Image Source
Introduction
Imagine for a second that everyone who walks into your bank can go anywhere within the bank—the control room, the manager’s office, the vault, etc.—without being stopped by anyone. Sounds weird, right? I doubt anyone would patronize such a bank, and it would be mostly on the grounds of security. The bank wouldn’t feel secure enough to most people.
As a result of digitization, which is becoming an increasingly critical part of how the world functions, the average netizen expects software solutions and digital infrastructure to be as secure as a bank vault. The premise of this expectation is based on the fact that our financial information and other personal data is stored online, and a data breach can prove rather costly to every stakeholder.
Let us look at an example that’s closer to home. On the internet, when you log in to Facebook, there is code written to ensure that the only way a person can access your account is by having your username and password. Even if someone else has the URL link to your profile, the person cannot edit your profile without logging in to your account.
If someone gains unauthorized access to your profile or messages because they have the URL link (without being signed in to your profile), then we have a case of broken access control. This seems rather harmless until you imagine a situation where someone can control your PayPal account because they typed in the URL that accesses your PayPal account.
Cybersecurity is a growing concern for both owners of digital infrastructure and users of these infrastructures. To help people mitigate cybersecurity risks, a list of the most likely cybersecurity threats has been collated by OWASP (Open Web Application Security Project): OWASP Top 10.
The OWASP Top 10 serves as a guideline for developers of the risks they should protect themselves against to create a stronger software solution.
Image Source
Broken Access Control And How to Avoid It
Access control is often used interchangeably with authorization—they both control the rights and privileges of a user by leveraging the utilities of digital infrastructure. As netizens, we access different platforms where we are able to do certain things depending on whether we’re premium or basic members, users or admin members, and these privileges keep us in check.
If we’re unable to prevent people from gaining access to resources and utilities that they have no right to be using, we’re dealing with broken access control. With cybercrime increasing by 600% during the COVID-19 pandemic, developers have an implicit and explicit burden to protect users as much as possible.
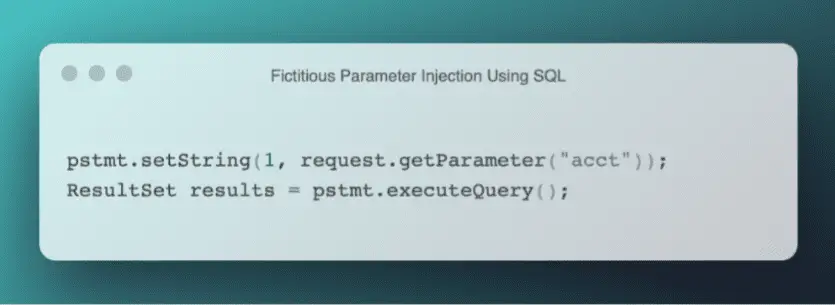
Broken access control involves injecting fictitious parameters (basically unverified data) using SQL (structured query language) into a software solution that interacts with a database to compromise the entire digital infrastructure and gain unlawful access to private data. An example is shown in the code below.
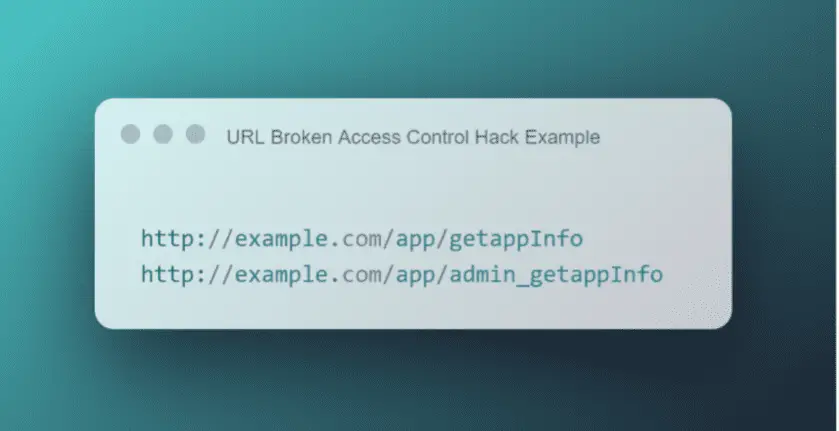
More often than not, broken access control usually involves inserting URL queries or strings aimed at gaining access to poorly protected user accounts, admin features, and resources. By understanding the process of building APIs and routing parameters, it’s possible for hackers to use particular queries (an example of which is shown below) maliciously.
Risk Mitigation
OWASP, among other notable entities, has suggested numerous ways in which one can guard against broken access control, some of which are:
- Reducing reliance on names for routes and using key-value pairs instead. as they’re less easy to predict.
- Ensuring web pages don’t have predictable names, which, like the previous suggestion points out, helps prevent URL path guesses that can compromise the security of your platform.
- Making sure all web pages (depending on the nature of the platform) have authentication checks.
- Customizing exceptions and error codes, making them harder to guess for hackers.
- Denying access to all functionalities on a platform by default makes it harder for hackers to gain unauthorized access to features simply by having a URL trigger.
- Leveraging access control and role-based authentication systems to ensure that permissions and privileges depend on the nature of a user on the platform.
- Avoiding the use of secrecy as the only protection for functions, URLs, and users on a platform.
- Giving users just enough privileges to carry out the activities assigned to their role.
Final Thoughts
Broken access control is a real threat that most people don’t think of because they feel it’s too simplistic for hackers to use. While broken access control seems like a no-brainer trick, it is difficult to guard against completely. Thus, software developers must pay attention to the process of authorization and authentication of users to ensure that neither the admin nor users can be compromised by parlor tricks like broken access control. Defining user roles and ensuring that these are specific enough to make sure that no user has more access than they require are great ways of ensuring that people are unable to break access privileges.