Jeopardize
Jeopardize tool is developed to provide basic threat intelligence&response capabilities against phishing domains at the minimum cost possible. It detects registered phishing domain candidates (typosquatting, homograph, etc.), analyzes them, and assigns a risk score to them. After then, it sends valid-looking credentials to the login forms on those phishing sites.
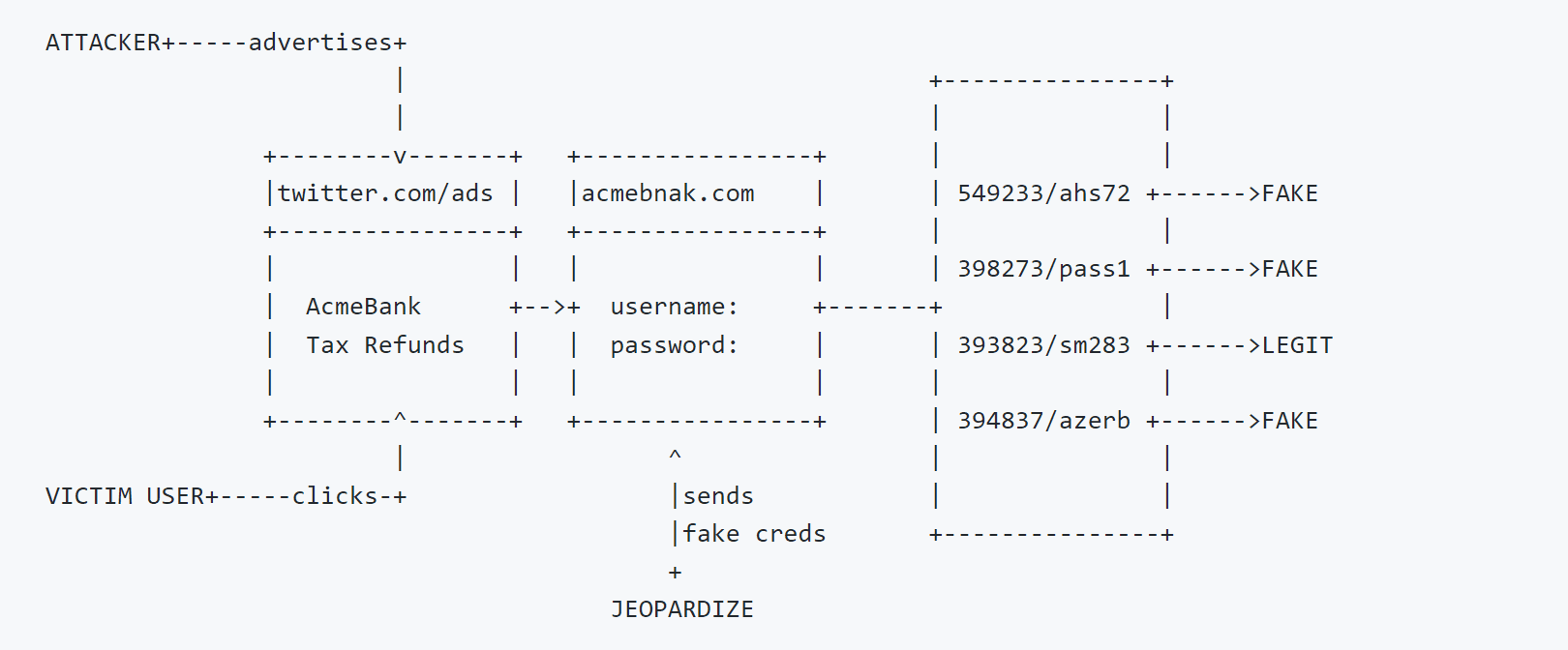
Why? Imagine this scenario: Attacker registers a phishing domain, acmebnak.com (Typosquatting of acmebank), copies the original acmebank.com’s login form there, and advertises this domain via sponsored tweets. This ad and the domain probably will be marked as phishing in the next day but the attacker has already harvested credentials from users. Taking it down after this won’t help the affected users. Jeopardize provides a proactive solution to this problem. It jeopardizes the phishing form with valid-looking credentials to confuse the attacker. This will buy organizations some time to take precautions.
How does it work?
1- Generating the combinations
Jeopardize generates different word combinations with a given domain. (dnstwist helps here) For example, if the given domain is acmebank.com, combinations would be acmebnak, acmeban, amcebank, etc. If your domain has a short or generic name (for example aa.com) This tool won’t help you. It works best for unique names.
2- Detecting Registered Domains
Jeopardize has two different detection methods to identify registered domains:
Brute: Jeopardize combines the generated words (acmebnak, amcebank, etc.) with all TLDs (com, net,xyz, live, etc.) and does whois query for all of them. Pros: Doesn’t require any API key, totally free. / Cons: Takes lots of time.
Dailly With the given Zonefiles.io API Key, Jeopardize scrapes all domains registered in the last 24 Hours and searches them for the generated words (acmebnak, amcebank, etc.). Pros: Fast, can be used as a daily threat intelligence easily. Cons: Requires Zonefiles.io API Key (Pro edition)
3- Analyzing the Domains
Detected domains are already suspicious. But there are factors that increase the likelihood of being a phishing domain. Also, we need to analyze if any phishing page is installed on that domain so that we can take action against them. Jeopardize checks the following elements of the registered domains:
- IP: If any IP address is assigned to the domain. If yes, the phishing risk score will increase.
- Web Server: If a web server is installed on that domain. If yes, the phishing risk score will increase.
- Nameservers: Checking the nameservers. If it uses Cloudflare, the phishing risk score will increase (no offense)
- Website Size: Checking the size of the website. Phishing pages usually contain different images, css, and js files. The phishing risk score will increase if it’s above a predefined threshold.
- Login Form: If a login form is identified at the website. If yes, the phishing risk score will increase.
- SSL Certificate: Checking the CA of the SSL certificate. If it’s issued by a CA other than Cloudflare or LetsEncrypt, the phishing risk score will “decrease”.
- Registration Date: Checking the registration date of the domain. If it’s newer than one month, the phishing risk score will increase.
- Alexa Ranking: Checking the Alexa ranking of the domain. If it’s not listed in there, the phishing risk score will increase.
4- Jeopardizing Login Forms
If the phishing score is high and the website has a login form, Jeopardize will fill it automatically with the provided username/password list.
Saving the Results
It saves the information of detected phishing domains to an XML file. For example:
Install & Use
Copyright (c) 2020, Utku Sen
All rights reserved.