The Attack Chain Analysis of JS to C2 | Source: CYFIRMA
Cybersecurity firm CYFIRMA has uncovered a highly sophisticated malware campaign leveraging JavaScript to establish covert communication with a Command-and-Control (C2) server. This newly discovered attack chain employs advanced obfuscation techniques, steganography, and abuse of legitimate services to evade detection while exfiltrating sensitive user data.
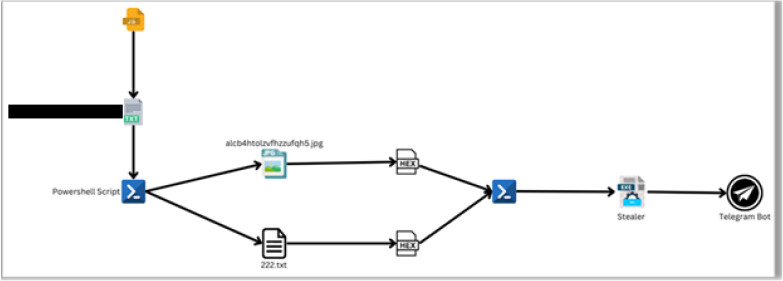
According to CYFIRMA’s analysis, the attack initiates with an obfuscated JavaScript file, which retrieves encoded strings from an open-source service. These strings trigger a PowerShell script, responsible for downloading additional payloads, including a JPG image and a text file. However, these files contain malicious MZ DOS executables cleverly hidden using steganographic techniques.
Once executed, the attack culminates in the deployment of Stealer malware, which harvests credentials, browser data, and system information before transmitting the stolen data to an attacker-controlled Telegram bot. This multi-layered obfuscation and use of legitimate cloud-based media hosting services help the malware remain undetected by traditional security mechanisms.
“The attack leverages multiple layers of obfuscation, legitimate web services for payload hosting, and encrypted communication to make detection and mitigation challenging,” CYFIRMA reported.
The malware’s dropper script is highly obfuscated, employing Unicode character manipulation, runtime code evaluation (eval()), and ActiveX abuse. This prevents both static and dynamic analysis, making detection difficult.
Cybercriminals leverage legitimate cloud services for C2 communication and payload hosting. An open-source media platform is used to store a seemingly harmless JPG image, which actually contains an embedded malicious .NET assembly. This enables the malware to blend into normal network traffic, bypassing traditional security scans.
To further evade detection, the attackers employ steganography to hide Base64-encoded .NET assemblies within images. These images, when processed by the malware, extract and execute the hidden code, making it impossible for traditional content inspection tools to flag them as malicious.
Once the malicious payload is extracted, the .NET assembly is executed directly from memory, a technique known as reflective loading. This method avoids leaving traces on disk, reducing forensic evidence and preventing detection by file-based antivirus solutions.
The campaign exploits legacy technologies such as ActiveX objects (WScript.Shell, Scripting.FileSystemObject) and PowerShell scripts to interact with the system. This enables the execution of arbitrary commands and facilitates dynamic payload extraction and in-memory execution.
Unlike traditional malware that communicates via compromised web servers, this campaign transmits stolen data using a Telegram bot-controlled C2 server. This provides cybercriminals with an encrypted and persistent method of retrieving victim data while bypassing many conventional network security measures.
“The integration of a .NET payload within this framework allows attackers to potentially deploy a variety of subsequent threats, including ransomware, information stealers, and backdoors,” CYFIRMA warns.