IRMA v2.4.15 releases: Incident Response & Malware Analysis
IRMA: Incident Response & Malware Analysis
IRMA is an asynchronous and customizable analysis system for suspicious files. This repository is a subproject of IRMA and contains the source code for IRMA’s Frontend, which is a Python-based application that provides a way to store analysis performed by probes in a database and to display them either through a web-client or a CLI-client.
IRMA intends to be an open-source platform designed to help to identify and analyzing malicious files.
However, today’s defense is not only about learning about a file, but it is also getting a fine overview of the incident you dealt with: where / when a malicious file has been seen, who submitted a hash, where a hash has been noticed, which anti-virus detects it, …
An important value with IRMA comes from you keep control over where goes and who gets your data. Once you install IRMA on your network, your data stays on your network.
Each submitted files is analyzed in various ways. For now, we focus our efforts on multiple anti-virus engines, but we are working on other “probes” (feel free to submit your own).
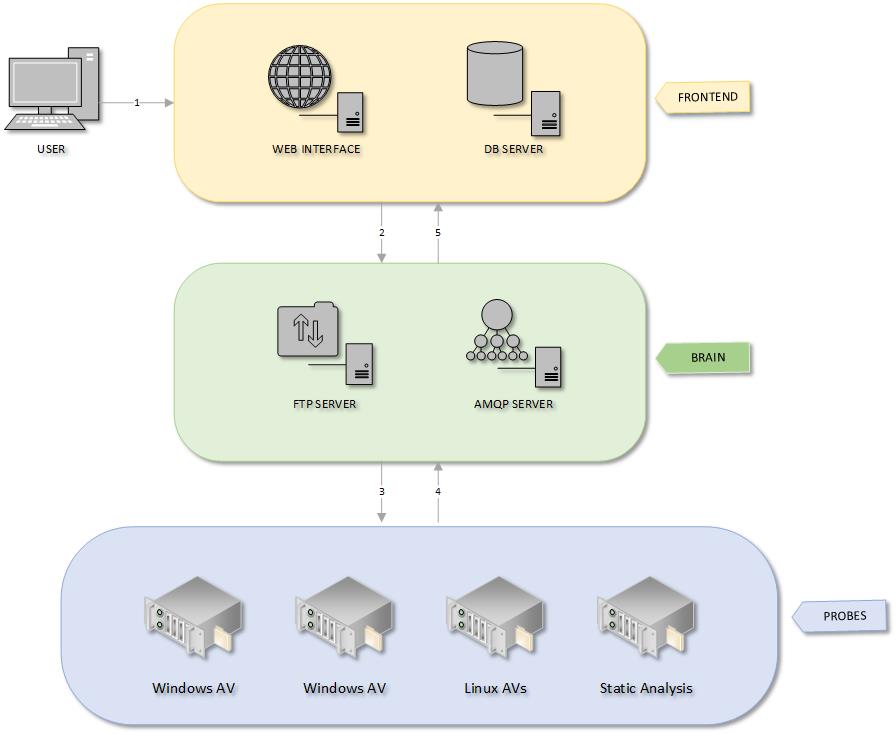
File Analysis Process
- An analysis begins when a user uploads files to the Frontend.
- Frontend checks for existing files and results in SQL. If needed, it stores the new files and calls asynchronously scan jobs on Brain.
- Brain worker sends as many subtasks to Probe(s) as needed.
- Probe workers process their jobs and send back results to Brain.
- Brain sends results to Frontend.
