JexBoss: Jboss, Java Deserialization Vulnerabilities verify & EXploitation Tool
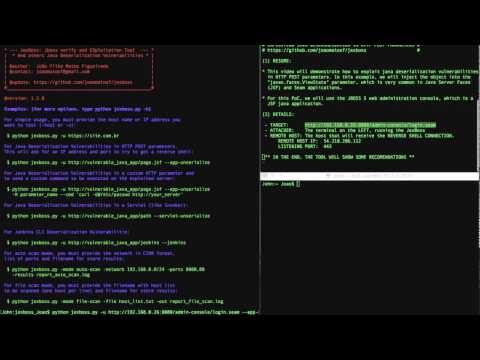
JexBoss is a tool for testing and exploiting vulnerabilities in JBoss Application Server and others Java Platforms, Frameworks, Applications, etc.
Features
The tool and exploits were developed and tested for:
- JBoss Application Server versions: 3, 4, 5 and 6.
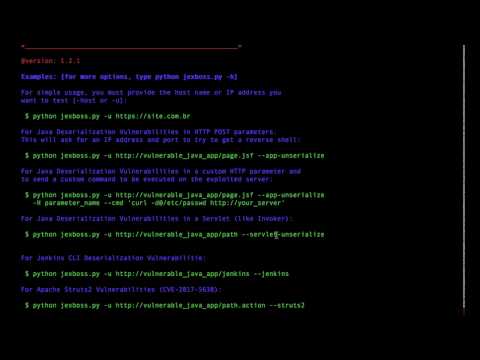
- Java Deserialization Vulnerabilities in multiple java frameworks, platforms and applications (e.g., Java Server Faces – JSF, Seam Framework, RMI over HTTP, Jenkins CLI RCE (CVE-2015-5317), Remote JMX (CVE-2016-3427, CVE-2016-8735), etc)
The exploitation vectors are:
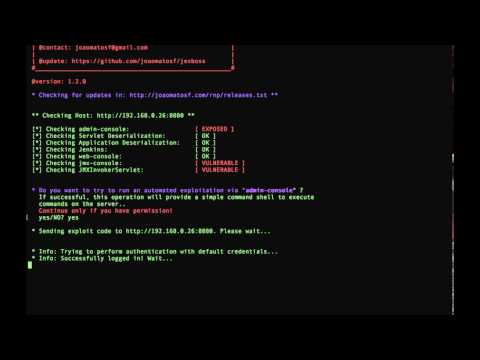
- /admin-console
- tested and working in JBoss versions 5 and 6
- /jmx-console
- tested and working in JBoss versions 4, 5 and 6
- /web-console/Invoker
- tested and working in JBoss versions 4, 5 and 6
- /invoker/JMXInvokerServlet
- tested and working in JBoss versions 4, 5 and 6
- Application Deserialization
- tested and working against multiple java applications, platforms, etc, via HTTP POST Parameters
- Servlet Deserialization
- tested and working against multiple java applications, platforms, etc, via servlets that process serialized objets (e.g. when you see an “Invoker” in a link)
- Apache Struts2 CVE-2017-5638
- tested in Apache Struts 2 applications
- Others
Installation on Linux\Mac
Installation on Windows
If you are using Windows, you can use the Git Bash to run the JexBoss. Follow the steps below:
- Download and install Python
- Download and install Git for Windows
- After installing, run the Git for Windows and type the following commands:
Demo
- Exploiting Java Deserialization Vulnerabilities (RCE) on JSF/Seam Applications via javax.faces.ViewState with JexBoss
- Exploiting JBoss Application Server with JexBoss
- Exploiting Apache Struts2 (RCE) with Jexboss (CVE-2017-5638)
Source:Github