JoomlaVS
A black box, Ruby powered, Joomla vulnerability scanner, Ruby application that can help automate assessing how vulnerable a Joomla installation is to exploitation. It supports basic fingerprinting and can scan for vulnerabilities in components, modules, and templates as well as vulnerabilities that exist within Joomla itself.
Installation
sudo apt-get install build-essential patch
sudo apt-get install ruby-dev zlib1g-dev liblzma-dev libcurl4-openssl-dev
Ensure Ruby [2.2.6 or above] is installed on your system
Clone the source code using git clone https://github.com/rastating/joomlavs.git
Install bundler and required gems using sudo gem install bundler && bundle install
Usage
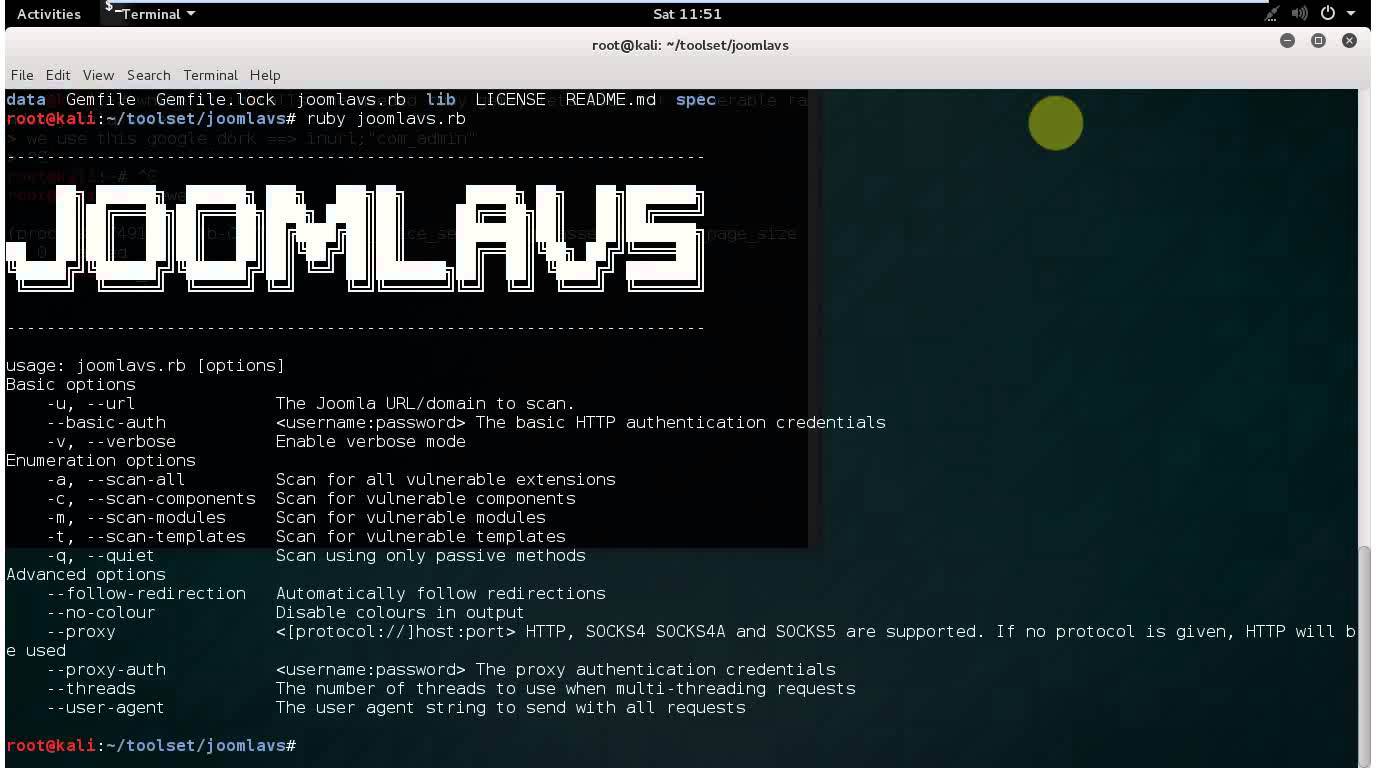
usage: joomlavs.rb [options]
Basic options
-u, --url The Joomla URL/domain to scan.
--basic-auth <username:password> The basic HTTP authentication credentials
-v, --verbose Enable verbose mode
Enumeration options
-a, --scan-all Scan for all vulnerable extensions
-c, --scan-components Scan for vulnerable components
-m, --scan-modules Scan for vulnerable modules
-t, --scan-templates Scan for vulnerable templates
-q, --quiet Scan using only passive methods
Advanced options
--follow-redirection Automatically follow redirections
--no-colour Disable colours in output
--proxy <[protocol://]host:port> HTTP, SOCKS4 SOCKS4A and SOCKS5 are supported. If no protocol is given, HTTP will be used
--proxy-auth <username:password> The proxy authentication credentials
--threads The number of threads to use when multi-threading requests
--user-agent The user agent string to send with all requests
Copyright (C) 2015 rastating
Source: https://github.com/rastating/