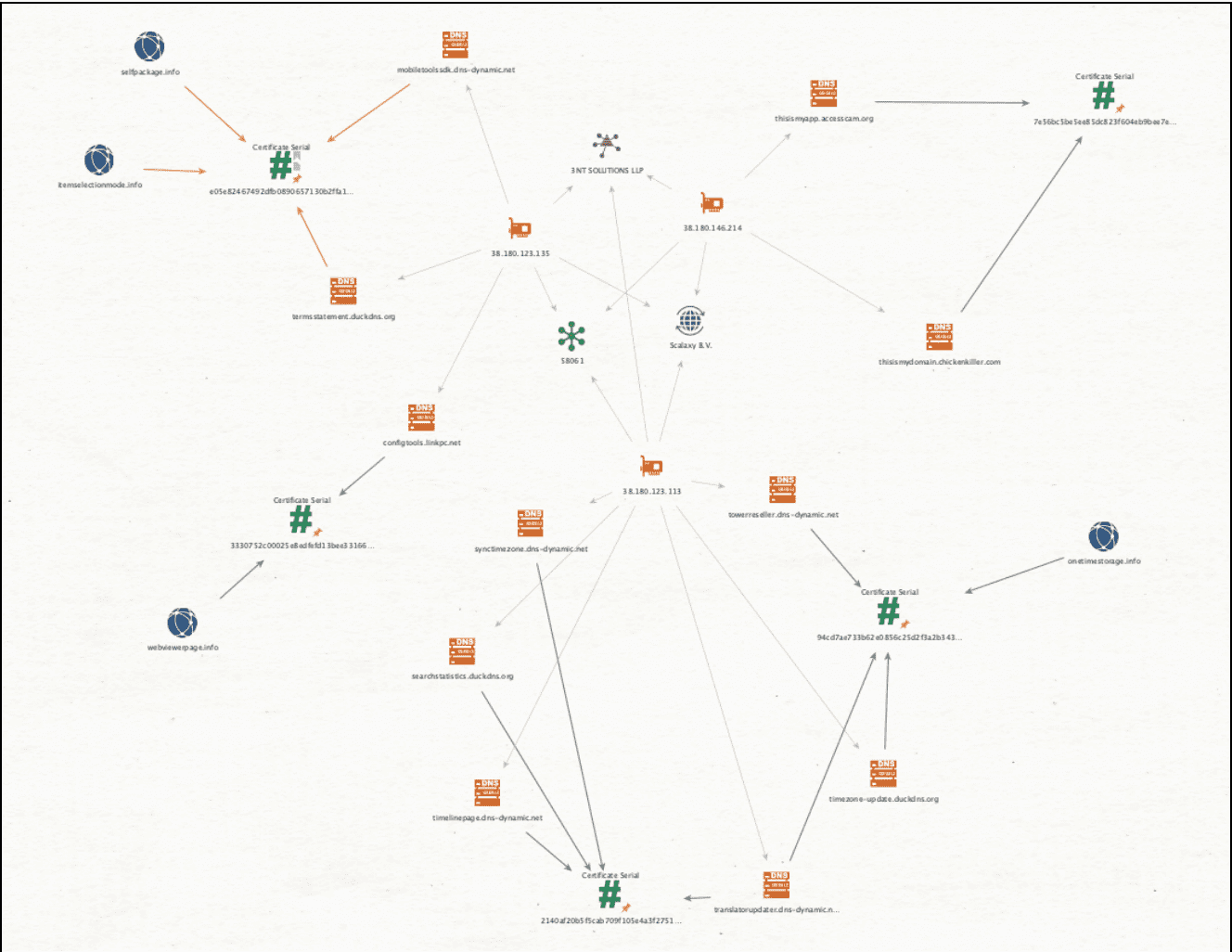
Link analysis between DDNS domains revealed a direct relationship via TLS certificates and reliance on the same infrastructure provider (Source: Recorded Future)
A recent report from Insikt Group has shed light on the covert operations of GreenCharlie, an Iran-backed Advanced Persistent Threat (APT) group, which has been linked to the targeting of US political campaigns. The group is suspected of operating under the directives of the Islamic Revolutionary Guard Corps’ Intelligence Organization (IRGC-IO) and shows significant overlap with other known Iranian threat actors such as Mint Sandstorm, Charming Kitten, and TA453.
According to Insikt Group, GreenCharlie has been meticulously building and expanding a network of malicious infrastructure since May 2024. This network has been leveraged in a series of cyber-espionage campaigns aimed at high-value targets, including government officials, diplomats, research analysts, and policy makers. The infrastructure includes a large number of domains registered through dynamic DNS (DDNS) services and various top-level domains (TLDs), primarily used to facilitate phishing operations and deliver malware.
The report highlights the use of several sophisticated malware families in GreenCharlie’s operations. Notably, Insikt Group identified the deployment of GORBLE, POWERSTAR, and NokNok malware, which are instrumental in the group’s spearphishing attacks. These malware families share significant code overlaps, suggesting they are variants of a single malware family designed to exfiltrate sensitive information from compromised systems.
GreenCharlie’s activities have a strong nexus to Iran, with evidence pointing to the use of Iranian IP addresses in communication with the group’s infrastructure. These findings bolster the theory that GreenCharlie operates at the behest of the IRGC-IO, reinforcing Iran’s strategic objectives of intelligence-gathering and interference in foreign political processes.
The report also delves into GreenCharlie’s use of ProtonVPN and ProtonMail to obscure their activities, a common tactic among Iranian APT groups. The group’s phishing operations are sophisticated, utilizing a range of domains designed to mimic legitimate services and lure victims into revealing sensitive information. One such domain, documentcloudeditor.ddnsgeek[.]com, was identified as hosting a phishing portal, although its exact purpose remains unclear.
Organizations involved in political campaigns, especially those in the US, are urged to remain vigilant and adopt proactive measures to mitigate the risk of falling victim to GreenCharlie’s sophisticated phishing and malware campaigns.
Related Posts:
- APT29 Strikes German Politics with WINELOADER Malware Assault
- Operation ShadowCat Targets Indian Political Observers
- The Doppelgänger Playbook: Russian Information Operations Unveiled (June-July 2024)
- Espionage Campaign Returns: LightSpy Targets Southern Asia
- New APT Group ‘Actor240524’ Targets Azerbaijan and Israel with Advanced Tactics