Changelog v2.4.15
- * [fix] update get-pip for python2
- * [fix] add missing acl package on AWS default debian stretch image
Install
$ git clone https://github.com/quarkslab/irma $ cd irma $ vagrant up
Tutorial
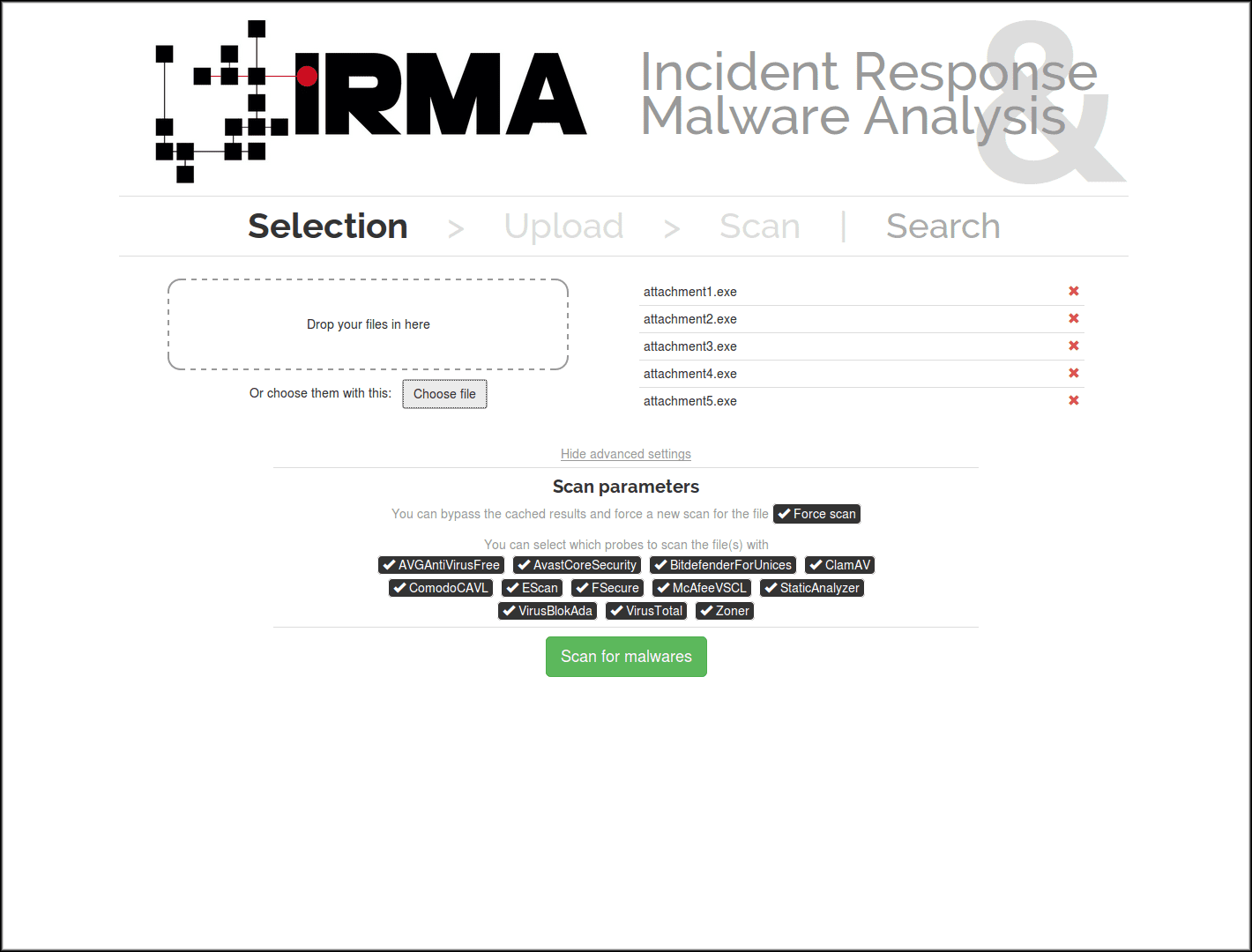
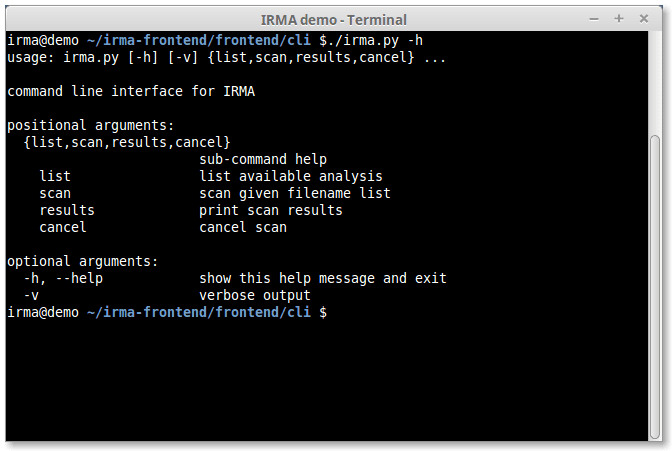
Command Line Interface
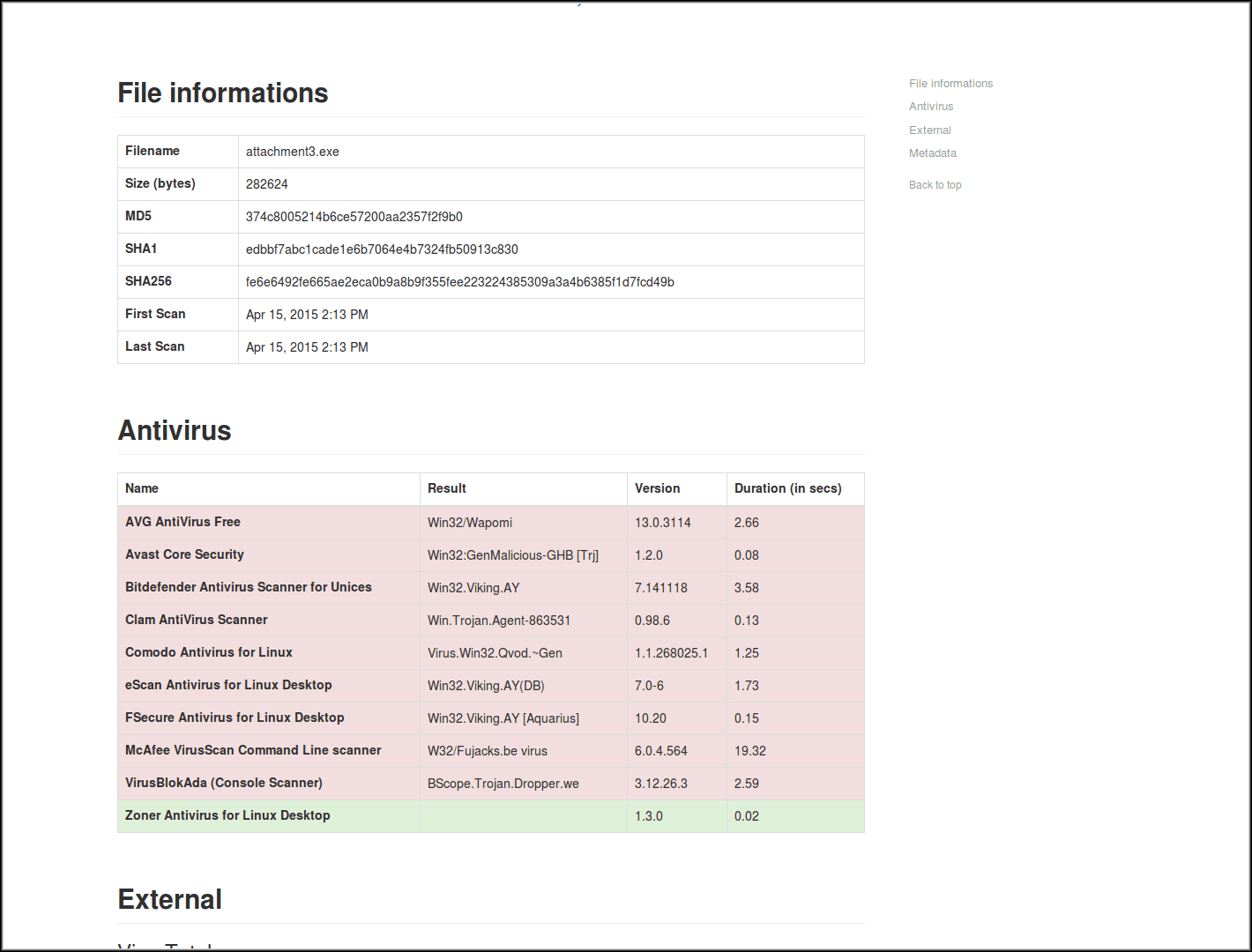
Web Interface

Copyright 2013-2018, Quarkslab
Source: https://github.com/quarkslab/