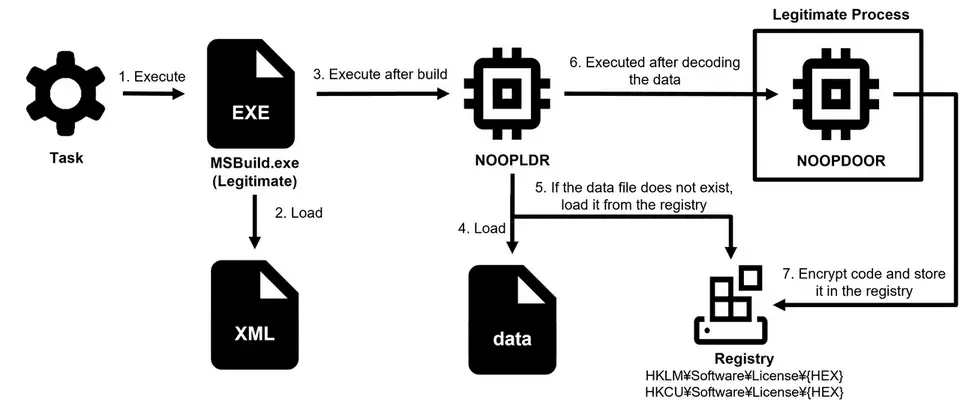
NOOPDOOR launched by an XML file (Type1)
JPCERT Coordination Center (JPCERT/CC) has released a comprehensive report detailing ongoing cyberattacks by the notorious MirrorFace LODEINFO and NOOPDOOR malware against Japanese organizations.
MirrorFace, a persistent threat actor observed since 2022, initially targeted media outlets, political organizations, think tanks, and universities. However, since 2023, their focus has shifted towards manufacturers and research institutions. This change in targets indicates a strategic move to infiltrate organizations with valuable intellectual property and sensitive data. MirrorFace has adapted its methods over time. Initially relying on spear-phishing emails to gain entry into networks, they now exploit vulnerabilities in external assets.
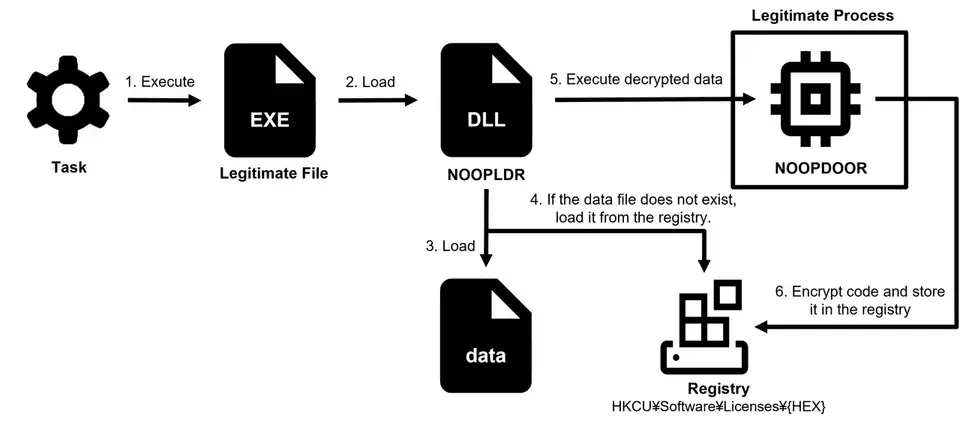
At the core of these attacks is the NOOPDOOR malware, a sophisticated tool capable of stealthy infiltration and persistence. NOOPDOOR operates by injecting shellcode into legitimate applications via two methods: an XML file (Type 1) or a DLL file (Type 2). This dual-method approach complicates detection and eradication efforts.

- Type 1: Utilizes obfuscated C# code in an XML file, compiled and executed using MSBuild. It decrypts data loaded in AES (CBC mode) and injects the code into a legitimate application.
- Type 2: Employs DLL side-loading to load NOOPLDR into a legitimate application, decrypting and injecting the malicious code similarly to Type 1.
MirrorFace employs several evasion techniques to ensure long-term persistence:
- Obfuscation: NOOPLDR uses Control Flow Flattening (CFF) to hinder analysis.
- Registry Storage: Stores encrypted code in the registry, reducing detectable artifacts.
- Service Hiding: Some Type 2 samples hide registered services using specific commands.
- Time Stamp Alteration: Changes file creation dates to confuse forensic analysis.
- Firewall Manipulation: Adds rules to allow communication through specific ports used by NOOPDOOR.
- Event Log Deletion: Deletes Windows Event logs to cover tracks.
- Windows Defender Disabling: Recorded in Event logs with specific Event IDs.
Once inside the network, MirrorFace conducts reconnaissance using a range of Windows commands and attempts to access credentials from Lsass memory dumps, NTDS.dit files, and registry hives. These activities are detectable by robust endpoint detection and response (EDR) solutions.
The attackers utilize tools like WinRAR and SFTP for data exfiltration, carefully reviewing file contents before exfiltration. They also leverage tools such as GO Simple Tunnel (GOST) and TinyShell-based malware on Linux servers to maintain communication and exfiltration channels.
JPCERT/CC urges all organizations, especially those in Japan, to remain vigilant, implement the latest security patches, and enhance their detection capabilities to combat these sophisticated threats. For detailed indicators of compromise (IoCs) and further technical insights, refer to the full report by JPCERT/CC.