kerbrute v1.0.3 releases: perform Kerberos pre-auth bruteforcing
Kerbrute
A tool to quickly bruteforce and enumerate valid Active Directory accounts through Kerberos Pre-Authentication.
This tool grew out of some bash scripts I wrote a few years ago to perform bruteforcing using the Heimdal Kerberos client from Linux. I wanted something that didn’t require privileges to install a Kerberos client, and when I found the amazing pure Go implementation of Kerberos gokrb5, I decided to finally learn Go and write this.
Bruteforcing Windows passwords with Kerberos is much faster than any other approach I know of, and potentially stealthier since pre-authentication failures do not trigger that “traditional” An account failed to log on event 4625. With Kerberos, you can validate a username or test a login by only sending one UDP frame to the KDC (Domain Controller)
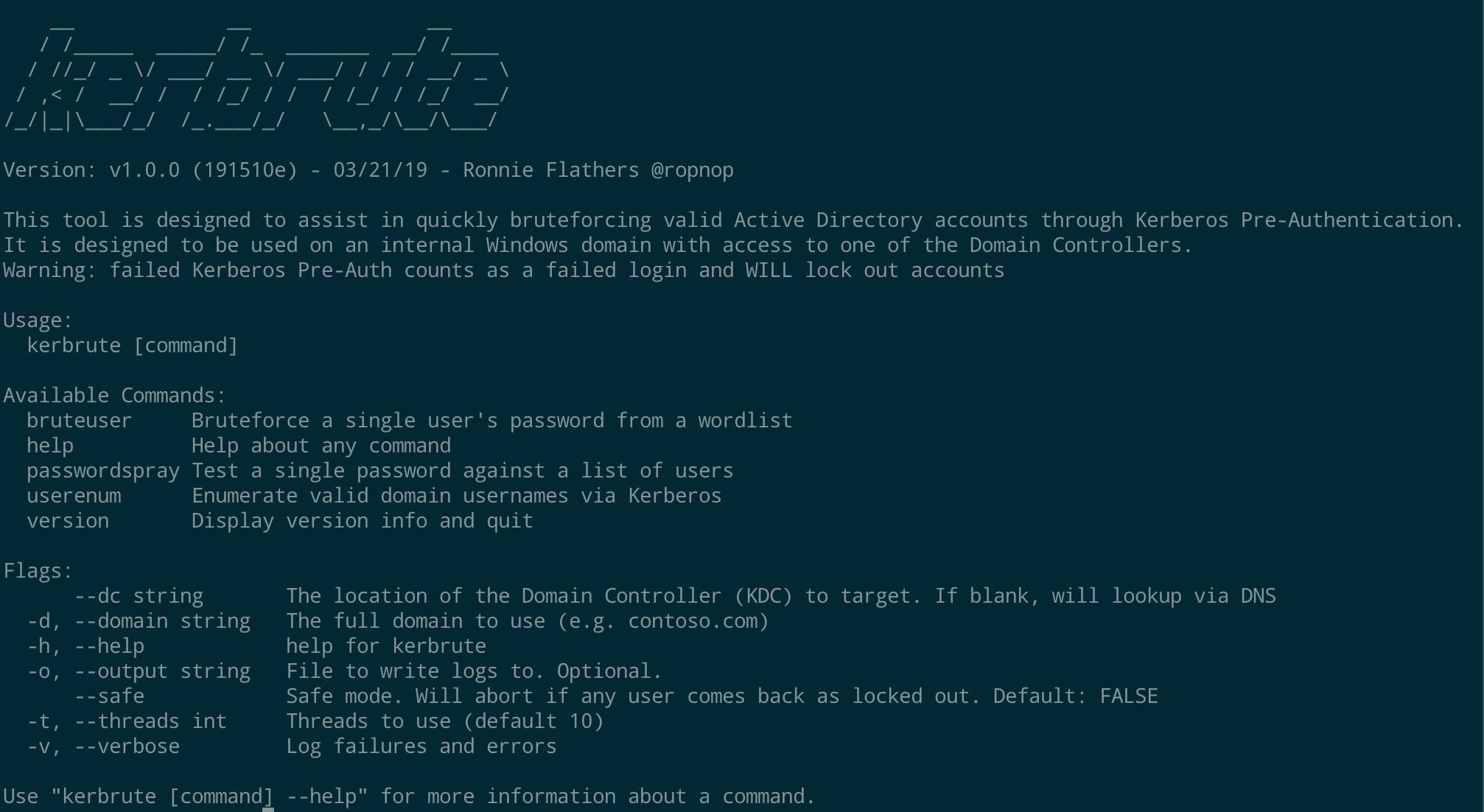
Usage

Kerbrute has three main commands:
- bruteuser – Bruteforce a single user’s password from a wordlist
- passwordspray – Test a single password against a list of users
- usernenum – Enumerate valid domain usernames via Kerberos
A domain (-d) or a domain controller (--dc) must be specified. If a Domain Controller is not given the KDC will be looked up via DNS.
By default, Kerbrute is multithreaded and uses 10 threads. This can be changed with the -t option.
The output is logged to stdout, but a log file can be specified with -o.
By default, failures are not logged, but that can be changed with -v.
Lastly, Kerbrute has a --safe option. When this option is enabled, if an account comes back as locked out, it will abort all threads to stop locking out any other accounts.
User Enumeration
To enumerate usernames, Kerbrute sends TGT requests with no pre-authentication. If the KDC responds with a PRINCIPAL UNKNOWN error, the username does not exist. However, if the KDC prompts for pre-authentication, we know the username exists and we move on. This does not cause any login failures so it will not lock out any accounts. This generates a Windows event ID 4768 if Kerberos logging is enabled.
Password Spray
With passwordwpray, Kerbrute will perform a horizontal brute force attack against a list of domain users. This is useful for testing one or two common passwords when you have a large list of users. WARNING: this does will increment the failed login count and lock out accounts. This will generate both event IDs 4768 – A Kerberos authentication ticket (TGT) was requested and 4771 – Kerberos pre-authentication failed
Brute User
This is a traditional bruteforce account against a username. Only run this if you are sure there is no lockout policy! This will generate both event IDs 4768 – A Kerberos authentication ticket (TGT) was requested and 4771 – Kerberos pre-authentication failed
Download
Copyright (C) 2019 ropnop





