Connection diagram | Image: Kaspersky Labs
Cybersecurity researchers at Kaspersky Labs uncovered a dangerous new trojan named “SteelFox,” which has been affecting users worldwide by masquerading as popular software activators. The sophisticated crimeware combines data-stealing capabilities with cryptocurrency mining functions.
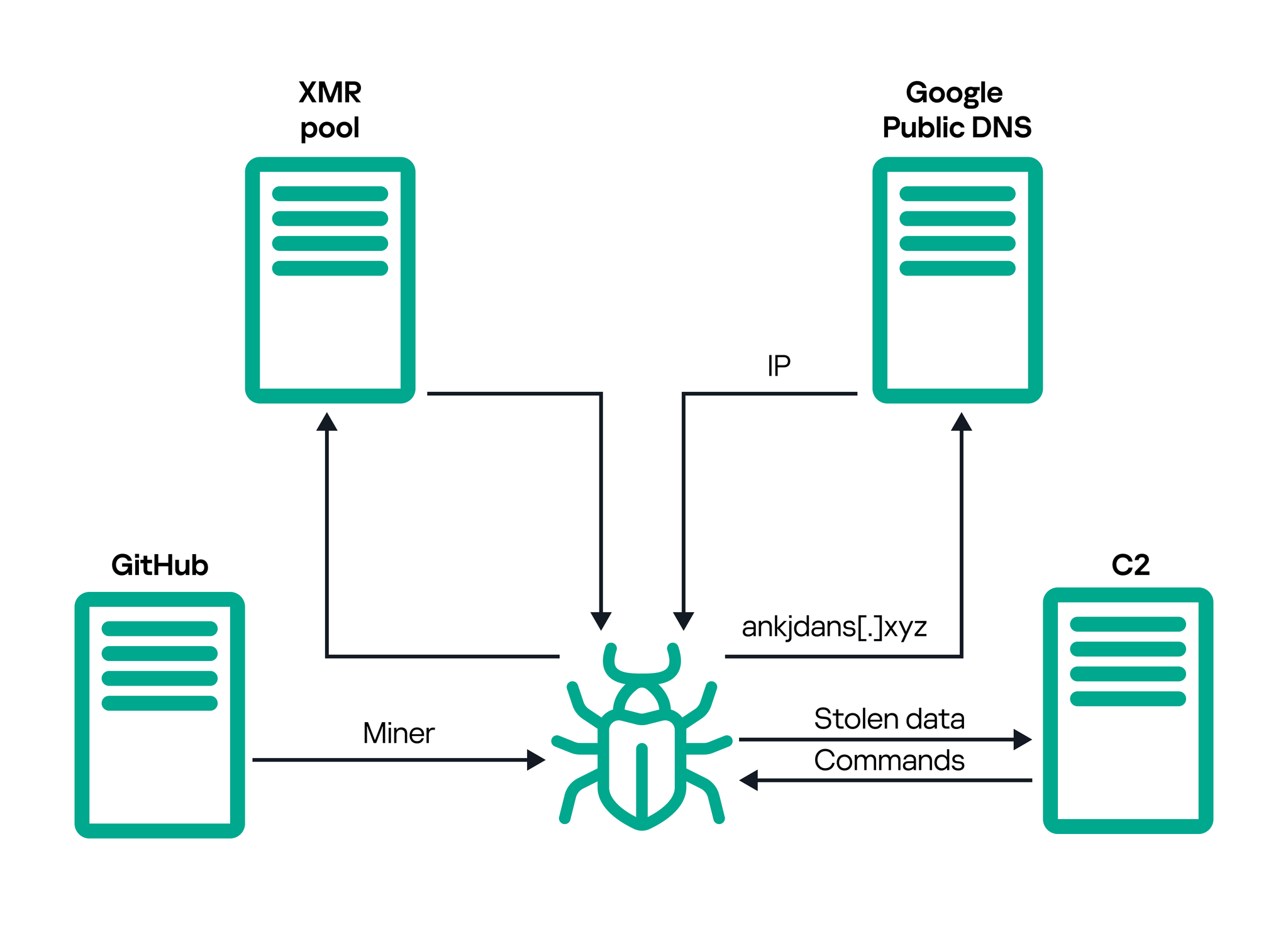
SteelFox spreads primarily through “forum posts and malicious torrents,” where it is disguised as a free software activator for well-known applications such as Foxit PDF Editor, AutoCAD, and JetBrains. Once downloaded, users are met with what appears to be a legitimate installation screen. However, as soon as the application prompts for administrator privileges, it seizes control, allowing SteelFox to install itself silently on the system. This tactic effectively exploits users seeking free software solutions, unknowingly exposing them to malware.
Kaspersky noted that SteelFox’s initial infection strategy was designed with subtlety and persistence, leveraging “shellcoding” and “malicious drivers” to gain and maintain access on the compromised device.
Upon successful installation, SteelFox initiates a sequence of actions to both collect data and set up a mining operation. The data-stealing component targets multiple browsers, including Chrome, Firefox, Opera, and Brave, extracting sensitive information like cookies, credit card details, and browsing history. It also gathers a range of system details, such as installed software, running services, and Wi-Fi network credentials, providing the attackers with a full profile of the compromised machine.
The trojan’s mining capability utilizes a modified version of XMRig, a widely known cryptocurrency mining tool. SteelFox takes advantage of an old, vulnerable driver, WinRing0.sys, allowing it to escalate privileges to the system level and mine cryptocurrency with minimal detection.
Kaspersky Labs’ report highlighted SteelFox’s advanced obfuscation techniques. The malware uses AES-128 encryption to hide its payload and dynamically changes IP addresses via Google’s DNS-over-HTTPS, ensuring the malware’s server communication remains secure and undetected. Notably, SteelFox implements SSL pinning, restricting connections to the attackers’ server only, making it nearly impossible for cybersecurity solutions to intercept or monitor its communication.
At the time of this report, SteelFox had already infected over 11,000 devices, with widespread activity in regions like Brazil, China, Russia, and Mexico. This global reach, combined with its capability to avoid detection, poses a significant risk, particularly for users of widely used applications like AutoCAD and Foxit.
Kaspersky researchers emphasized, “This campaign does not target any individuals or specific organizations. Instead, it operates on a larger scale, infecting everyone who stumbles upon the compromised software.”
To protect against threats like SteelFox, Kaspersky recommends downloading software only from trusted sources and avoiding “free” activators. Implementing updated antivirus solutions and being cautious with administrator privileges can also prevent the malware from embedding deeply within systems.
Related Posts:
- Kaspersky Report: Criminals earning millions through mining malware
- 86% of the compromised Google Cloud instances were used to perform cryptocurrency mining
- Kaspersky Report: Energy Industry becomes the largest area affected by vulnerabilities in industrial automation systems