Main.java in STR RAT
A recent analysis by security researcher Jacob Malimban at Cofense has revealed a resurgence in activity from the STR RAT malware, a Java-based Remote Access Trojan (RAT) known for its credential theft and surveillance capabilities. Originally identified in a forum post in 2020, STR RAT has since evolved, incorporating new features and techniques to evade detection and increase its potency. The malware is capable of keylogging, stealing credentials, and delivering additional malicious payloads.

STR RAT made its debut in 2020 with version 1.2, featuring standard RAT functionalities such as password stealing, keystroke logging, and backdoor access. It also included a fake ransomware module that renamed files without encrypting them. In 2021, Microsoft Threat Intelligence highlighted its use in phishing campaigns. By 2022, the malware had begun spoofing the Maersk shipping brand and employing polyglot file techniques to enhance compatibility with Windows systems.
In 2023, STR RAT reached version 1.6, utilizing obfuscation tools like Zelix KlassMaster and Allatori to make analysis more challenging for cybersecurity professionals. The latest update in 2024 saw STR RAT being uploaded to legitimate services like GitHub and AWS, which helped it bypass security measures by appearing more credible.
Cofense’s analysis from January 2023 to April 2024 reveals that 60% of STR RAT samples were delivered directly via email attachments, rather than embedded links. The remaining samples were distributed through loaders, embedded URLs, and droppers.
- Attachments: STR RAT is typically delivered as a .jar file within an email attachment. These archives may include the necessary Java Runtime Environment (JRE) binaries to run the malware, or they may download these components from Maven and GitHub repositories.
- Loaders: These are malware that reach out to payload locations to download and execute STR RAT. Common loaders include Jar Downloaders, which can update the payload while keeping the original downloader link intact, and exploit CVE-2017-11882, a Microsoft Office vulnerability.
- Embedded URLs: Attackers may use links within emails or PDFs to download the malware. These URLs often host the malware on legitimate services like AWS, GitHub, and Discord’s CDN, making them appear trustworthy to both email security systems and recipients.
- Droppers: These files contain both the malicious code and the final malware. A JS Dropper, for example, is a .js file that executes natively on Windows, delivering STR RAT directly without needing to download additional payloads.
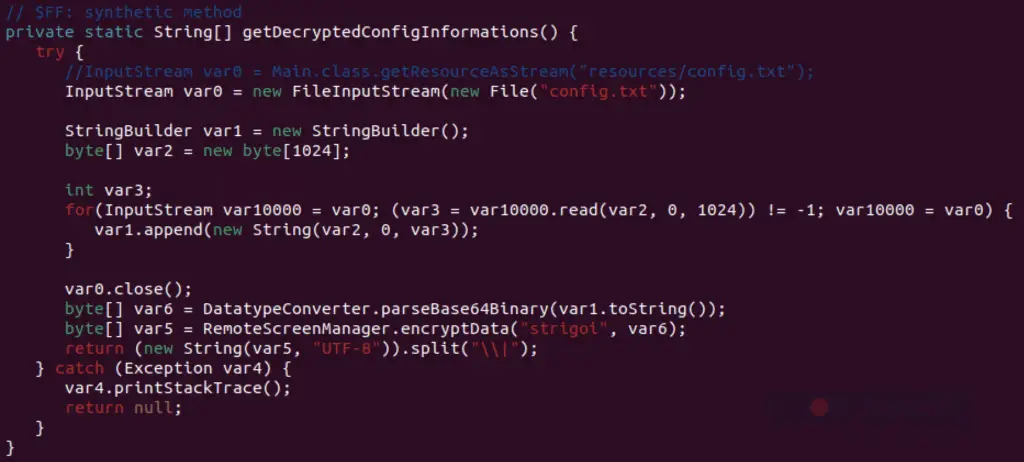
Once executed, STR RAT installs dependencies, creates persistence mechanisms, and communicates with its command and control (C2) servers. It uses a lock file to prevent multiple instances and encrypts its configuration using AES, with the passphrase “strigoi” found in the Main.java file. The malware also uses Java libraries for keylogging and SQLite databases.
Key indicators of STR RAT infection include renamed files in the AppData Roaming and user’s local home profile directories, new folders containing legitimate files used by the malware, and the presence of a lock file indicating the port used for C2 communication. STR RAT also creates persistence through registry keys or scheduled tasks, ensuring it runs every time the user logs in.
STR RAT often communicates with C2 servers via subdomains of free dynamic DNS services or legitimate platforms like GitHub and Maven. This dual-use of legitimate and malicious services makes detection challenging, requiring vigilant monitoring of network traffic and endpoint behavior.
The resurgence of STR RAT demonstrates the ongoing cat-and-mouse game between threat actors and cybersecurity professionals. While the malware itself may not be new, its evolving tactics highlight the importance of continuous adaptation and vigilance in the face of ever-changing cyber threats.