Anomalies were detected by Kaspersky through vigilant monitoring of internal network traffic, leading to the uncovering of what is now known as ‘Operation Triangulation’.
Kaspersky Lab remains steadfast in its pursuit to unravel the mysteries of Operation Triangulation. Through meticulous research, Kaspersky’s team has discovered a method for swiftly detecting the presence of spyware on iPhones.
Historically, detecting malicious software necessitated a complete backup of the iPhone, followed by a thorough examination of the backup data for anomalies. However, Kaspersky has now devised a more streamlined approach named ‘iShutdown’. Kaspersky has released an open-source script, iShutdown, designed for rapid detection of spyware infections in iOS devices.

The log file, named shutdown.log, became a focal point in Kaspersky’s study of Israeli spyware developers, including the NSO Group’s Pegasus, QuaDream’s Reign, and Intellexa’s Predator. A commonality among these spyware programs was unearthed.
These spyware invariably leave traces in the device’s reboot logs, primarily because each spyware strives for persistence and hence must remain active in the background for extended periods.
Consequently, during an iPhone reboot, processes related to this spyware hinder the system’s reboot procedure, slightly prolonging the restart time. The system, in turn, records these events in the logs.
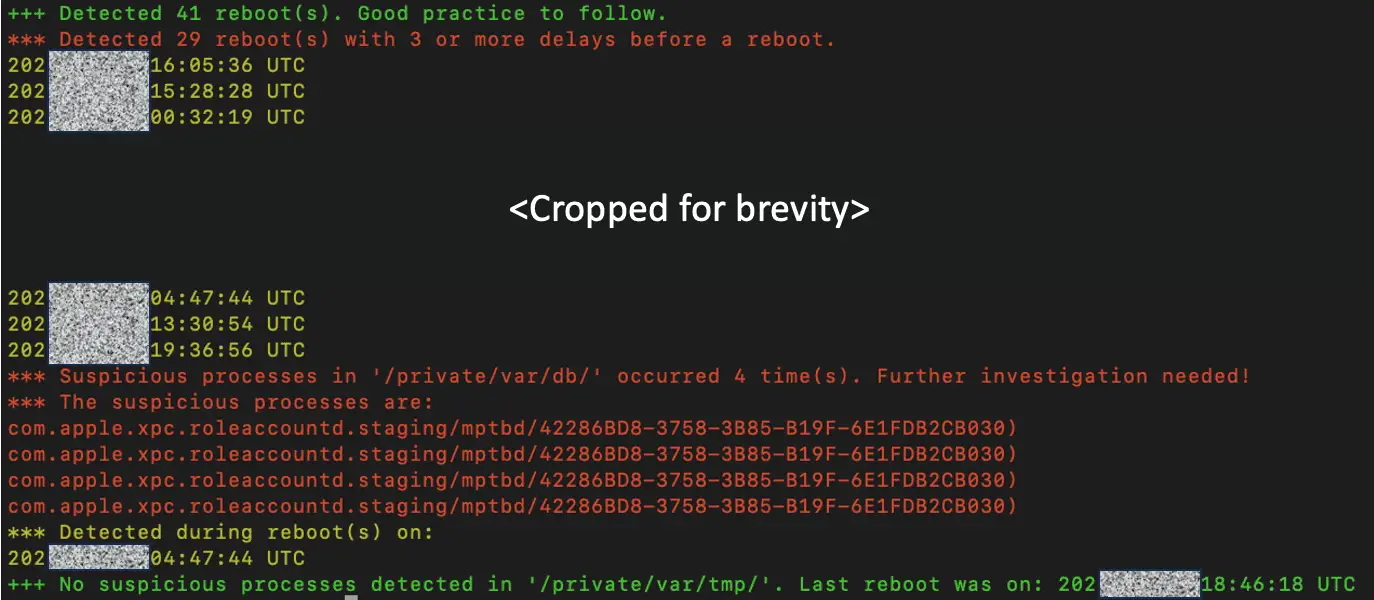
Investigations have revealed that all three Israeli commercial spyware developers utilize similar filesystem paths: /private/var/db/ and /private/var/tmp/.
Kaspersky notes that users who frequently restart their iPhones are more likely to observe related entries in the logs. Thus, extracting the shutdown.log file is sufficient for analyzing whether an iPhone has been compromised by spyware.
It’s important to note that shutdown.log is not autonomously generated by the system. iOS primarily uses sysdiag for log recording, so the shutdown.log must be manually created and exported. The exported file, typically ranging between 200 to 400 MB in size and in the .tar.gz format, contains the necessary logs in \system_logs.logarchive\Extra\.
To this end, Kaspersky has developed a Python script capable of automatically scouring through the exported logs for anomalies. If such irregular entries are found, they warrant a thorough examination by researchers to ascertain the presence of spyware.
In conclusion, the specific perpetrators behind Kaspersky’s Triangulation Attack remain elusive. The spyware used in the attack is a novel creation, not the handiwork of the aforementioned Israeli commercial spyware developers.