CTFTOOL
ctftool is an interactive command-line tool to experiment with CTF, a little-known protocol used on Windows to implement Text Services. This might be useful for studying Windows internals, debugging complex issues with Text Input Processors and analyzing Windows security.
It is possible to write simple scripts with ctftool for automating interaction with CTF clients or servers or perform simple fuzzing.
Edit Session Attacks
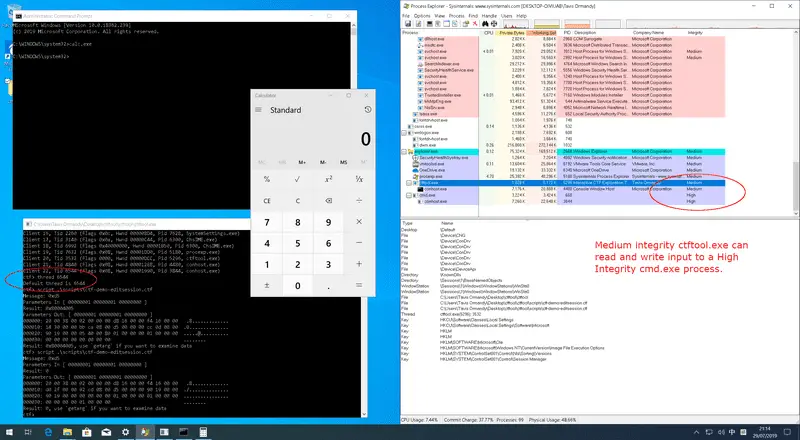
Apart from memory corruption, a major vulnerability class exposed by CTF are edit session attacks. Normally, an unprivileged process (for example, low integrity) would not be permitted to send input or read data from a highly privileged process. This security boundary is called UIPI, User Interface Privilege Isolation.
CTF breaks these assumptions and allows unprivileged processes to send input to privileged processes.
There are some requirements for this attack to work, as far as I’m aware it will only work if you have a display language installed that uses an OoP TIP, out-of-process text input processor. Users with input languages that use IMEs (Chinese, Japanese, Korean, and so on) and users with a11y tools fall into this category.
Example attacks include…
- Sending commands to an elevated command window.
- Reading passwords out of dialogs or the login screen.
- Escaping IL/AppContainer sandboxes by sending input to unsandboxed windows.
There is an example script in the scripts directory that will send input to a notepad window to demonstrate how to edit sessions work.
Use
Copyright (C) 2019 Tavis Ormandy taviso@gmail.com