ipv4Bypass: Using IPv6 to Bypass Security
ipv4Bypass
Using IPv6 to Bypass Security
how the tool works
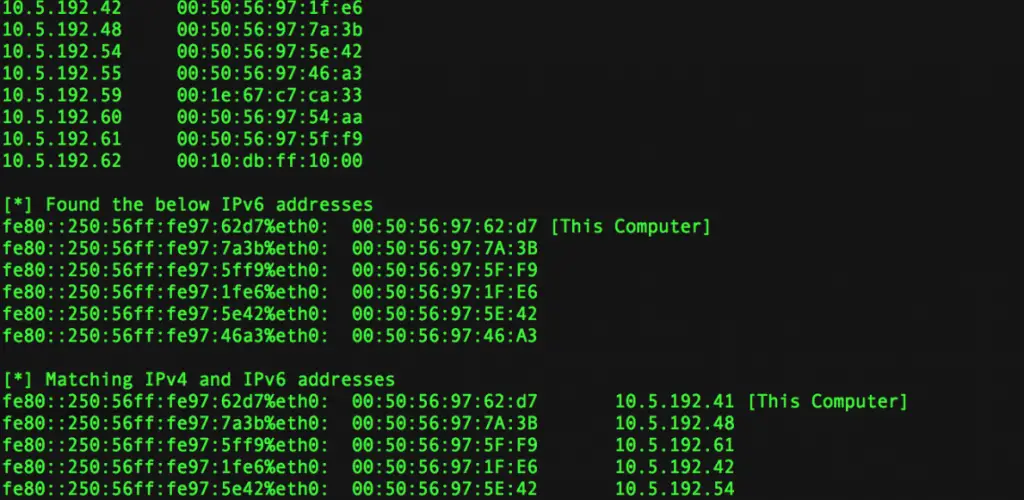
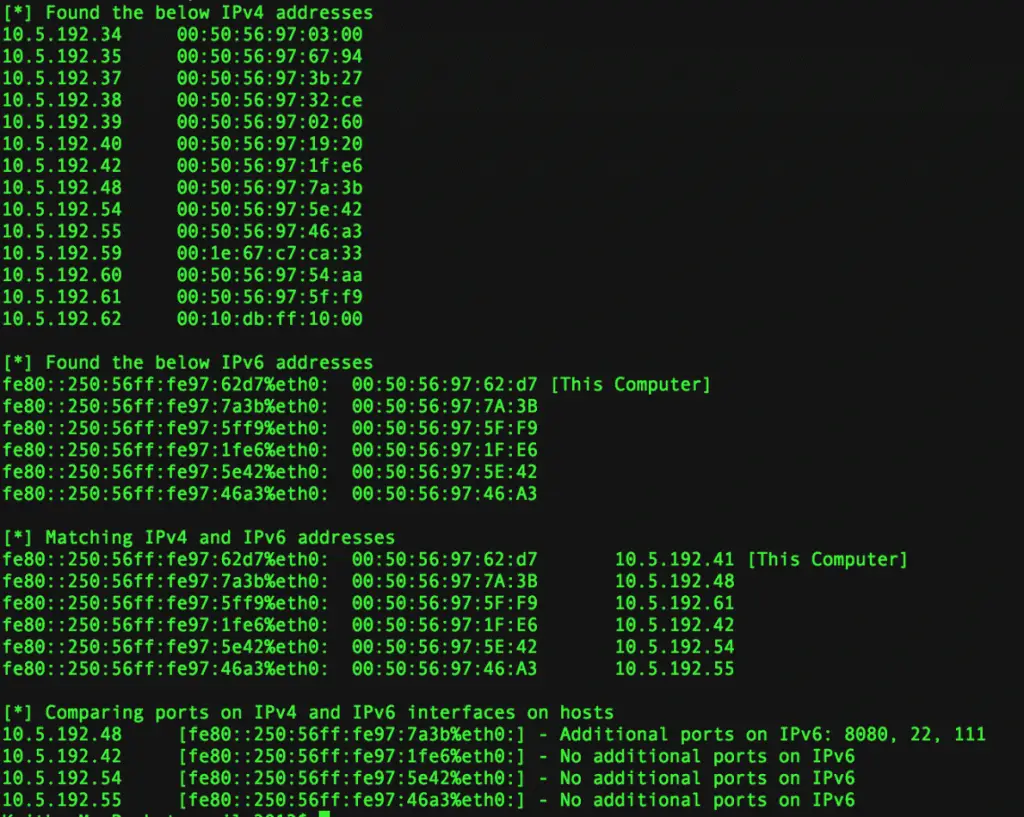
1) Sends an ICMP echo request (ping6 ff02::1%eth0) to the broadcast address (ff02::1), all IPv6 hosts in the local network will reply
2) Sends an ARP requests to all IPv4 hosts in the local network
3) Performs a port scan of all IPv4 and IPv6 hosts that are alive in the local network
4) Match the IPv6 address to the IPv4 address based on the MAC address information.
5) Checks to see if the scan against the IPv6 address on the host returns more open ports that the IPv4 address on the same host and outputs the difference in ports (if any)
See here for an explanation of the technique.
Download
git clone https://github.com/milo2012/ipv4Bypass.git
Use
Source: https://github.com/milo2012/






