Ivanti EPMM CVE-2024-22026 Vulnerability: Potential for Full System Takeover, PoC Published
Ivanti’s Enterprise Mobility Management Platform (EPMM), a widely used mobile device management solution, has been found to contain a high-severity vulnerability (CVE-2024-22026) that could allow attackers to gain full control of affected systems.
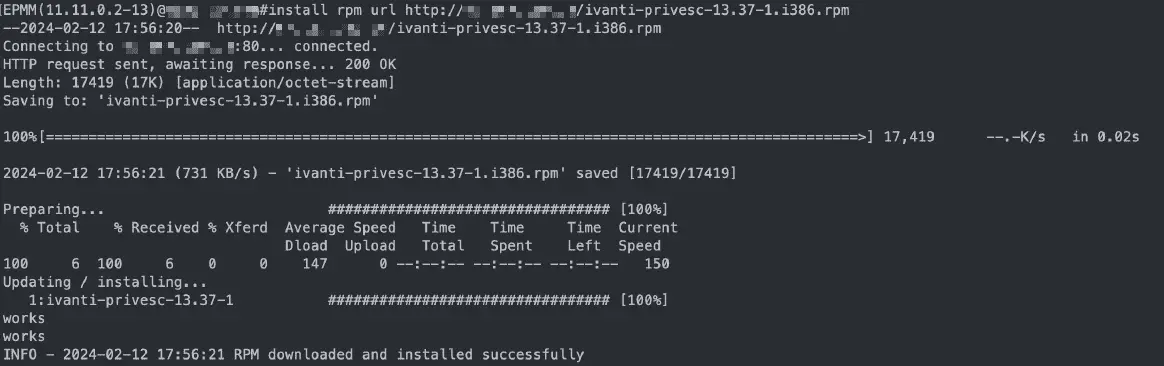
Identified by Bryan Smith of Redline Cyber Security, CVE-2024-22026 is a high-severity vulnerability that allows for local privilege escalation within the EPMM. This flaw, found in versions prior to 12.1.0.0, 12.0.0.0, and 11.12.0.1, enables an attacker to gain root privileges via the [install rpm url] command in the clish restricted shell.
The vulnerability resides in the EPMM command-line interface (CLI) tool installation command. It allows attackers to execute arbitrary code with root privileges by tricking the system into installing a malicious RPM package from a user-provided URL. The lack of authentication checks and signature verification mechanisms in the installation process exacerbates the risk.

The vulnerability stems from inadequate validation within the EPMM CLI’s tool installation command. The console allows the installation of tools or RPMs through the [install] command, specifically using [install rpm url] to fetch an RPM package from a user-provided URL without verifying its authenticity. This lack of validation enables attackers to execute arbitrary commands with root privileges by delivering a malicious RPM package.
Behind the scenes, the appliance uses the command [wget -t 3 -c <URL>], followed by /bin/rpm -Uvh *.rpm, to perform the installation. The appliance does not enforce signature verification or URL filtering, making it vulnerable to exploitation. Furthermore, the versions of curl and wget in use on this fully patched appliance were released in 2013 and contain numerous known vulnerabilities, exacerbating the risk.
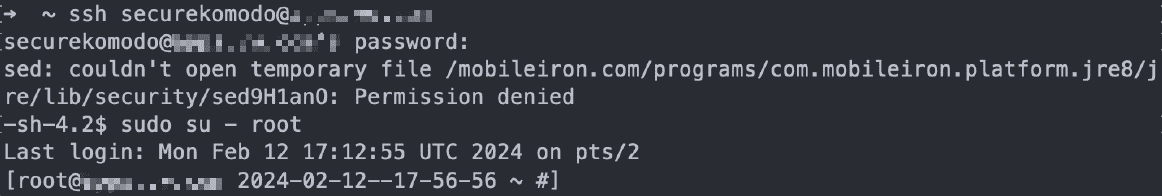
Bryan Smith shared the technical details and a proof-of-concept (PoC) for CVE-2024-22026.
The potential impact of successfully exploiting this flaw is severe and includes:
- Complete system compromise
- Unauthorized access to sensitive data
- Potential for further network intrusion
Ivanti has released patches for versions 12.1.0.0, 12.0.0.0, and 11.12.0.1 of EPMM to address this vulnerability. It is crucial for organizations using EPMM to apply these updates immediately to protect their systems and data.