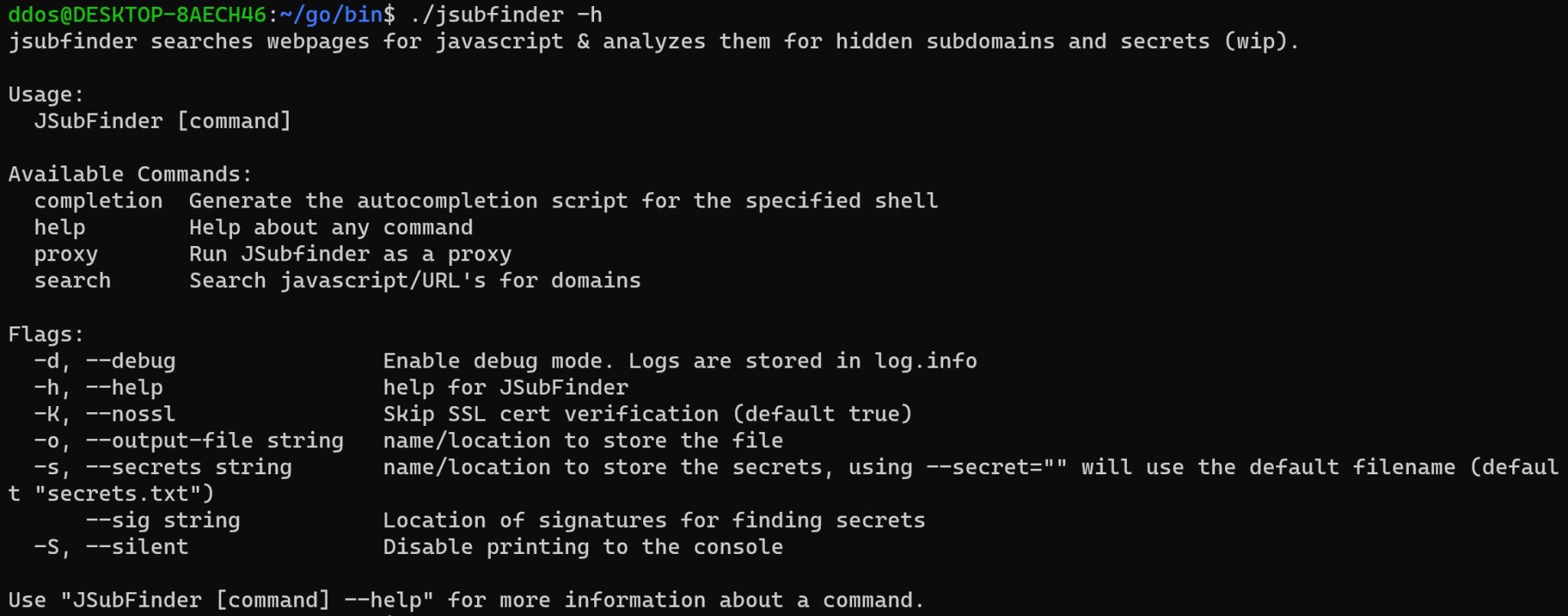
JSubFinder
JSubFinder is a tool written in golang to search webpages & javascript for hidden subdomains and secrets in the given URL. Developed with BugBounty hunters in mind JSubFinder takes advantage of Go’s amazing performance allowing it to utilize large data sets & be easily chained with other tools.
Install
go get github.com/ThreatUnkown/jsubfinder
wget https://raw.githubusercontent.com/ThreatUnkown/jsubfinder/master/.jsf_signatures.yaml && mv .jsf_signatures.yaml ~/.jsf_signatures.yaml
Use

Examples (results are the same in this case):
With Secrets Enabled
note –secrets=”” will save the secret results in a secrets.txt file
Advanced examples
$ echo www.google.com | jsubfinder search -crawl -s “google_secrets.txt” -S -o jsf_google.txt -t 10 -g
-crawluse the default crawler to crawl pages for other URL’s to analyze-senables JSubFinder to search for secrets-SSilence output to console-o <file>save output to specified file-t 10use 10 threads-gsearch every URL for JS, even ones we don’t think have any
Proxy
Enables the upstream HTTP proxy with TLS MITM support. This allows you to:
- Browse sites in real-time and have JSubFinder search for subdomains and secrets in real-time.
