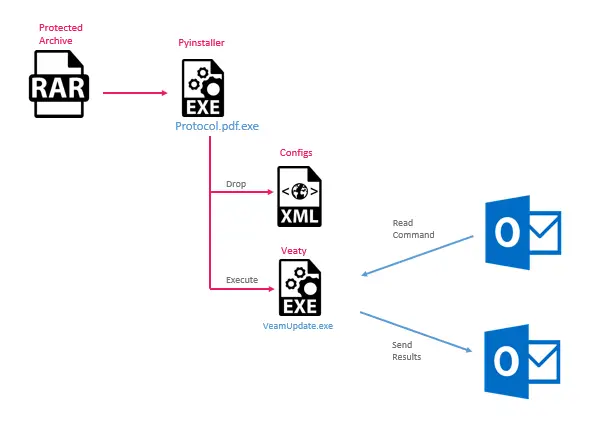
The infection chain installing Veaty malware | Image: Check Point
Check Point Research (CPR) has uncovered a sophisticated cyberespionage campaign aimed at the Iraqi government, bearing the hallmarks of Iranian state-sponsored threat actors. This campaign, which has been ongoing for several months, bears the hallmarks of the notorious APT34 group, an Iranian cyber espionage group known to be affiliated with Iran’s Ministry of Intelligence and Security (MOIS).
The campaign identified by CPR features a blend of custom-built tools designed specifically for the Iraqi government infrastructure. One of the most unique aspects of this operation is its use of custom C2 channels, including:
- DNS Tunneling Protocol: A stealthy way to communicate between infected machines and the C2 server using DNS queries.
- Email-Based C2 Channel: The attackers used compromised email accounts within the targeted organization to create a hidden communication pipeline.
These custom mechanisms allowed the threat actors to evade traditional detection methods and maintain long-term access to their targets.
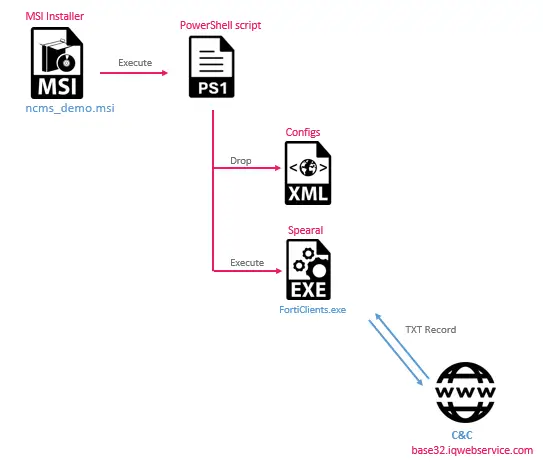
CPR’s analysis highlighted two primary malware families deployed in these attacks—Veaty and Spearal. Both of these backdoors were developed in .NET and employed highly sophisticated communication techniques to exfiltrate sensitive data from compromised systems.
- Veaty: This malware communicates through compromised email accounts in the Iraqi government’s infrastructure. It uses a carefully crafted mechanism that involves disabling SSL/TLS certificate verification to bypass security measures. Veaty uploads and downloads files, executes commands, and relies on encrypted messages hidden within email subjects or attachments to carry out its tasks.
- Spearal: Utilizing DNS tunneling, Spearal communicates with its C2 server by encoding data in DNS queries. This allows the attackers to remain under the radar, as DNS traffic is typically less scrutinized. The malware communicates through base32-encoded commands, allowing it to execute PowerShell commands, upload and download files, and send sensitive data back to the C2.
The initial infection vector in this campaign was likely a social engineering attack. The threat actors distributed files with misleading double extensions, such as Avamer.pdf.exe and Protocol.pdf.exe, to trick users into executing them. Once executed, these files deployed the Spearal or Veaty backdoors, granting the attackers access to the network.
CPR discovered that these malicious files were uploaded to VirusTotal from Iraq between March and May 2024. The tactics, techniques, and procedures (TTPs) observed in this campaign strongly suggest links to APT34, an Iranian state-sponsored group known for its cyberespionage activities in the Middle East. The use of similar tools, infrastructure, and targeting patterns points to a coordinated effort to infiltrate and exfiltrate sensitive information from Iraqi government entities.
One of the more sophisticated elements of this campaign was the use of a custom IIS backdoor named CacheHttp.dll. This backdoor listens for incoming HTTP requests on compromised IIS servers and executes commands based on data embedded within HTTP headers. The communication is encrypted using AES-CBC, making detection challenging for traditional monitoring tools. This method evolved from older backdoors like RGDoor.
With the continuing rise of cyber espionage in the Middle East, government institutions and private organizations must remain vigilant, recognizing that today’s cyberattacks are more targeted, stealthy, and sophisticated than ever before.