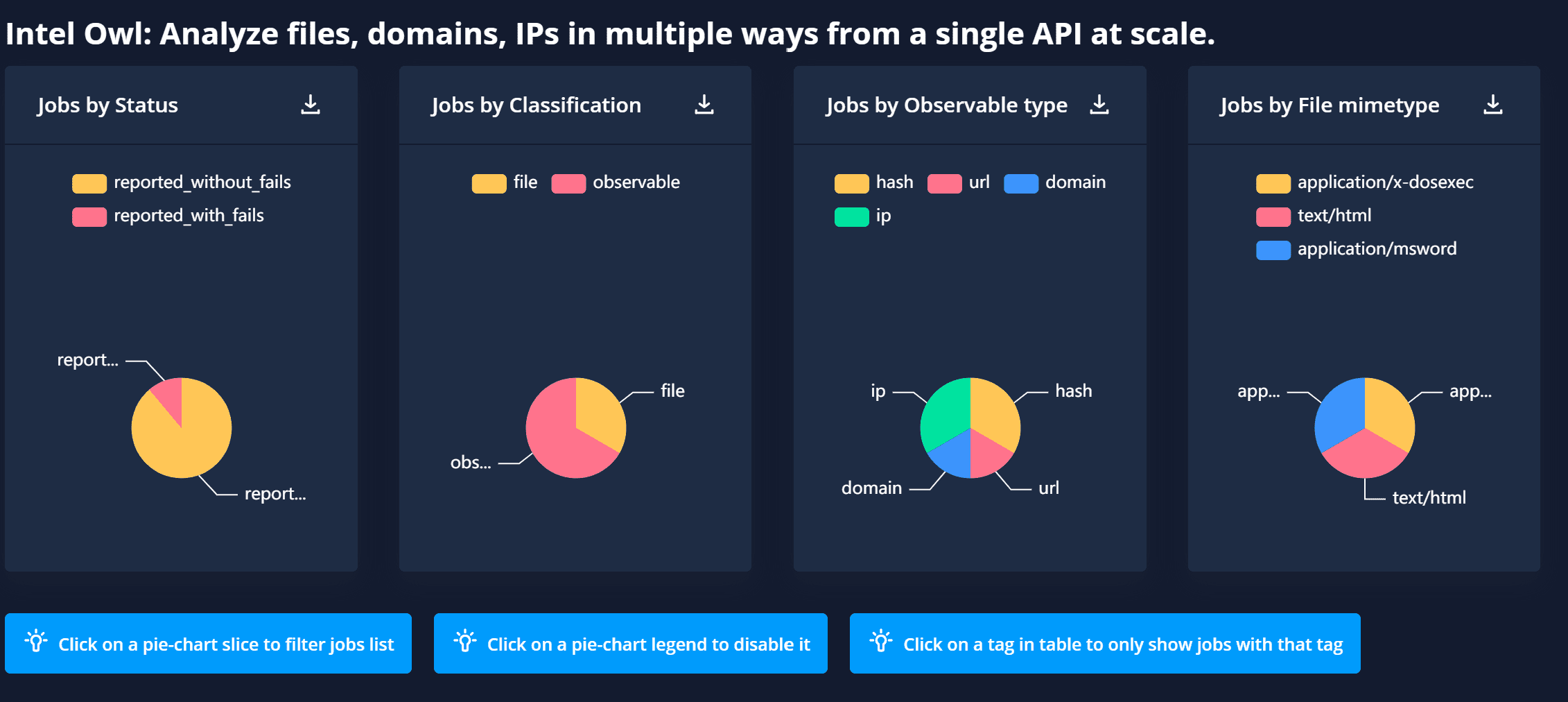
Intel Owl v5.2.2 releases: analyze files, domains, IPs in multiple ways

Intel Owl
Do you want to get threat intelligence data about a file, an IP, or a domain?
Do you want to get this kind of data from multiple sources at the same time using a single API request?
You are in the right place!
This application is built to scale out and to speed up the retrieval of threat info.
It can be integrated easily in your stack of security tools to automate common jobs usually performed, for instance, by SOC analysts manually.
Intel Owl is composed of analyzers that can be run to retrieve data from external sources (like VirusTotal or AbuseIPDB) or to generate intel from internal analyzers (like Yara or Oletools)
This solution is for everyone who needs a single point to query for info about a specific file or observable (domain, IP, URL, hash).
Features
- Provides enrichment of threat intel for malware as well as observables (IP, Domain, URL, and hash).
- This application is built to scale out and to speed up the retrieval of threat info.
- It can be integrated easily in your stack of security tools (pyintelowl) to automate common jobs usually performed, for instance, by SOC analysts manually.
- Intel Owl is composed of analyzers that can be run to retrieve data from external sources (like VirusTotal or AbuseIPDB) or to generate intel from internal analyzers (like Yara or Oletools)
- API is written in Django and Python 3.7.
- Inbuilt frontend client: IntelOwl-ng provides features such as dashboard, visualizations of analysis data, easy to use forms for requesting new analysis, etc. Live Demo.
Available services or analyzers
You can see the full list of all available analyzers in the documentation or live demo.
| Inbuilt modules | External Services | Free modules that require additional configuration |
|---|---|---|
| – Static Document, RTF, PDF, PE, Generic File Analysis – Strings analysis with ML – PE Emulation with Speakeasy – PE Signature verification – PE Capabilities Extraction – Emulated Javascript Analysis – Android Malware Analysis – SPF and DMARC Validator – more… |
– GreyNoise v2 – Intezer Scan – VirusTotal v2+v3 – HybridAnalysis – Censys.io – Shodan – AlienVault OTX – Threatminer – Abuse.ch – many more.. |
– Cuckoo (requires at least one working Cuckoo instance) – MISP (requires at least one working MISP instance) – Yara (Community, Neo23x0, Intezer and McAfee rules are already available. There’s the chance to add your own rules) |
Changelog v5.2.2
Main Improvements
- Added new analyzers for DNS0 PassiveDNS data
- Added the chance to collect metrics (Business Intelligence regarding Plugins Usage and send it to an ElasticSearch instance.
- Added new buttons to test “Healthcheck” and “Pull” operations for each Plugin (A feature introduced in the previous version)
Other improvements
- Various generic fixes and adjustments in the GUI
- dependencies upgrades
- adjusted contribution guides
Install && Use
Copyright (C) 2019 Matteo Lodi