- If needed run jsubfinder on another server to offload the workload
With Burp Suite
- Configure Burp Suite to forward traffic to an upstream proxy/ (User Options > Connections > Upsteam Proxy Servers > Add)
- Run JSubFinder in proxy mode
Burp Suite will now forward all traffic proxied through it to JSubFinder. JSubFinder will retrieve the response, return it to burp, and in another thread search for subdomains and secrets.
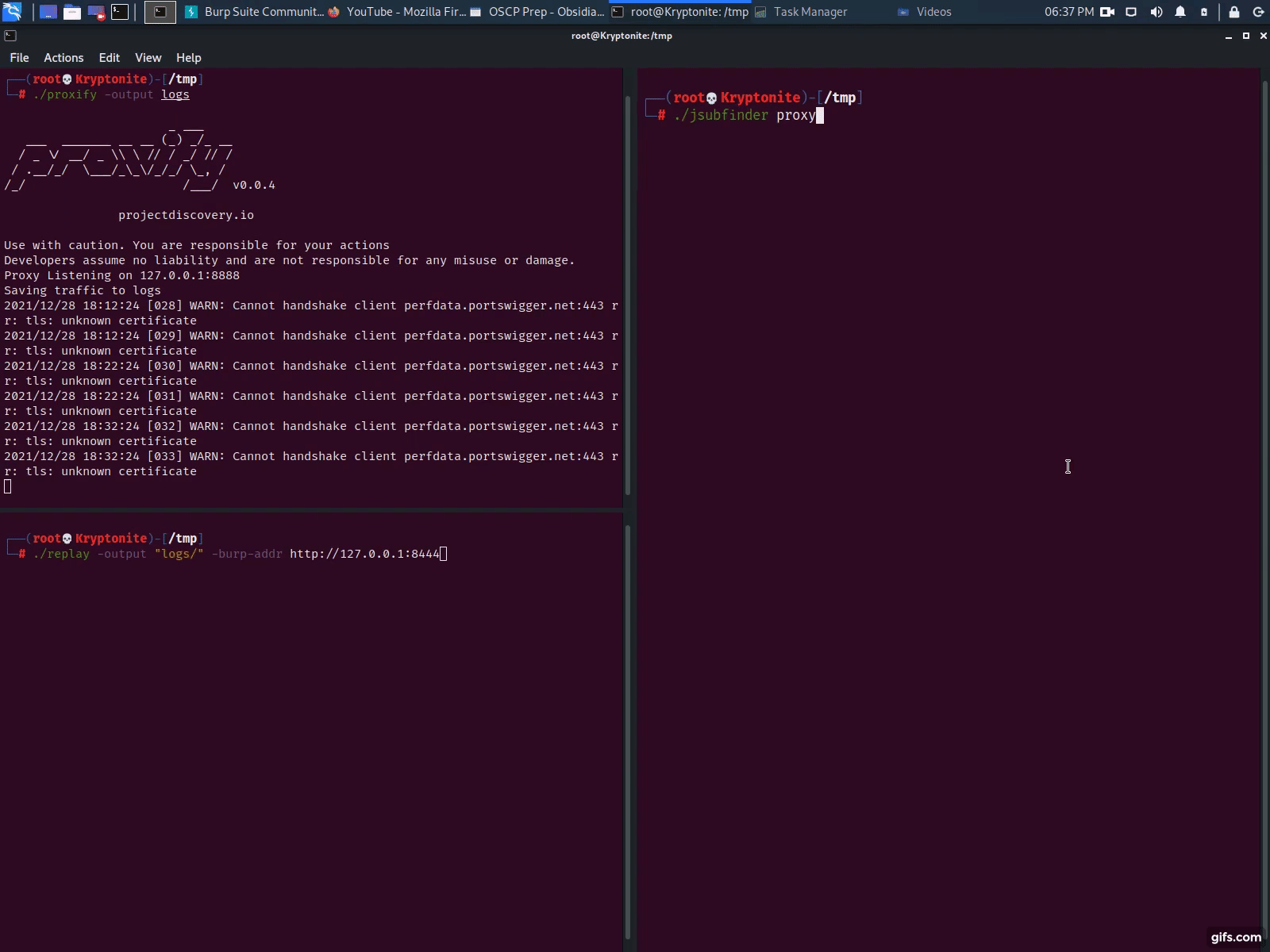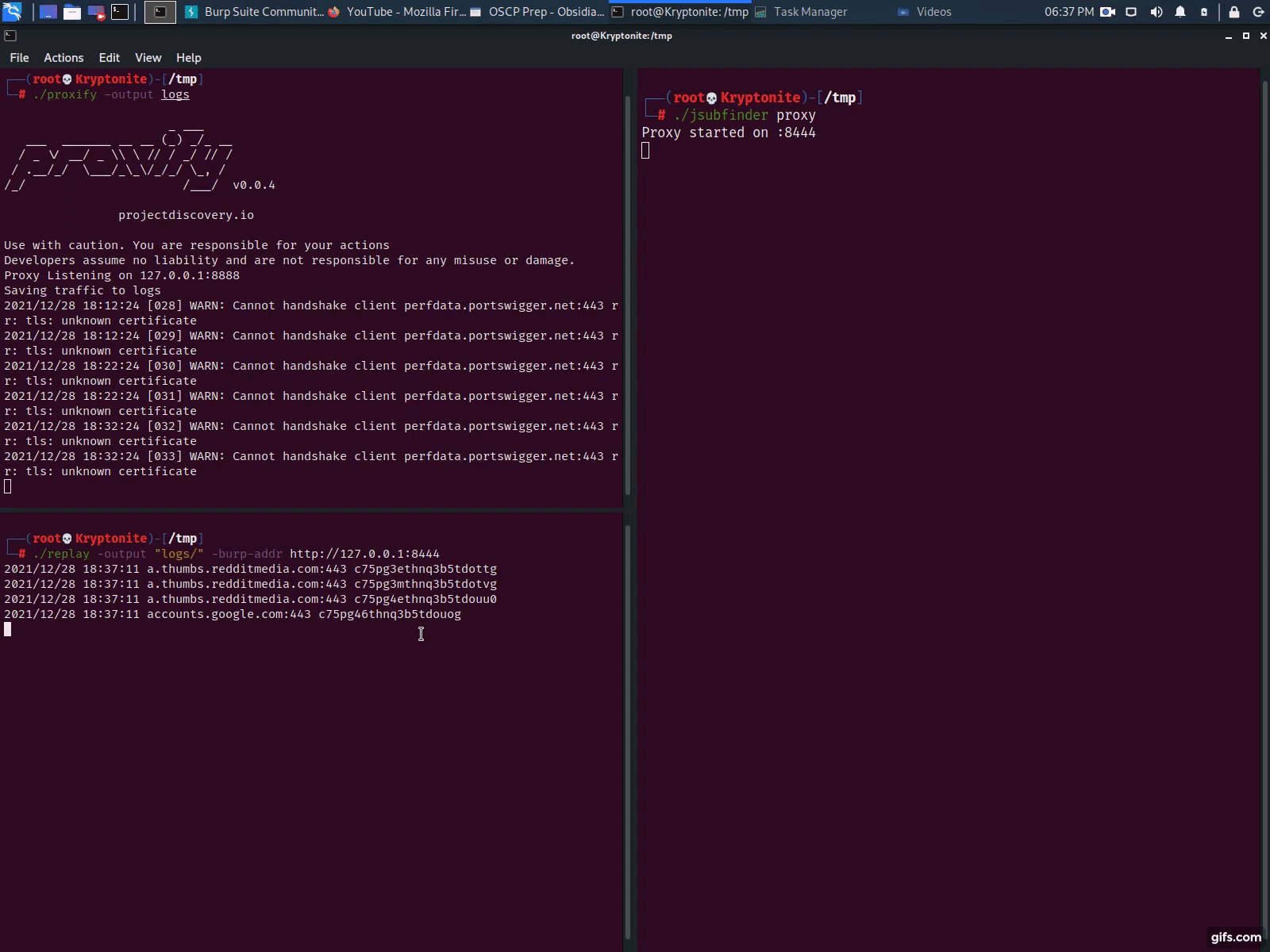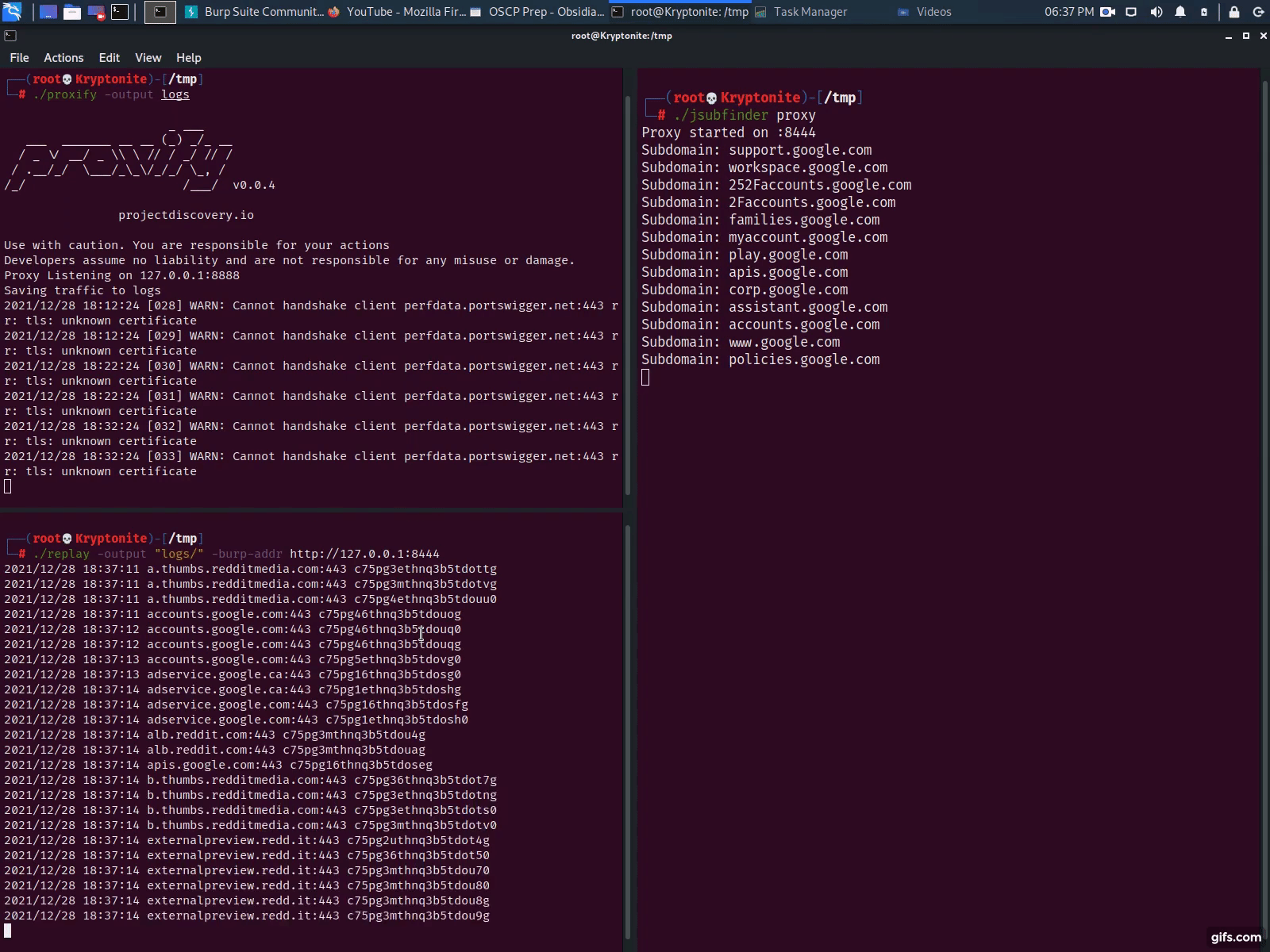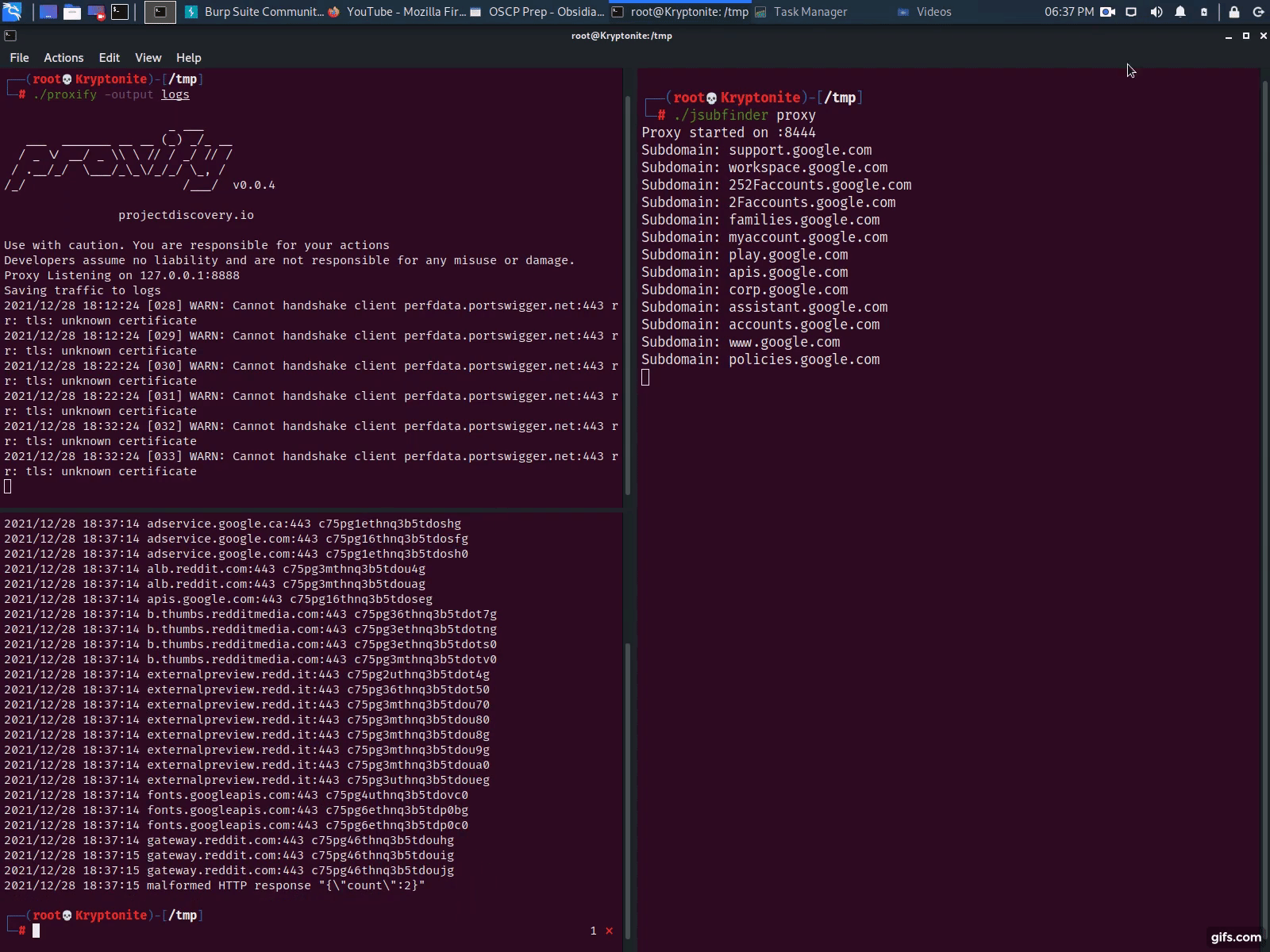
With Proxify
- Launch Proxify & dump traffic to a folder proxify -output logs
