ioc2rpz
Overview
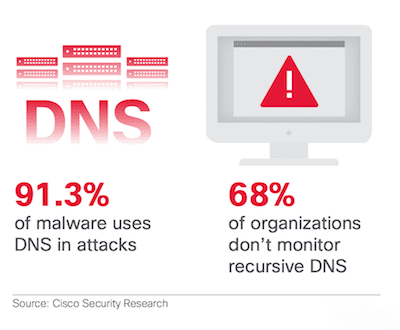
DNS is the control plane of the Internet. Usually, DNS is used for good but:
- It can be used to track users locations and their behavior;
- Malware uses DNS to command and control, exfiltrate data or redirect traffic;
- According to with 2016 Cisco annual security report, 91.3% of malware use DNS;
- Advertisements companies usually use separate and obscure domains to show ads;
- Free DNS services (e.g. 1.1.1.1, 8.8.8.8, 9.9.9.9, etc) can help you to address some concerns but you can not define your own protection settings or ad filters.
ISC Bind is a de facto a standard of a nameserver. With the introduction of Response Policy Zones in the ISC BIND 9.8, it is became a simple task to monitor and contain malware on the DNS layer. RPZ is supported on PowerDNS recursor 4.0.0 and later releases. Knot DNS is also partially supported RPZ.
In comparing with traditional network protection solutions a DNS server can handle millions of indicators without performance impact but there was no automated and efficient way to maintain response policy zones on primary DNS servers.
Usually, indicators of compromise are distributed in plain text but in different formats and only a few providers of IOCs make them available via RPZ.
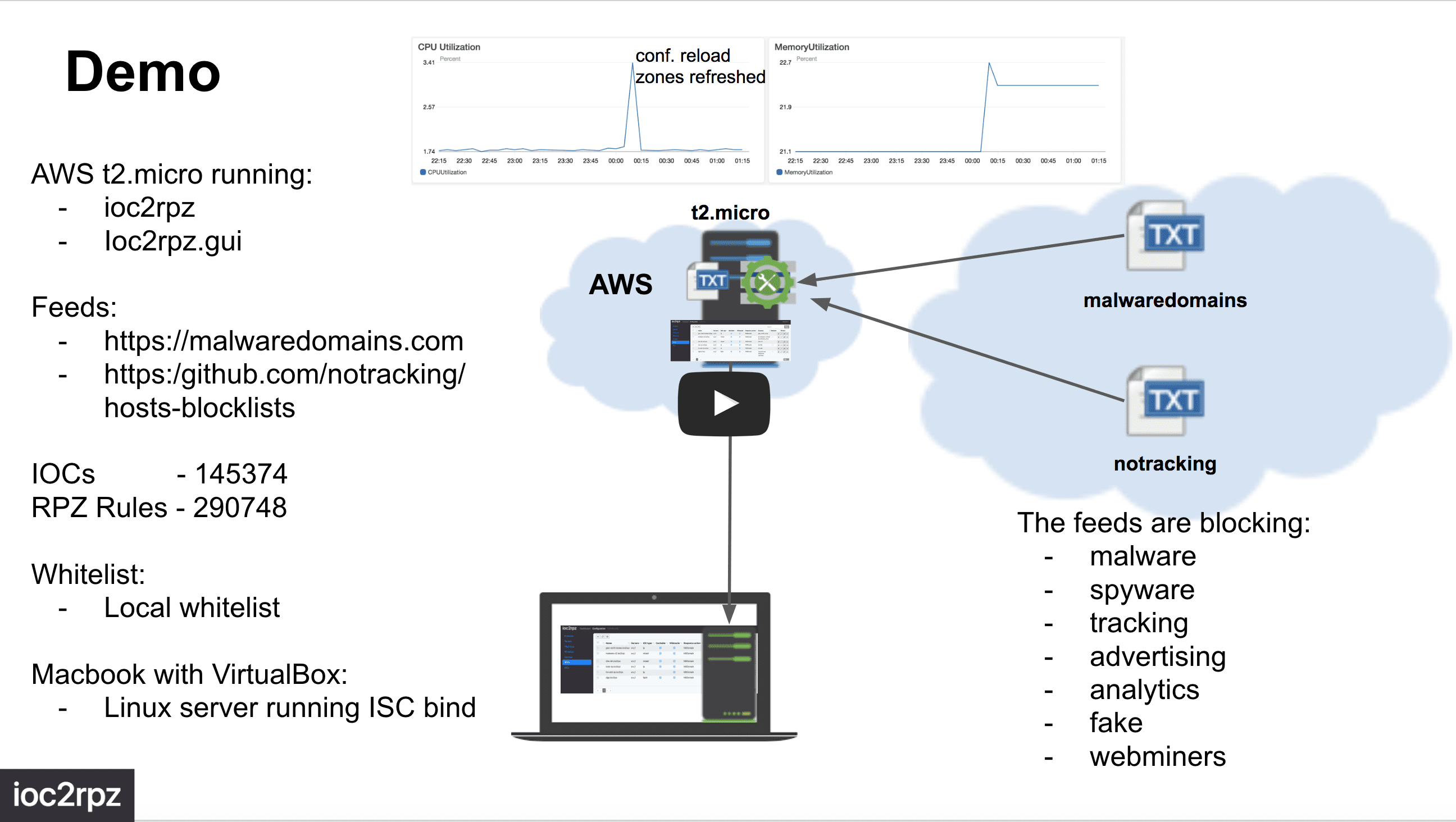
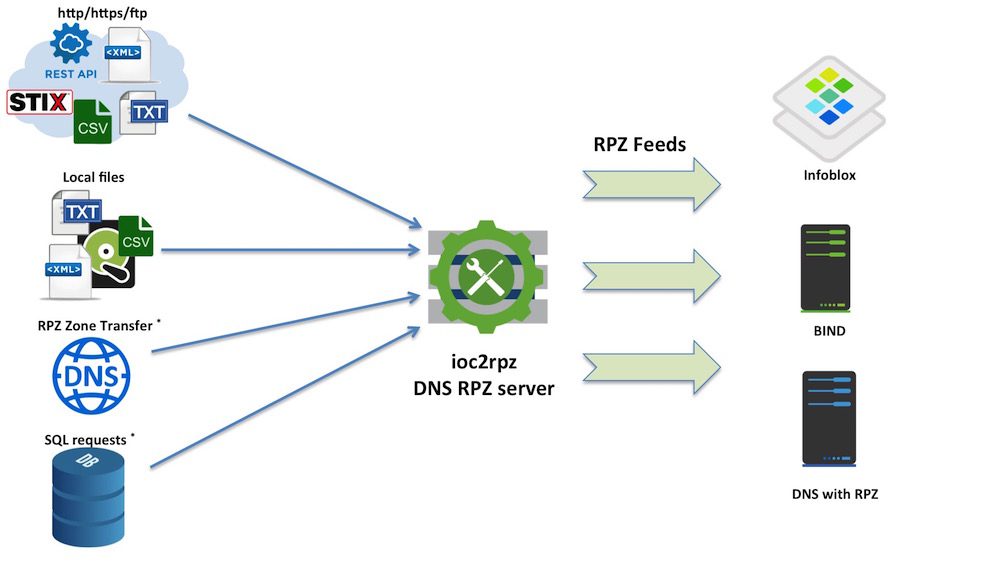
ioc2rpz is a custom DNS server which automatically converts indicators (e.g. malicious FQDNs, IPs) from various sources into RPZ feeds and automatically maintains/updates them. The feeds can be distributed to any open source and/or commercial DNS servers which support RPZ, e.g. ISC Bind, PowerDNS. You can run your own DNS server with RPZ filtering on a router, desktop, server, and even Arduino. System memory is the only limitation.
With ioc2rpz you can define your own feeds, actions and prevent undesired communications.
ioc2rpz is a place where threat intelligence meets DNS
ioc2rpz transforms IOC feeds into response policy zones (RPZ). You can mix feeds to generate a single RPZ or multiple RPZs. Trusted domains and IPs can be whitelisted. ioc2rpz supports expiration of indicators and accordingly rebuilds zones.
