ioctlance: detect various vulnerability types in Windows Driver Model (WDM) drivers
IOCTLance
Presented at CODE BLUE 2023, this project titled Enhanced Vulnerability Hunting in WDM Drivers with Symbolic Execution and Taint Analysis introduces IOCTLance, a tool that enhances its capacity to detect various vulnerability types in Windows Driver Model (WDM) drivers. In a comprehensive evaluation involving 104 known vulnerable WDM drivers and 328 unknown ones, IOCTLance successfully unveiled 117 previously unidentified vulnerabilities within 26 distinct drivers. As a result, 41 CVEs were reported, encompassing 25 cases of denial of service, 5 instances of insufficient access control, and 11 examples of elevation of privilege.
Features
Target Vulnerability Types
- map physical memory
- controllable process handle
- buffer overflow
- null pointer dereference
- read/write controllable address
- arbitrary shellcode execution
- arbitrary wrmsr
- arbitrary out
- dangerous file operation
Optional Customizations
- length limit
- loop bound
- total timeout
- IoControlCode timeout
- recursion
- symbolize data section
Build
Docker
git clone https://github.com/zeze-zeze/ioctlance.git
docker build .
Local
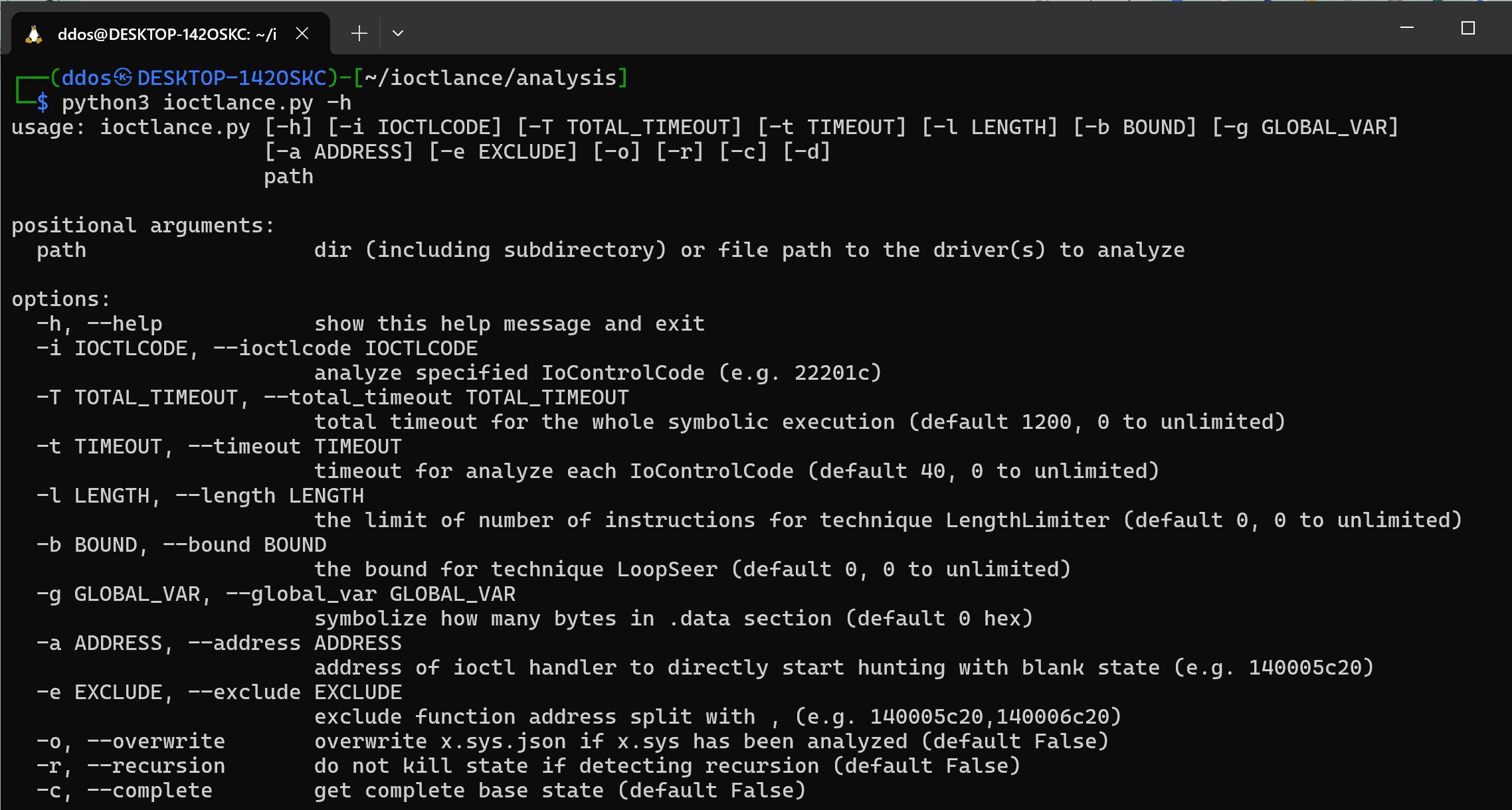
Use
Analysis

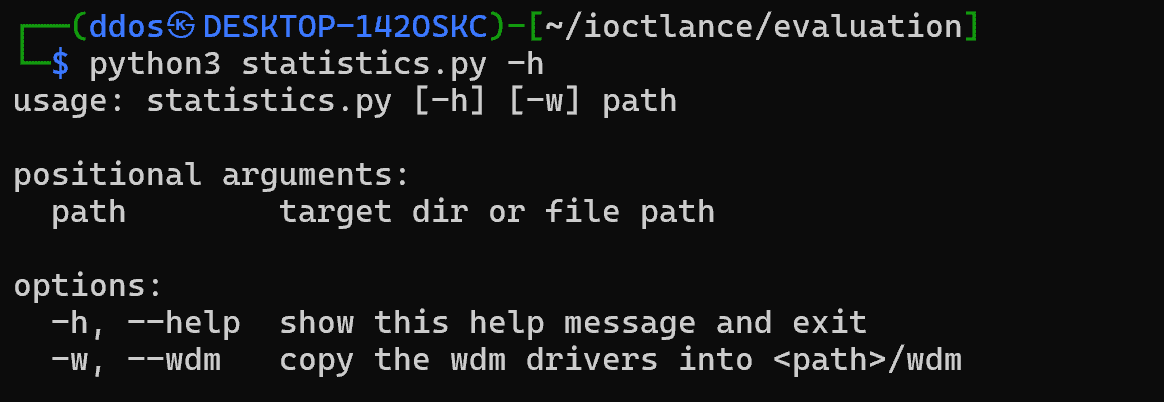
Evaluation
Copyright (C) 2023 zeze-zeze
Source: https://github.com/zeze-zeze/