- Configure Burp Suite, a Browser or other tool to forward traffic to Proxify (see instructions on their github page)
- Launch JSubFinder in proxy mode & set the upstream proxy as Proxify jsubfinder proxy -u http://127.0.0.1:8443
- Use Proxify’s replay utility to replay the dumped traffic to jsubfinder replay -output logs -burp-addr http://127.0.0.1:8444
Run-on another server
Simple, run JSubFinder in proxy mode on another server e.g 192.168.1.2. Follow the proxy steps above but set your application upstream proxy as 192.168.1.2:8443
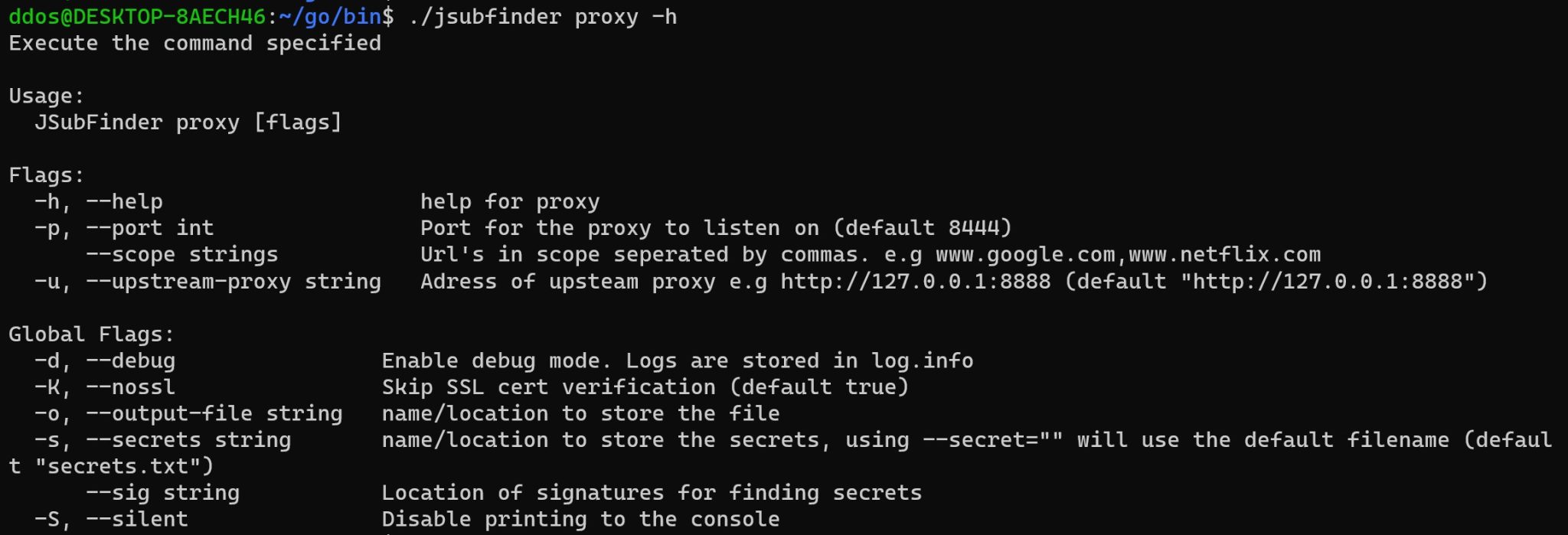
Advanced Examples
$ jsubfinder proxy –scope www.reddit.com -p 8081 -S -o jsf_reddit.txt
--scopelimits JSubFinder to only analyze responses from www.reddit.com-pport JSubFinders proxy server is running on-Ssilence output to the console/stdout-o <file>output examples to this file
Copyright (c) 2021 hiddengearz
Source: https://github.com/ThreatUnkown/