 The current release supports local files, files/requests via http/https/ftp and shell scripts to access other resource types. You can use any file format if you can write a REGEX to extract indicators and indicators are separated by a newline or/and return carriage chars (/n, /r, /r/n).
The current release supports local files, files/requests via http/https/ftp and shell scripts to access other resource types. You can use any file format if you can write a REGEX to extract indicators and indicators are separated by a newline or/and return carriage chars (/n, /r, /r/n).
How to use ioc2rpz
You can use ioc2rpz with any DNS server which supports Response Policy Zones e.g. recent versions of ISC BIND, PowerDNS and any commercial DNS server based on these products (e.g. Infoblox, Blue Cat, Efficient IP). A sample bind’s configuration file (named.conf) is provided in the cfg folder.
ioc2rpz web interface
ioc2rpz.gui is a Management Web interface which is developed as a separate project. It is not required to run ioc2rpz.
DNS over TLS (DoT)
ioc2rpz supports RPZ distribution over DoT. The SSL listener service is automatically started on port 853 (PortTLS) if a certificate is provided in the configuration (cert). The current implementation has the following limitations:
- TLS 1.2 only;
- single request per session;
- TLS PIN is not supported;
- DNS Notify messages are unencrypted. When a certificate is expired or is going to expire soon there is no need to restart service if new certificates were saved in the same file. Erlang automatically updates certificates if files were replaced. The delay may be up to 2 minutes because of caching. It is recommended do not let the certificate to expire for service continuity.
ioc2rpz vs ISC BIND vs other DNS:
- ioc2rpz was built to handle RPZ distribution only;
- ioc2rpz supports DoT (DNS over TLS) so nobody can easily eavesdrop on your RPZs/indicators;
- ioc2rpz supports as many RPZs as you need;
- ioc2rpz supports live/non-cached zones. It creates zones by an incoming request;
- indicators can be pulled from different sources and via different protocols (e.g. via REST API calls);
- RPZs are automatically updated;
- IOC expiration time is used to remove expired indicators in a timely manner;
- Performance and zone transfer time/size/packets optimizations.
Changelog v1.2.0.3
- Many minor enhancements and bug fixes
Install && Use
Copyright 2019 Vadim Pavlov